Geopolitical Tensions Increase Risk of DDoS Attacks Among Other Damaging Intrusions

With Ukraine moving beyond the brink of war with an official invasion by Russia underway, organizations both near and afar must brace for potential repercussions in the form of crippling cyberattacks and intrusions. Already Ukraine has been bombarded with DDoS assaults aimed at taking down government sites, communication providers, and financial institutions.
This type of activity is reminiscent of previous DDoS attacks associated with prior Russian disputes and military activities (Estonia 2007, Georgia 2008, Crimea 2014). It is notable that this is not the first time Ukrainian websites have been targeted with alleged Russian DDoS attacks.
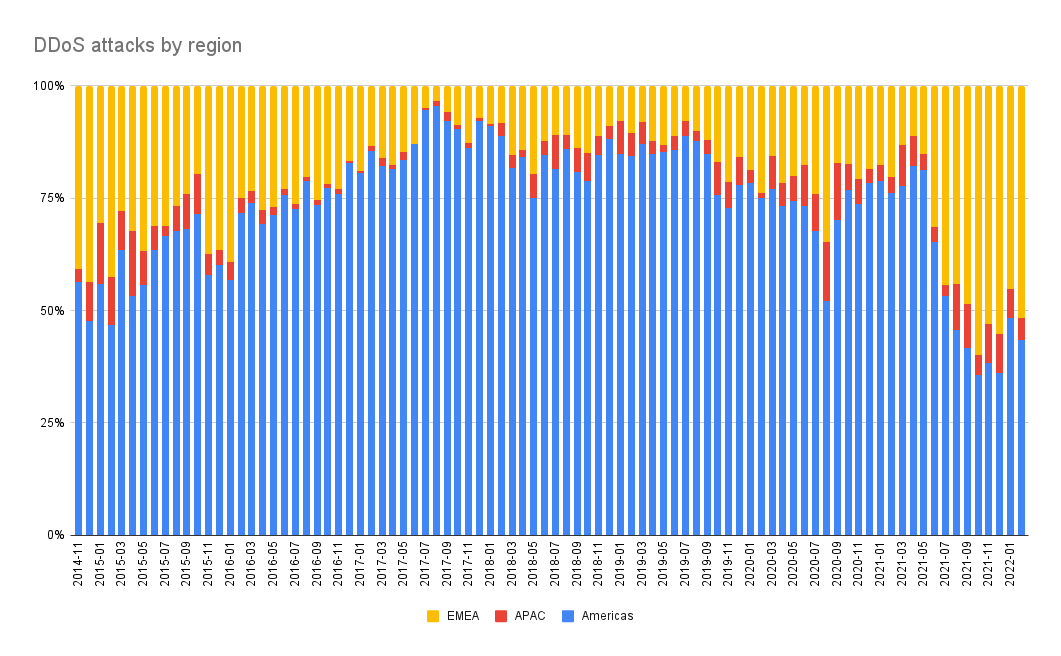
The specific surge in European DDoS activity as tensions escalated has been reflected in our data since fall 2021, with total EMEA (Europe, Middle East, and Africa) attacks up 220% over the average of the previous four years. As of yesterday, we’ve even executed an emergency DDoS protection for a new customer in Eastern Europe impacted by increased DDoS attacker activity across the region.
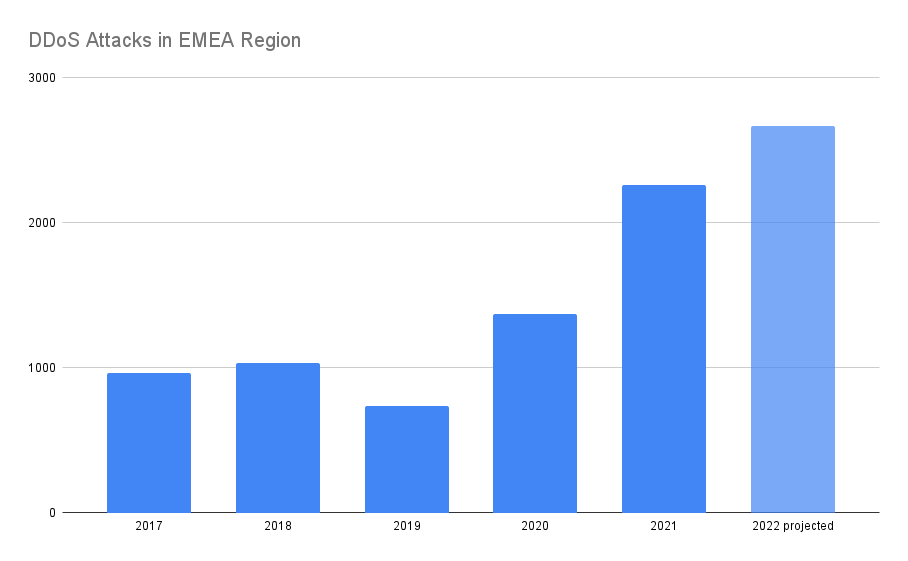
Projections based on year-to-date attacks forecast continued growth in 2022.
This massive growth in EMEA DDoS activity is largely directed at Europe, accounting for over 50% of all attacks seen on the Akamai Prolexic mitigation platform.
Current reports also indicate that HermeticWiper, highly destructive malware designed to make PCs inoperable, is actively targeting Ukrainian systems. In the wake of what is currently unfolding, businesses should reassess defensive postures and prioritize locking down attack surfaces, to better maintain operational readiness and business continuity.
While the full cyber ramifications of the Ukraine invasion and associated sanctions have yet to unfold, there are key steps that you should be thinking about right now to protect uptime of internet-facing infrastructure against DDoS attacks and the spread of malware across critical systems and networks.
Recommendations for Maintaining Operational Readiness in the Face of Elevated Risk
To bolster defenses to mitigate the risk of DDoS-associated downtime, consider doing the following:
Immediately review and implement CISA recommendations* — see complete list of links below.
Review critical subnets and IP spaces, and ensure that they have mitigation controls in place.
Deploy DDoS security controls in an “always-on” mitigation posture as a first layer of defense, to avoid an emergency integration scenario and to reduce the burden on incident responders. If you don’t have a trusted and proven cloud-based provider, get one now.
Proactively pull together a crisis response team and ensure runbooks and incident response plans are up to date. For example, do you have a runbook to deal with catastrophic events? Are the contacts within the playbooks updated? A playbook that references outdated tech assets or people that have long left the company isn’t going to help.
To help stop the spread of a malware infection, consider doing the following:
Patch everything that needs a patch. Don’t wait. If you can’t patch due to logistical reasons, then selective WAF rules can temporarily assist and buy some time.
Backups. Do you have them? You should. Do they work? Test them. Most ransomware attacks go from bad to worse because the backups were flawed.
Segmentation is one of the most important steps you can take to improve your cyber resilience, as well as prevent the spread of malware (i.e., ransomware). In addition, implement MFA across the enterprise for layers of defense.
Explore custom WAF rules to match on certain geographic attributes to help reduce malicious traffic from unwanted geographies.
Akamai’s thoughts are with all the Ukrainian citizens and residents. Our security and network teams are closely monitoring potential cyber threats arising from these geopolitical events, and we will continue taking the appropriate measures to ensure the integrity of Akamai systems and the Akamai network to help keep our customers protected during this time of increased risk.
* For additional information on the steps you can take to protect your organization, please visit the CISA resources below:
Understanding and Mitigating Russian State-Sponsored Cyber Threats to U.S. Critical Infrastructure
CISA Insights: Preparing for and Mitigating Foreign Influence Operations Targeting Critical Infrastructure
Proactive Preparation and Hardening to Protect Against Destructive Attacks



