Akamai Blog | DNS Cybersquatting: The Case for Edge DNS Zone Protect

Cybersquatting, also known as domain squatting, is a type of scam that mimics a brand's domain to confuse potential victims and gain their trust. According to Revision Legal, “Cybersquatting is prohibited in the U.S. by federal law under the Anticybersquatting Consumer Protection Act (ACPA.)” These fake domains can be used in cyberattacks — especially phishing attacks.
Cybersquatting can take different forms. For example, attackers could use the domain bank[.]co. to mimic bank[.]com., including making the website look the same. There are other variations on this type of scam as well.
1. Typosquatting — This approach is characterized by mimicking a branded domain and adding a small typo to the URL. So, domain[.]com with typosquatting, could become:
Domein[.]com — a common misspelling, or foreign language spelling
Domian[.]com — a common typo
Domains[.]com — Phrasing the domain differently (pluralized in this example)
Domain[.]net — a different top-level domain (TLD)
wwwdomain[.]com — another common typo: missing the dot after www
Do-main[.]com — adding or omitting a hyphen
2. Combosquatting — This tactic is characterized by adding a phrase to a popular trademark using the second-level domain, such as domainchangepassword[.]com or domainsecurity[.]com
3. Levelsquatting — Here, the domain is converted to be the third or fourth level of other domains (e.g. domain[.]com[.]test[.]biz). Users might think they are on domain[.]com, but are on another domain entirely.
4. Bitsquatting — With this approach, the domain is one bit different from a popular domain. Thus, doeain[.]com instead of domain[.]com. This method is similar to typosquatting, when only one character has changed, but the difference is that the attackers rely on a bit-flip that could occur during a DNS request, instead of a user’s mistake.
5. Internationalized Domain Name (IDN) Homograph — Using similar-looking characters from languages such as Greek or Latin, such as domáin[.]com instead of domain[.]com.
6. Soundsquatting — Using homophones, words that sound the same, or can be spelled incorrectly. For example, if the actual domain is domainforus[.]com, a criminal will use domain4us[.]com.
Akamai has extensive visibility into DNS and HTTP traffic worldwide. Using this to our advantage, we can see which industries are most impacted by cybersquatting, the methods used, and geolocated trends.
To showcase some interesting statistics about cybersquatting in the wild, we’ve analyzed 48 domains — eight from each vertical — ranked at the top of SimilarWeb's website rankings.
For this analysis, we separated the domains into six verticals, each containing eight different brands worldwide. The verticals used in our research were:
Television, movies, and streaming
Social networks and online communities
Marketplace
Finance
Air travel and car rental
Fashion and apparel
Using our algorithm, we created a list of potential squatted domains and the matching squat type; we then looked for active cybersquatting domains.
The results returned thousands of potentially cybersquatted domains. After some work to reduce false-positive results, like squatted domains that were registered by actual brands to protect themselves, we were left with a total of 120,000 domains across 47 brands, including 5 cybersquatting variations.
SimilarWeb verticals and cybersquatting connection
Figure 1 shows the fully qualified domain names (FQDN) in traffic by vertical. The data shows that no vertical is ignored by criminals.
From the number of active domains on SimilarWeb, we can say that the most squatted verticals, within the six that were tested, are finance and air travel and car rental (with more than 25,000 squatted domains for each in the last week). It's likely they were the top targeted verticals because of the amount of valuable personal information that can be obtained from victims targeted by the scams using these fraudulent domains.
 Fig. 1: Unique FQDNs in traffic by SimilarWeb vertical
Fig. 1: Unique FQDNs in traffic by SimilarWeb vertical
Squat types in the wild
Knowledge of the types of squatting in the active domains, combined with our far-reaching visibility, allows us to predict which method will most likely be used in the wild. In Figure 2, the most noticeable type of domain squatting is IDN homograph, active in 71% of the domains observed.
The second most common type is combosquatting (26%), which isn't surprising given that there are a number of fake domains that can be generated for a common brand. In Figure 3, we've plotted the active domains in our threat intelligence and found that 86% of them were combosquatting, indicating that our algorithm does in fact detect malicious domains — even with an overly broad rule, such as *brand.*
 Fig. 2: Unique FQDNs by squat type
Fig. 2: Unique FQDNs by squat type
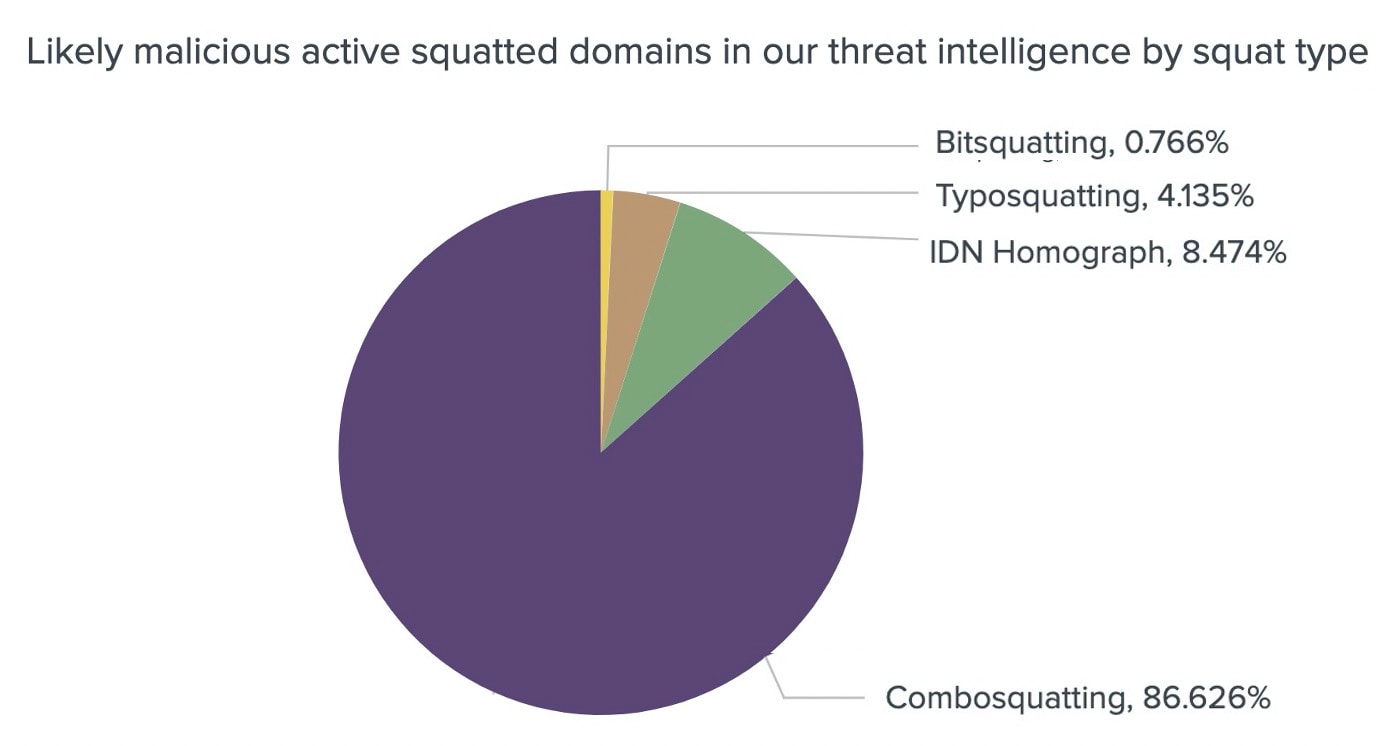 Fig. 3: Unique FQDNs in our threat intelligence by squat type
Fig. 3: Unique FQDNs in our threat intelligence by squat type
Popular cybersquatting and geographical connections
Using Akamai's global visibility into the internet, we can reliably identify geographical trends and observe the interrelation among users visiting specific verticals and scam pages in their area.
In Figure 4, we see that the geolocation of users visiting active domains does not show a strong connection between region and industry vertical. For a strong connection, we would expect to see more than 50% of the users querying active domains from a specific geolocation for all verticals; instead, we see that the percentages are low, so there is no specific geolocation in which most of the querying users are located.
 Fig. 4: Geolocation of users querying active domains by SimilarWeb category (countries with more than 1% of data)
Fig. 4: Geolocation of users querying active domains by SimilarWeb category (countries with more than 1% of data)
In Figure 5, we see the percentage of active domains’ squat type by queried users and geolocation. The data shows that, while the IDN homograph was the top active scam type (Figure 2), there weren't a lot of users visiting these domains compared with domains using combosquatting.
We can see that the percentages of purple sections in Figure 5, which represent combosquatting, are more than 50% of all active domains queried by users; thus, combosquatting is the most queried squat type by geolocation, which is similar to what we saw in Figure 3.
 Fig. 5: Squat type of users querying active domains by geolocation
Fig. 5: Squat type of users querying active domains by geolocation
Conclusion
Akamai has seen squatted domains in the wild, using different methods to mimic known brands. The most noticeable type of domain squatting is IDN homograph, but most victims are lured by combosquatting domains. We know that brands usually defend themselves by registering domains similar to their own domains, but there are too many variables at play, which is why criminals leverage combosquatting so frequently.
One of the best ways to avoid these types of scams is to look at the URL and ask yourself: “Does it look suspicious?” If it does, that could indicate a problem. Domains like those covered in this post are often associated with phishing attacks, so the awareness training that many of us get at work will help identify and avoid many of these harmful domains.
Sources
https://en.wikipedia.org/wiki/Cybersquatting
https://www.securitee.org/files/bitsquatting_www2013.pdf
https://unit42.paloaltonetworks.com/cybersquatting/
https://blog.avast.com/how-to-identify-an-online-scam
https://blogs.akamai.com/sitr/2020/05/watch-your-step-the-prevalence-of-idn-homograph-attacks.html
https://wccftech.com/combosquatting-trick-users-trust-malicious-urls/
https://en.wikipedia.org/wiki/Typosquatting
https://snapshotinteractive.com/why-cybersquatting-is-actually-illegal/
https://revisionlegal.com/copyright/copyright-infringement/an-overview-of-cybersquatting-laws/



