The Increased Use of Mobile Devices Expands the Threat Landscape

Business trends are driving greater use of mobile and Internet of Things (IoT) devices, creating new threat exposures for IT teams. Mobile network operators (MNOs) are in a unique position to help organizations maximize their investment in IT security by extending security policies to all their mobile and IoT devices and improving the visibility of mobile traffic.
Digital transformation and adapting to remote work models are two of today’s major business trends. The McKinsey Global Institute analyzed work trends across eight countries with diverse economies and labor markets that account for nearly half the world’s population and more than 60% of the world’s GDP.
They concluded that remote work will continue, although likely less than during the COVID-19 pandemic. Digital commerce, telemedicine, online banking, and streaming entertainment will grow strongly, as will digitization of delivery, transportation, and warehouse jobs.
Increasing mobile device dependency
Businesses are increasingly depending on mobile devices since digital transformation, remote work, and phones go hand-in-hand. According to a survey of mobile security professionals in the Mobile Security Index 2022 report published by Verizon:
53% of respondents said mobile devices have access to more sensitive data than a year ago
58% said they have more users using mobile devices than 12 months ago
59% said mobile users are doing more with the devices than 12 months ago
The Verizon report also stated: “Many employees now have access to much of the same data — customer lists, banking details, employees’ personal data, billing information, etc. — and systems — messaging, enterprise resource planning (ERP), etc. — via their mobile devices as they would sitting at a desktop in the office.”
Creating a weak link in the security chain
More workers, phones, and data means more attractive targets, and the increased business use of mobile devices creates more risk for organizations' security postures. Mobile devices extend the organization's perimeter and can be a weak link in the security chain; they tend to be overlooked due to the perception that cellular networks are secure.
Cellular networks themselves are highly secure, but when phones access the internet they’re exposed to threats like phishing and other malicious activity.
Akamai mobile DNS threat data
Mobile operating system distribution
The data in this blog post is based on Akamai’s visibility into mobile DNS traffic. The data is for the year starting in Q2 2022 and ending in Q1 2023. Of the mobile devices that Akamai saw, 57% use iOS and 43% use the Android operating system (Figure 1). Since there are negligible numbers of devices not using Android or iOS, these devices were not included in the presented data.
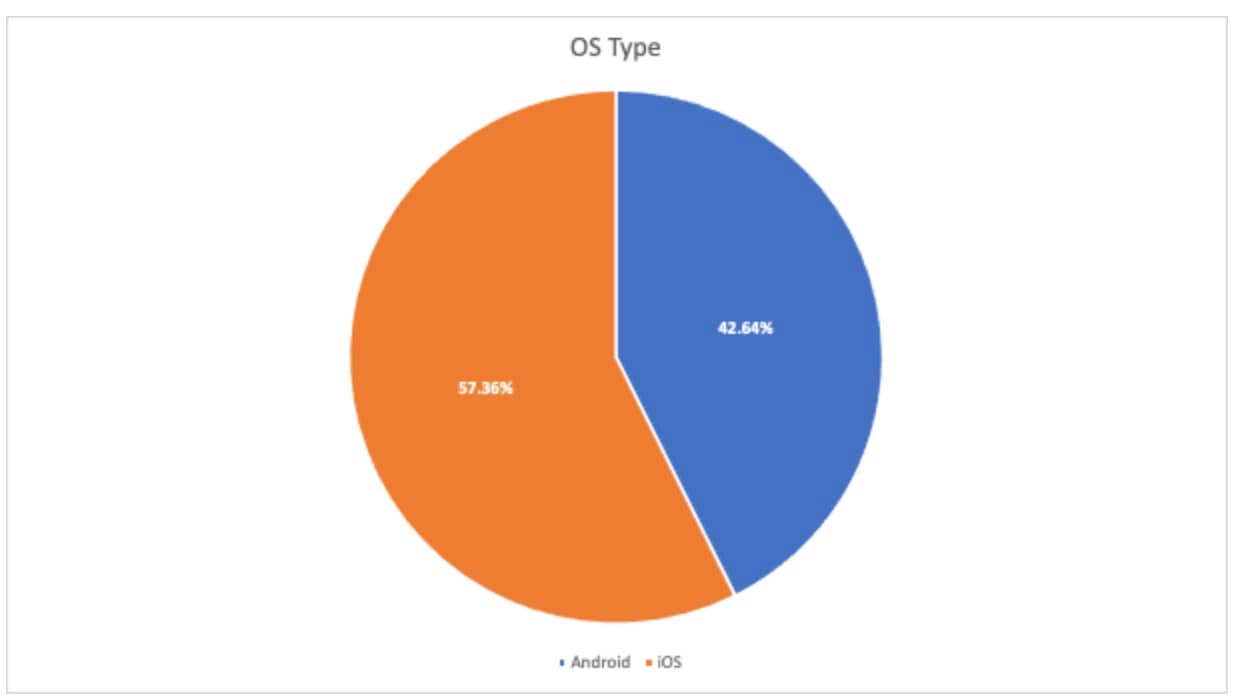 Fig. 1: Mobile operating system device distribution
Fig. 1: Mobile operating system device distribution
Combined device exposure
Figure 2 shows that nearly 1 in 10 monitored devices, on average, attempted to reach out to domains associated with either malware, phishing, or command and control (C2) in the past year.
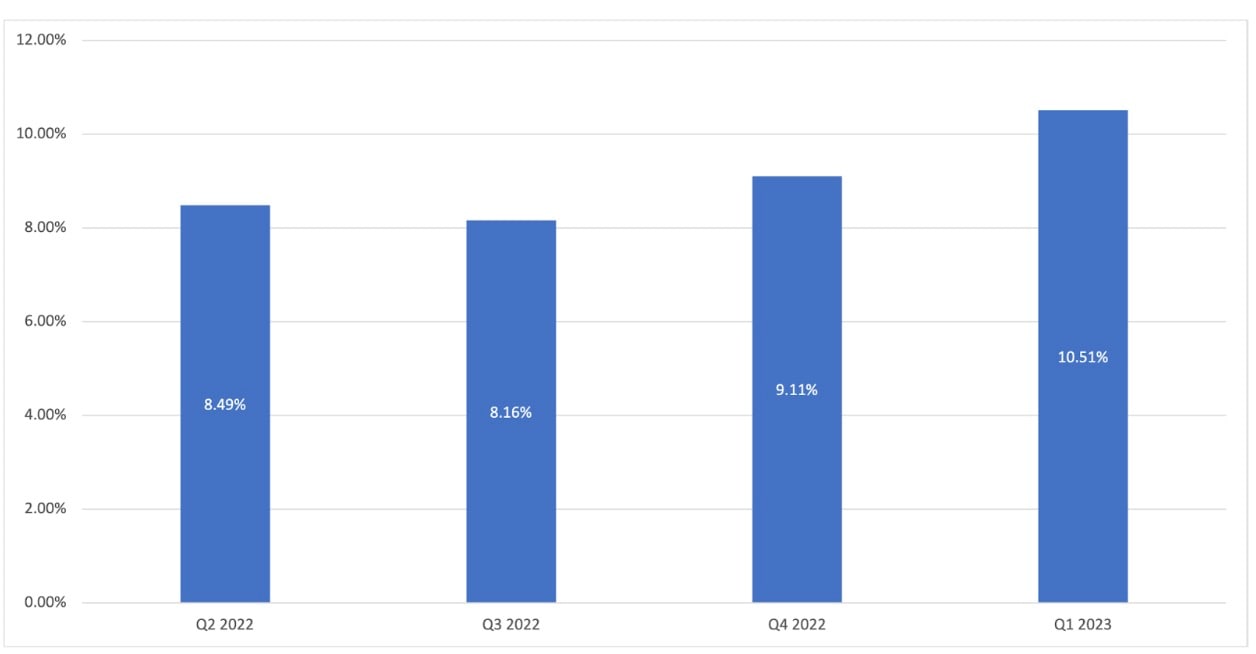 Fig. 2: Combined device exposure to malware, phishing, or C2
Fig. 2: Combined device exposure to malware, phishing, or C2
Over the year, there was also an increasing trend in devices’ exposure to any one of those three threat categories: from 8.49% in Q2 2022 to 10.51% in Q1 2023. We attribute this increase to the continued shifts of mobile devices toward multipurpose consumer and business use cases.
The primary usage of mobile devices continues to be driven by consumption of personal services, like entertainment and digital commerce, but these same devices are also being adopted for business-driven use cases; therefore it’s not surprising to see an increase in DNS activity associated with threats.
Mobile attack categories
By looking more closely at the data analysis in Q1 2023, we can see that 8.23% of devices monitored attempted to reach out at least once to domains associated with malware. In addition, 5.87% communicated with domains pertaining to phishing, and 0.65% C2 communication (Figure 3). These numbers are considered to be a significant exposure to threats and require resources from security operations if the exposures are not mitigated properly.
Attempted communication with malware-associated domains does not guarantee that the devices were actually compromised, but it provides a strong indication of increased potential risk if threats aren’t properly mitigated. Exposure to C2-associated domains, however, indicates that the devices are likely compromised and communicating with C2 servers. This may explain why the number of C2 attacks is lower than malware attacks.
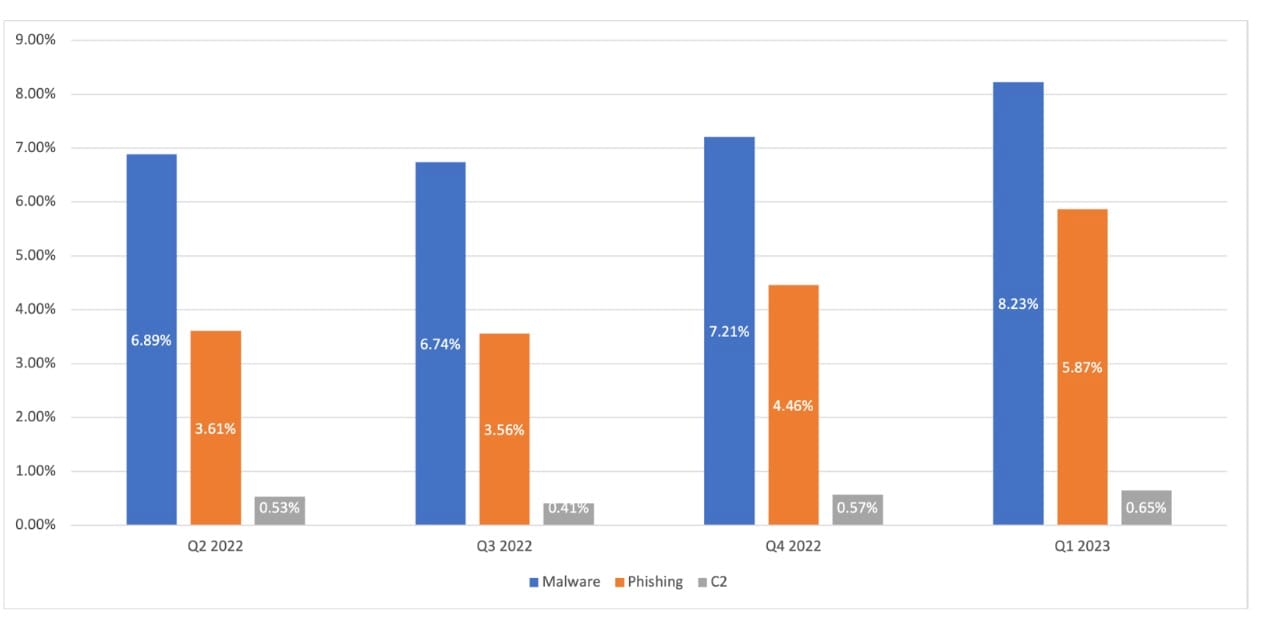 Fig. 3: Mobile threats by category over the past year
Fig. 3: Mobile threats by category over the past year
The breakdown of threat categories also shows consistent increases with malware, from 6.89% in Q2 2022 to 8.23% in Q1 2023. This breakdown correlates with the overall trend in the observed increase across threat categories. It also demonstrates, yet again, the increase in attacks and risks associated with mobile devices — and why a business’s mobile device posture should get the relevant attention.
Mobile phishing attacks
Mobile phishing data over Q1 2023 yields insights into which verticals are being abused and mimicked by phishing scams, and the total number of campaigns versus the number of victims on mobile devices (Figure 4). This kind of visibility into phishing data allows us to assess the success rate of campaigns, and separate the targeted industries on a percentage basis.
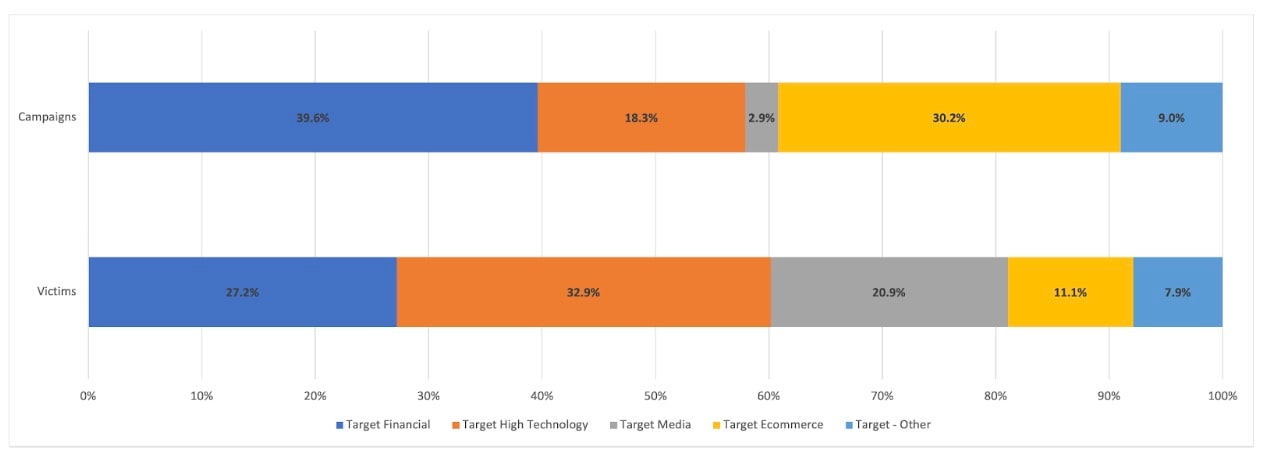 Fig. 4: Mobile phishing attack victims vs. campaigns
Fig. 4: Mobile phishing attack victims vs. campaigns
Our analysis found that financial brands had the highest number of phishing attack campaigns (39.6%), but only 27.2% of victims. High technology brands and services had the opposite trend: 18.3% of the phishing campaigns and 32.9% of the victims. This indicates that attacks against financial services were not as effective as attacks on high technology services in Q1 2023.
Akamai partners with MNOs
Business trends create exposure as mobile phones become more integral to all kinds of workflows. Akamai data shows MNOs are in a unique position to help organizations improve security and visibility of their mobile devices.
Akamai partners with MNOs to integrate technology into their networks that can help organizations protect mobile devices from exploits like phishing, malware, and botnets. Powered by Akamai threat intelligence, the services don’t require client software and they’re compatible with all SIMs and mobile OSs. IT teams can quickly provision security defenses, acceptable use policies (AUPs), and data usage controls at any scale using a self-serve portal and automated tools. Integrations with mobile device management or unified endpoint management solutions ensure consistent, unified visibility and control.




