Digging Deeper – An In-Depth Analysis of a Fast Flux Network

Introduction
Recently, we have seen large-scale botnets used to execute attacks rarely seen in the past. These botnets incorporate new features and have bigger capabilities. How do these botnets remain resilient to detection?
Fast Flux is a DNS technique used by botnets to hide various types of malicious activities, such as phishing, web proxying, malware delivery, and malware communication, behind an ever-changing network of compromised hosts acting as proxies. The Fast Flux network concept was first introduced in 2006, with the emergence of Storm Worm malware variants. The Fast Flux network is typically used to make the communication between malware and its command and control (C2) server more resistant to discovery. Akamai’s research team has analyzed sophisticated botnet infrastructure that leverages Fast Flux techniques including domains, nameservers, and IP address changes. Figure 1 shows an overview of such a network, which can also be referred to as a form of bulletproof hosting, that hosts various malicious services. These networks empower threat actors to execute attack campaigns by utilizing network capabilities to host malware binaries, proxy communication to C2 servers, phishing websites, or proxy attacks on websites across the internet.
Akamai’s high visibility to both web and enterprise traffic gives us the ability to get new and unique insights on the behavior of such Fast Flux networks.
According to our research, we were able to track a botnet that is using Fast Flux techniques with more than 14,000 IP addresses associated with it, with most of the IP addresses originating from eastern Europe. Some of the associated IP addresses are in address space that is assigned to Fortune 100 companies. These addresses are most likely used by the Fast Flux network owner as spoofed entities and are not genuine members of the Fast Flux network. This allows the botnet to inherit the reputation of the Fortune 100 companies.
This research includes an in-depth analysis of the discovered Fast Flux network, and presents:
How network fluxing is using domains, IP addresses, and even nameservers to become resistant to discovery
How a Fast Flux network is being segregated to different subnetworks based on the offered malicious service
How the analyzed Fast Flux network offers services such as malware communication (proxying) and hosting malware binaries, websites that sell various stolen credentials, and phishing websites
How web attacks such as web scraping and credential abuse go through the Fast Flux network
How to detect and defend against such networks
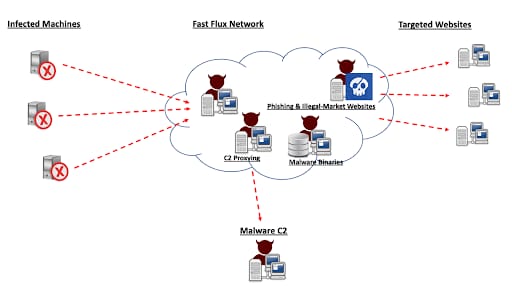 Figure 1: High-level architecture overview of the Fast Flux network and associated threat landscape
Figure 1: High-level architecture overview of the Fast Flux network and associated threat landscape
Fast Flux network — overview
While analyzing DNS communication to suspicious domains, Akamai’s Cloud Security Intelligence (CSI) platform collected data that allowed our team to identify a large-scale Fast Flux network with more than 14,000 associated IP addresses.
To better detect and track such networks, we performed an in-depth analysis:
Across various data sources, including web and DNS traffic, passive DNS, WHOIS history, Shodan.io, and malware analysis
Using data science tools and techniques such as network graphs, similarity learning, and heatmaps
To understand the boundaries and relations between the network entities, an undirected network graph was created (Figure 2). The graph represents the following entities and relations between them: domains (shown in red), IP addresses (purple), and nameservers (green). The inspected network is composed of two subnetworks sharing a strong relation. These subnetworks are connected based on the similarity between their shared IP addresses associated with different nameservers.
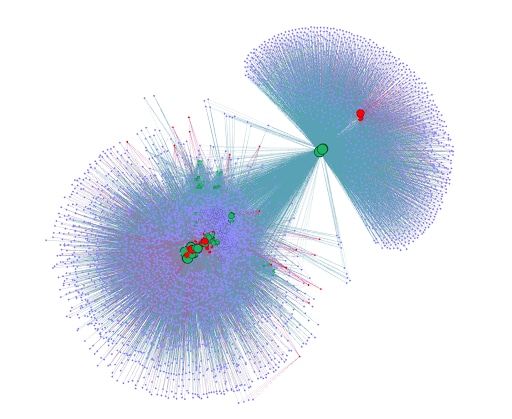 Figure 2: Graph network of Fast Flux domains, associated IP addresses, and associated nameservers
Figure 2: Graph network of Fast Flux domains, associated IP addresses, and associated nameservers
Fluxing — deep dive
The primary characteristic of the Fast Flux network is that the network constantly changes its domains, IP addresses, and nameservers. These changes obfuscate the true nature of the network and make it more difficult for researchers to understand and defend against.
IP addresses
Looking at the amount of IP addresses associated with the Fast Flux network over time, we observed a rapid change in the involved IP addresses. This behavior is also known as “single-flux,” where multiple individual nodes within the network register and de-register their addresses for a single DNS name. Figure 3 shows the number of IP addresses involved with the observed network daily from May 24, 2017, until June 17, 2017.
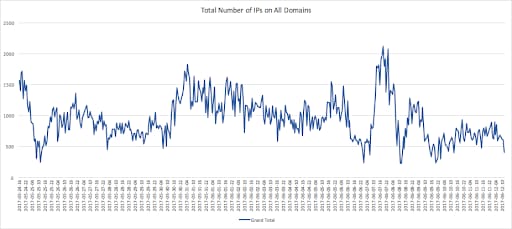 Figure 3: Number of associated IP addresses to Fast Flux network per day over time
Figure 3: Number of associated IP addresses to Fast Flux network per day over time
Monitoring the Fast Flux network IP addresses rotation (by analyzing a collection of four snapshots that each represent a week of the network and the associated IP addresses) shows that an average of 75% of network IP addresses changed between snapshots. When comparing the first snapshot and the fourth snapshot, we can see that only 19% of the associated IP addresses remained the same.
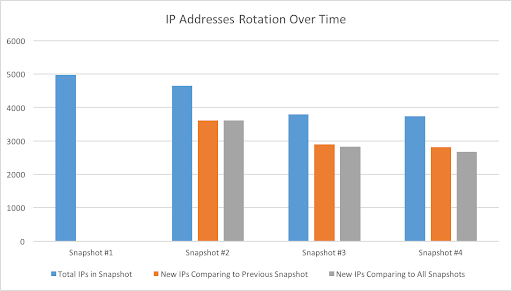 Figure 4: IP addresses rotation over time
Figure 4: IP addresses rotation over time
Domains
Examining IP fluxing over time, we observed some domains alternated between active and inactive mode (a domain was considered inactive if its DNS queries received a NXDOMAIN response, indicating “non-existing domain”). The Fast Flux network activated a domain for a limited time frame, making sure that by the time the malicious activity related to that domain was spotted, a new domain could take place, and as a result, network services remained intact.
This behavior is also known as “double-flux,” where multiple nodes within the network register and de-register their addresses as part of the DNS nameserver and the related domain name. This provides an additional layer of redundancy and survivability within the network. Following the DNS “trail” and shutting down servers used by the botnet don’t put an end to the larger botnet.
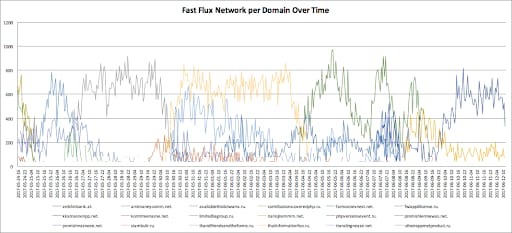 Figure 5: Number of associated IP addresses per domain (Fast Flux network domains) per day over time
Figure 5: Number of associated IP addresses per domain (Fast Flux network domains) per day over time
Nameservers
We were able to see more than 15 nameservers, most registered by different entities, associated with the Fast Flux network. Over time, we observed changes in the nameserver in use, as new servers were rotated into usage. We attribute this behavior to the Fast Flux network’s need to be resilient to detection, making the nameserver an entity that is constantly changing and therefore hard to track.
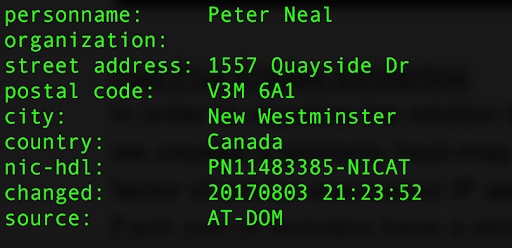
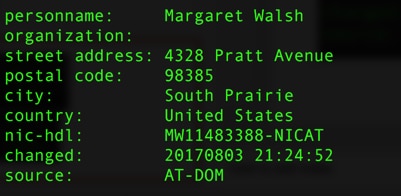
Figure 6: Example for the two Fast Flux network nameservers’ registrant personal information
The analysis of the Fast Flux network begins with the assumption that the botnet is malicious. The nameservers’ registrant personal information (Figure 6) shows what are most likely fake identities for the alleged owners of the nameservers. When we look at the similarity between those nameservers in terms of associated IP addresses later in this post, we can see evidence that those nameservers are strongly related. Looking at the registrant personal information, we can see that someone took the time to register those nameservers with different fake names that were associated with different countries to make them look unrelated; however, as our research above shows, these domains are strongly related.
Another indication of authenticity for the nameserver can be found in the history of the nameservers, most of which were recently registered, indicating an emerging activity. The usage of fake identities is another technique being used by Fast Flux network owners to make nameservers look legitimate.
Fast Flux domains and nameserver correlation
To visualize the strength of relationships between different domains hosted on the Fast Flux network, we created a heat map to highlight the correlations between different domains. Similarity is being represented as a factor of similar associated IP addresses of each pair of domains.
Each pair of domains has a similarity value, ranging from 0 to 1. The value of 1 represents a perfect match (i.e., the set of associated IP addresses of the first domain contains the set of IP addresses of the second domain). The heat map below is assigned with a darker blue color as the similarity value gets closer to 1.
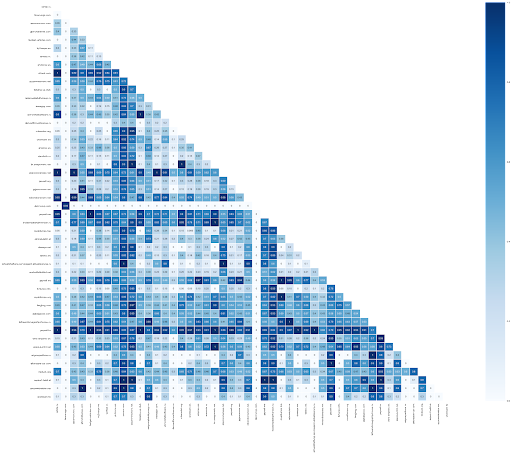 Figure 7: Similarity heat map between different domains
Figure 7: Similarity heat map between different domains
A similar heat map was also created for nameservers hosting all the domains in the Fast Flux network. For example, nameservers such as “klyatiemoskali{.}at” show a strong correlation with “cobby{.}at” with a similarity rate of 0.75.
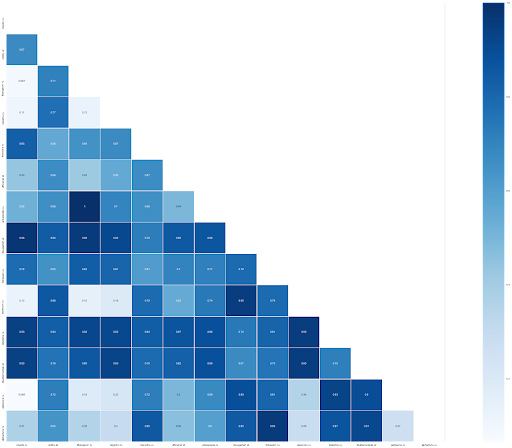 Figure 8: Similarity heat map between different nameservers
Figure 8: Similarity heat map between different nameservers
On the heat maps, we can see that many paired domains and nameservers have a strong relation between them. This strengthens our suspicion of the existence of fluxing behavior, where a network of compromised machines is being activated by reallocation of resources (represented as IP address) to new domains and nameservers rapidly.
Fast Flux network — C2 network vs. hosting network
To further investigate the initial assumption of having two different subnetworks as observed in “Fast Flux network — overview”, we created a network graph, but this time without showing the relation to the nameserver. Doing that showed us that we can see two distinct subnetworks segregated in terms of associated IP addresses.
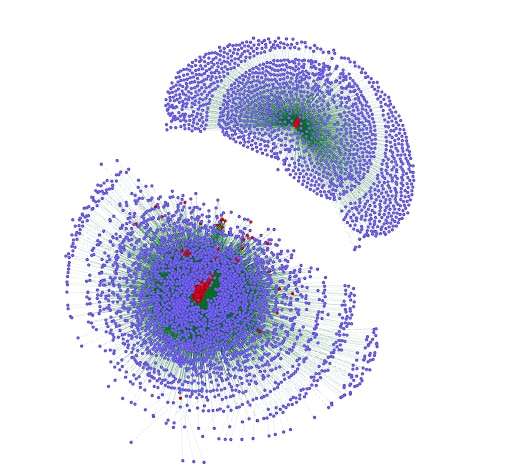 Figure 9: Graph network of Fast Flux domains and associated IP addresses
Figure 9: Graph network of Fast Flux domains and associated IP addresses
Further analysis (described in the Fast Flux network malicious activity section) of the domains that are being clustered into two different subnetworks revealed that each subnetwork offers a different type of service. On the top right side (Figure 9), we identified domains (shown in red) that are being used by malware as the communication channel to C2 servers. On the bottom left, we identified domains being used for hosting malware, phishing websites, and illegal-market websites.
Network sources behavior
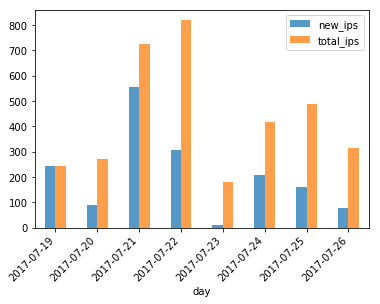 Figure 10: Associated IP addresses C2 network
Figure 10: Associated IP addresses C2 network
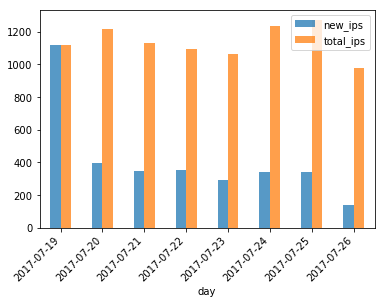 Figure 11: Associated IP addresses hosting network
Figure 11: Associated IP addresses hosting network
When looking at the IP addresses associated with each subnetwork over the time frame of one week, we can see that the C2 subnetwork is unstable (Figure 10). Both the total, as well as the new IP addresses associated with the C2 subnetwork, are constantly changing throughout the week. Looking at the hosting subnetwork (Figure 11), we can see the stability with regard to the total number of IP addresses, and the number of new IP addresses associated per day.
Network sources geographical information
When analyzing the geographical information of each network, we can see in the hosting network (Figure 12) that the top countries include Ukraine, Romania, and Russia.
Further, most of the IP addresses belong to local internet service providers (ISPs) that are typically used by household consumers and are addresses you would not expect to see hosting web services.
 Figure 12: Top 10 countries hosting network
Figure 12: Top 10 countries hosting network
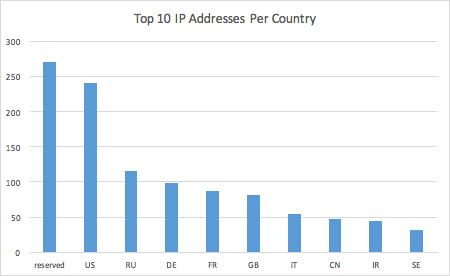 Figure 13: Top 10 countries C2 network
Figure 13: Top 10 countries C2 network
When looking at the C2 network (Figure 13), we can see the United States ranked first. The “reserved” value represents private IP addresses, which are being used only with internal websites or intranets. Analysis of the IP addresses in the United States shows that many belong to Fortune 100 companies, as well as military organizations, probably being used as fake entries on the nameserver associated with the given domains.
The Secure Internet Access Enterprise security research team suspects that these IP addresses are not compromised machines — and that the presence of these IP addresses on the nameserver can be explained as a technique being used by C2 network owners designed to inherit the reputation of the associated organizations. Inspection of such domains by law enforcement or security vendors can result in misleading conclusions on the nature of the domains and the associated IP addresses.
Network sources open ports
By looking at Shodan.io, a search engine that shares information on computers that are connected to the internet, we were able to find limited evidence of open ports on both subnetworks. In the case of the hosting network, we had information on 24% of the network IP addresses, and in the case of the C2 network, 5% of the network IP addresses. We believe that the difference in the percentage of collected ports information is related to the usage of “fake” and “reserved” IP addresses in the C2 network, as seen in the Network sources geographical information section.
While information on all botnet members’ open ports was limited, we see evidence that supports the difference between the two networks. The hosting network’s most common open ports are 80 and 443, representing the service being delivered by the network, hosting of websites, and malware binaries.
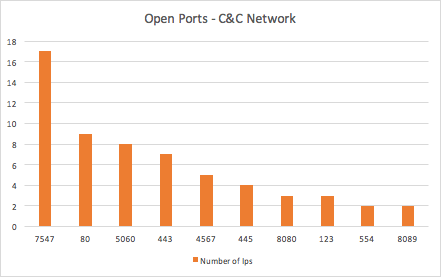 Figure 14: Top 10 most used ports C2 network
Figure 14: Top 10 most used ports C2 network
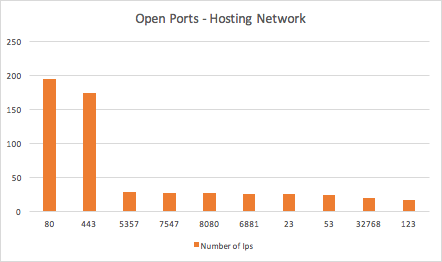 Figure 15: Top 10 most used ports hosting network
Figure 15: Top 10 most used ports hosting network
When analyzing the C2 subnetwork (Figure 14), we see that port 7547 is the most used port. This port is used mostly by routers that have a TR-069 management tool, and the usage shows how the same type of vulnerable devices are being used for the same goal. Such routers are known to be highly exploited and are probably used as infrastructure that acts as a proxy layer for the communication of the malware with its C2 server.
Fast Flux network malicious activity
Fast Flux network as a platform for malware activity
To make sure, beyond any reasonable doubt, that the Fast Flux network is being used for malicious activities, we collected evidence from a variety of public sources that shows a clear relationship between the analyzed malware samples and domains being hosted on the Fast Flux network.
Hosting malware — dropper
We were able to track down and analyze a sample of unnamed malware that is being distributed as a Word document that includes a malicious macro. Once the macro is enabled, it executes JavaScript code that accesses a domain (on the Fast Flux network) and downloads a file that contains a binary. This binary is known malware classified as a Trojan by many antivirus vendors.
We were able to see that the downloaded file (same file path) exists on several IP addresses, representing different compromised machines, also associated with the Fast Flux network.
C2
We were also able to find evidence for other malware variants that use domains associated with the Fast Flux network. Evidence from sandboxing analysis of malware samples showed us that domains that are associated with the Fast Flux network are being used as C2 servers.
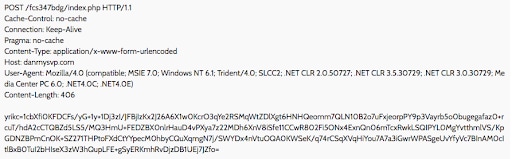 Figure 16: An example for C2 communication over HTTP (going through the C2 network)
Figure 16: An example for C2 communication over HTTP (going through the C2 network)
The HTTP request (Figure 16) shows an HTTP POST request that contains exfiltrated data (encrypted) being sent from the infected sandbox machine to a domain that is being used as the C2 server.
Fast Flux network as illegal-market websites hosting provider
We were also able to find evidence of websites whose primary purpose is to function as an illegal market being hosted on the Fast Flux network, offering merchandise such as:
Stolen credentials for popular online retail websites
Hacked credit card numbers with CVV
Professionals hackers carders forum
 Figure 17: Example of illegal-market website catalog, hosted on the hosting network
Figure 17: Example of illegal-market website catalog, hosted on the hosting network
We can see (Figure 17) that when searching Google for one of the illegal-market domains, we were able to find the offering of that website, including stolen credentials, stolen credit cards, and spamming services.
To evaluate the similarity between hosting illegal-market domains and hosting malware domains, we measured the similarity between the domain that was used for selling credit cards and a domain that was being used to deliver malware binaries. The results revealed a 50% similarity rate between the domains. This is more evidence that strengthens the relationship between the different domains being used for different services, and shows that the Fast Flux network is being used as a collection of malicious services.
Fast Flux network as phishing hosting provider
We were also able to see some domains being hosted on the Fast Flux network that look like part of a phishing campaign. One was a domain starting with a prefix of a well-known ecommerce travel service. Such social engineering techniques are used to give spammed victims the feeling of confidence when recognizing a company as part of the domain name, while in practice the primary domain is not related to the ecommerce company.
Fast Flux network — web attacks
Akamai’s position as a content delivery network (CDN) gave us visibility into web attack traffic going out of the Fast Flux network, targeting Akamai’s customers.
We assume that several infected machines in the Fast Flux network serve a dual purpose. Not only do they act as servers, they are also involved in web attacks against Akamai’s customers by executing a variety of web attacks such as SQL injection, web scraping, credential abuse, and more.
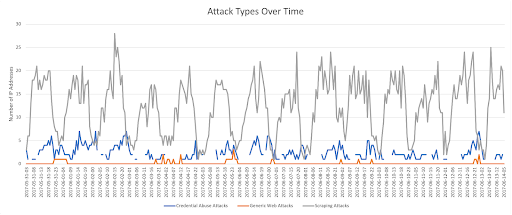 Figure 18: Web attacks by IP addresses per day over time
Figure 18: Web attacks by IP addresses per day over time
According to what we can see over time, the web attacks tend to occur on a daily basis. This can be explained by the attackers’ objective to be seen as legitimate users that are active during daytime hours.
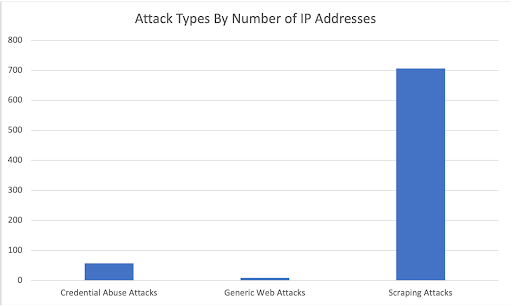 Figure 19: Total number of IP addresses per attack type
Figure 19: Total number of IP addresses per attack type
According to what we can see in the aggregation based on the attack type (Figure 19), the majority of attacks are scraping and credential abuse. This data represents a known trend in the web application attack landscape, showing an increased volume in the attacks that abuse application functionality.
Note that at the time of writing, we couldn’t find direct evidence that indicates that the owners of the Fast Flux network also offer infrastructure or proxying capabilities for executing web attacks.
Summary
Fast Flux networks can be compared to a living organism — an organism that evolves and changes over time as part of its self-preservation mechanism. Tracking such evolving networks is nearly impossible when only looking for incriminating malicious evidence. By the time the evidence is collected, the network will already be changed.
To track such networks, a different approach is required. They need to be tracked based on network attributes, derived from their malicious fluctuation phenomena.
As the largest CDN in the world, Akamai can only appreciate and regret at the same time the amount of technological effort being invested in building such malicious networks that are resilient and evasive to detection.
We believe that the right approach for detecting such networks is to focus on the ever-changing behavior of the network and, as a result, use algorithms that will enable detection of such behaviors. Having visibility to a wide range of data sources such as enterprise traffic, as well as web traffic, can result in better insights on the threat landscape and can lead to improvement in detection capabilities.
Those techniques need to be able to look at attributes and features of such networks, understand which ones are the most relevant, and build algorithms that differentiate legitimate networks from Fast Flux networks.
During our research, Akamai was also able to spot and mitigate malicious activity originating from one of its enterprise customers, where a compromised machine was trying to download malware from one of the domains being hosted on the Fast Flux network.
Monitoring and blocking any access to such Fast Flux networks are critical for security teams around the world. To prevent infection, businesses must add another layer of protection that will eliminate the communication channel to malware or phishing websites. Doing that will help with keeping up with the next emerging threat outside your door.



