Feature Spotlight: Kubernetes Enforcement

Kubernetes (K8s) is one of the most widely adopted technologies for deploying and managing applications in cloud environments.
According to Gartner, 90% of global organizations will be running containerized applications in production by 2026 — up from 40% in 2021"
However, K8s has one major drawback: security.
According to Red Hat’s 2022 State of Kubernetes Security Report, which surveyed more than 300 DevOps, engineering, and security professionals, 93% of respondents experienced at least one security incident in their K8s environments in the last 12 months. These incidents could potentially be exploited by adversaries to install ransomware and other types of malicious software.
Akamai recently announced new enforcement capabilities for K8s environments that provide segmentation for applications and block lateral movement to, from, and inside K8s clusters. I sat down with Omer Mayer, a product manager at Akamai, to understand more about how Akamai is implementing enforcement in K8s environments.
Why do you need segmentation in Kubernetes environments?
As the K8s cluster network is inherently flat, it allows communication between clusters and pods by default. Upon initial breach, an attacker can move laterally and gain access to all connected data centers and execute the attack (Figure 1).
In recent years, we’ve seen a sharp rise in attacks on containers. To avoid detection, attacks on K8s clusters have increased their use of evasion and obfuscation techniques, including packing the payloads, using rootkits, and running malware straight from memory. To help minimize the attack surface in K8s clusters, we need the ability to enforce strict segmentation policies.
A good segmentation policy should address two main criteria: It should be nonintrusive with performance limitations, and it should provide a flexible way to ringfence all levels of K8s objects, including namespaces, controllers and K8s labels.
What are policy enforcement challenges in Kubernetes environments?
K8s can be an overwhelming solution. It’s a complex environment, with many different resources, namespaces, and interactions between components. Because of its dynamic nature, resources are constantly being created, deleted, or updated, which makes it challenging to enforce and manage K8s network policies in real time.
One of the common challenges when dealing with K8s is the lack of visibility. Security and development teams don’t know, and therefore can’t understand, what’s going on inside the K8s cluster. To create effective policies, the teams must visualize traffic inside and outside the clusters and see the dependencies between the communications.
How does Akamai address these challenges?
Akamai Guardicore Segmentation offers a software-based segmentation solution that has dedicated support for securing K8s clusters. It's nonintrusive and built for scale and performance. The solution does not require a dedicated console nor local access to the clusters.
The solution behaves similarly for other workloads in the customer’s environment. As a result, assets can be visualized, secured, and managed across the company through a single pane of glass.This was done by introducing the representation of pods and services, and via metadata and labels that are imported from K8s to Akamai Guardicore Segmentation, which allow the user to manage the most complex environments in the same way from the same console.
How does Akamai enforce policies in Kubernetes environments?
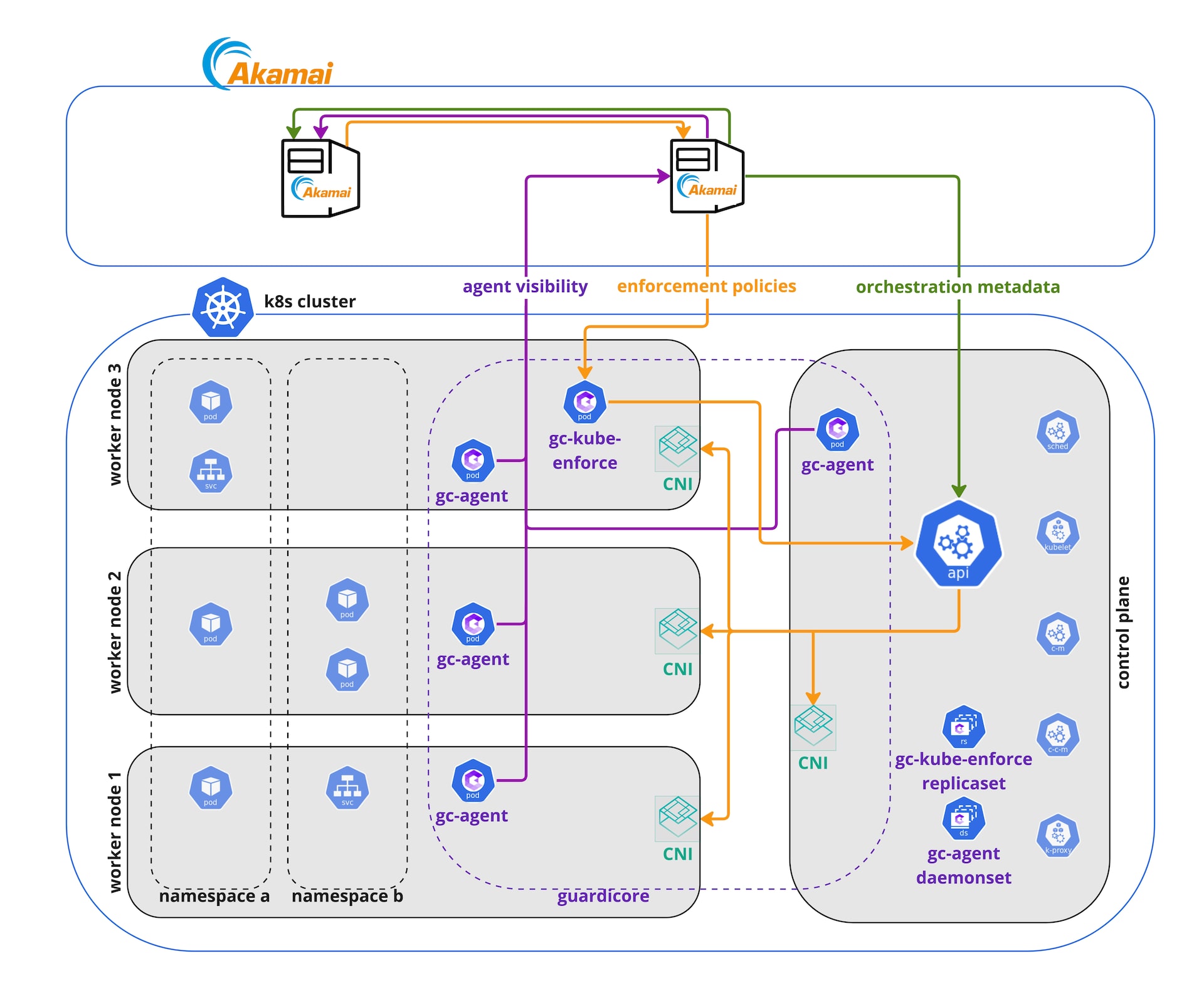
Akamai uses the K8s native way of network policy enforcement capabilities by leveraging the Container Network Interface (CNI) network policy plug-in. K8s has an out-of-the-box resource designed for network policy enforcement. This network security policy plug-in was specifically designed for network segmentation enforcement in a K8s environment.
The CNI acts as the IP address manager of the cluster — it always “knows” which pod or service has which IP address — so every connection that occurs passes through the CNI's engine. Then, each connection is immediately trafficked through to the destination pod or blocked, based on the CNI’s configuration of the IP tables and routing tables.
What makes Akamai’s way of enforcement unique?
There are two things that set apart the Akamai approach:
1. Complete visibility into K8s clusters. Because you can’t properly segment what you can’t see, the ability to know what’s running in the K8s environment and to confirm that the traffic is going only where you want it to go is critical to successful policy creation.
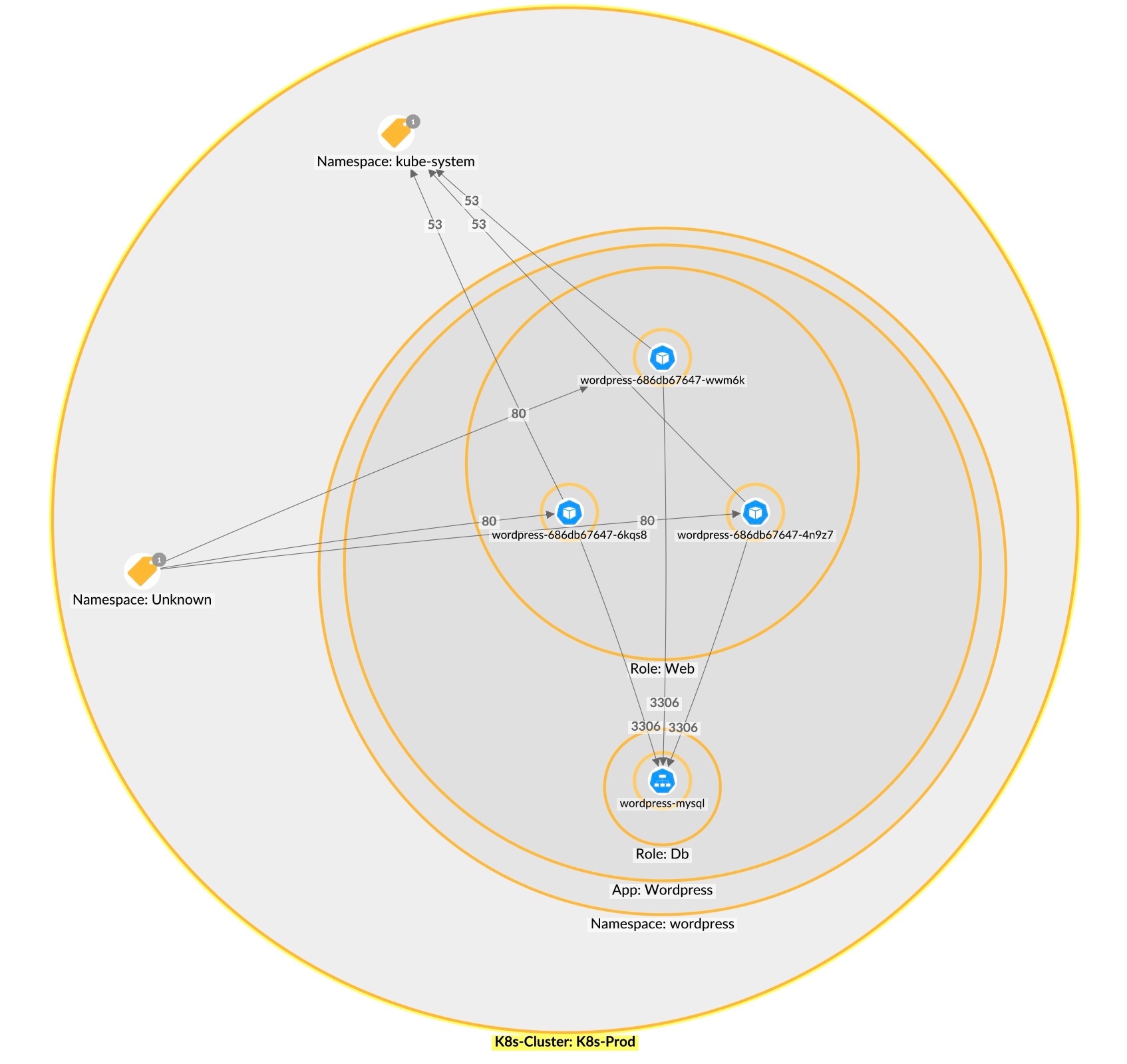
Akamai Guardicore Segmentation provides a map for visualizing communications internally and across data centers for all types of technologies, such as VMs, K8s, docker containers, and more. Customers are suddenly able to easily visualize their entire K8s environment, which greatly simplifies the creation of policies and ensures accuracy in the process.
2. Use of the K8s native way of enforcement. Akamai realized that the most intuitive, scalable, and nonintrusive way to enforce policies is to use the K8s infrastructure. K8s provides a CNI controller on every node that is responsible for the traffic of that node. It's distributed and designed to work at scale. This is the K8s native way of enforcing traffic in the cluster, and it’s the way it was designed to handle network microsegmentation.
Figure 3 shows how Akamai’s enforcement works. The policy is configured in the Akamai Guardicore Segmentation solution and then communicated to the dedicated pod in the K8s cluster, translated into the K8s network policy format and through the API, and sent over to the CNI for every relevant node.
What are some of the most common Kubernetes enforcement use cases?
The three most popular use cases we see are:
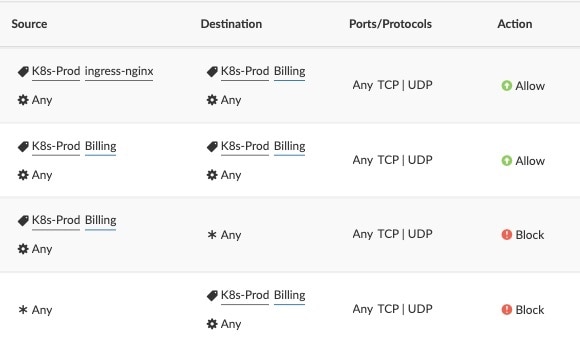
1. Application Ringfencing. Using the pod labels, customers can prevent any unwanted access to or from apps in the cluster. Ringfencing the app allows the user to prevent lateral movement to it from within the cluster or allow external ingress/egress to/from a K8s app.
2. Namespace segmentation. When there are no labels in the pods or when the level of granularity provided by labels is not necessary, it is possible to define rules for namespaces that allow or block communication between them (Figure 4).
3. Controlling K8s ingress/egress cluster traffic. This is done to prevent lateral movement from one area in the data center to the K8s cluster and vice versa. It is important to control traffic from outside the cluster to the applications inside the K8s cluster; this is done by applying microsegmentation policies, as well as by limiting access to other areas in the data center to specific K8s applications.
For example, if one of the K8s applications needs access to the PCI database, there is no reason to allow the entire cluster to have access. You’ll want to make sure that the access is granted at the granularity of the application.
How do Kubernetes labels simplify the enforcement process?
Labels are an inherently important part of any functioning K8s cluster. Because pods scale up and down regularly, their IP addresses change constantly. That's why, to apply a policy that would persist regardless of scaling, Akamai Guardicore Segmentation uses labels, instead of relying on IP addresses. It imports labels from K8s to the Akamai Guardicore Segmentation console and uses them to define the rules and policies. This way, once the user uses labels to create a rule, it is applied to all the pods that are related to this label, regardless of their IP addresses.
Akamai imports all labels in the cluster using Kubernetes Orchestration in addition to generating useful labels such as Namespaces and Cluster IDs, by querying the K8s cluster’s apiserver, and updates them regularly to reflect the cluster correctly. Akamai Guardicore Segmentation agents collect metadata on every pod on every node and report it along with the various connections that have been seen.
What can you share about the future roadmap?
We are working on supporting OpenShift and Cilium, open source platforms that provide solutions for container orchestration and network security. There is much more great stuff coming that we can’t share yet, but stay tuned for further announcements later this year!
Learn more
For more information about Akamai Guardicore Segmentation, Akamai’s segmentation solution for K8s environment, read the solution brief or talk to an expert.