CVE-2023-50387 and CVE-2023-50868 — DNS Exploit KeyTrap Posed Major Internet Threat

Security researchers discovered and contained a major vulnerability in the Domain Name System (DNS), one of the foundational components needed for the internet to function. In collaboration with the researchers, Akamai developed mitigations and issued patched versions for Akamai DNSi recursive resolvers (CacheServe, AnswerX, and Answer X Cloud and Managed solutions), which serve a very large number of internet users, in December 2023 and February 2024. Other affected Akamai products, including Enterprise Application Access and Secure Internet Access Enterprise (formerly Enterprise Threat Protector), and Secure Business Hosted were also patched.
Akamai authoritative DNS server offerings, such as Akamai Edge DNS and Global Traffic Management, are not affected by this vulnerability, nor is Shield NS53, a new cloud proxy DNS service. Customers with additional questions can open a support ticket through their regular channels.
Dubbed “KeyTrap,” this security gap could have allowed attackers to cause major disruption to the functioning of the internet, exposing one-third of DNS servers worldwide to a highly efficient denial-of-service (DoS) attack and potentially impacting more than one billion users.
KeyTrap targets DNS resolvers, exposing flaws in the DNS Security Extensions (DNSSEC) specification. Resolution of a single query can lead to CPU-intensive cryptographic calculations when a resolver attempts to verify a malicious response — a vulnerability now identified as CVE-2023-50387.
In addition, a related vulnerability in the NSEC3 proof of non-existence DNSSEC mechanism was discovered: CVE-2023-50868. Using a similar attack vector, a resolver’s CPU cycles could once again be exhausted. Either approach could cause the resolver to become unresponsive for several minutes, rendering the network it serves practically inoperable.
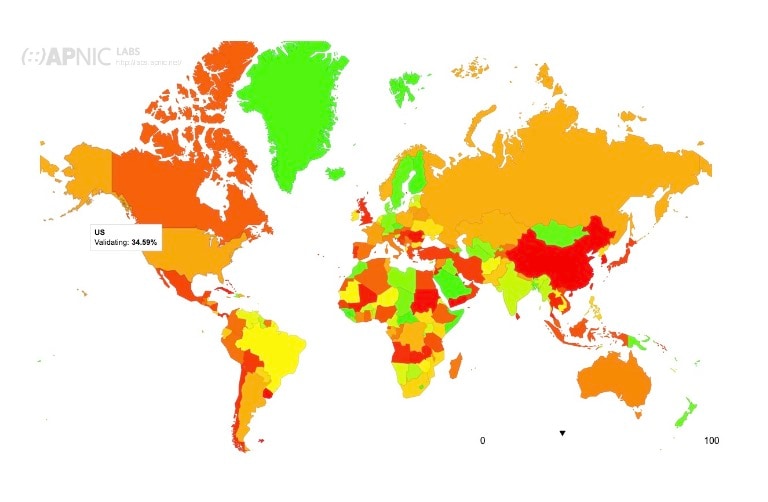
Data collected by APNIC shows that approximately 35% of internet users in the United States and 30% around the world rely on resolvers that use DNSSEC validation.
The team at ATHENE, the German National Research Center for Applied Cybersecurity for industry, society, and government, led a coordinated disclosure process. Akamai’s carrier engineering team actively participated, along with other key players in the global DNS community, in working with the researchers who discovered the vulnerability to prevent it from causing havoc.
Akamai DNSi resolvers are deployed at ISPs and mobile network operators (MNOs) that serve approximately one billion internet users in more than 60 countries. Akamai’s carrier engineering team proactively provided patches that ensure the resolvers will maintain performance levels that deliver the user experience our customers expect, even when confronted with malicious KeyTrap queries.
Many DNS software and service providers have also already published security advisories and released patched updates, and we encourage all users to check with their vendors for these updates. Because of the collaboration of the community, what could have been a damaging exploit has already been mitigated.
Akamai would like to thank Elias Heftrig, Haya Schulmann, Niklas Vogel, and Michael Waidner from the German National Research Center for Applied Cybersecurity (ATHENE) for finding and coordinating the disclosure of this vulnerability.