Crypto Threats Surge by 500%, and It's All About the Money

Previously reserved for early adopters and tech-savvy consumers, cryptocurrencies have gone mainstream -- with tech entrepreneurs and prominent financial institutions leading the charge.
In the past year, rapidly increasing cryptocurrency rates, the introduction of new currencies, and the official trading of cryptocurrencies have called into question the threats posed by cryptomining abuse and cryptocurrency scams.
In this blog, we'll examine how escalating currency rates and the continued adoption of cryptocurrencies impact the threat landscape -- and what our data can tell us to expect in the future.
Malicious cryptomining malware traffic
In the past few years, malware variants that infect both personal computers and corporate servers have become an increasing trend. Their objective is to utilize infected device computing resources for cryptomining activities. Sampled DNS traffic data between January 2020 and March 2021 shows a correlation in the surging increase in traffic from cryptomining malware and the price increases of both Bitcoin and Ethereum cryptocurrencies.
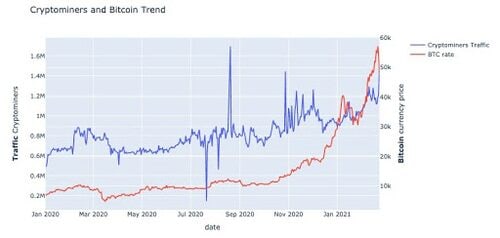
Figure 1: Traffic to malicious cryptomining and the effect on Bitcoin prices
During this time period, Bitcoin prices increased by over 800%, Ethereum prices increased by over 1,300%, and traffic from malicious cryptominers increased by over 200%.
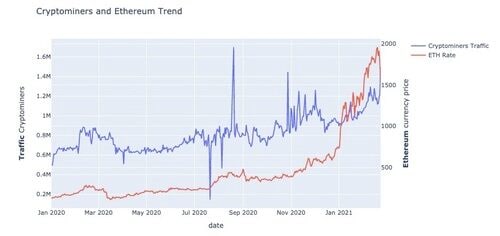
Figure 2: Traffic to malicious cryptomining and the effect on Ethereum prices
We believe the increase in malicious traffic is driven by the increase in cybercriminals' motivation to execute cryptomining activities. As cryptocurrency prices grow, and the potential benefit from malicious mining activities increases, cybercriminals gain momentum as well.
Phishing attacks abusing crypto consumers
Because phishing is one of the most prominent and growing threats, we looked into phishing attack trends involving crypto exchange consumers. In such scams, cybercriminals will create fake websites that mimic the appearance and functionality of crypto exchange websites to deceive victims into giving away their credentials. Once credentials are stolen, cybercriminals own the victims' crypto wallets and execute fraudulent transactions.
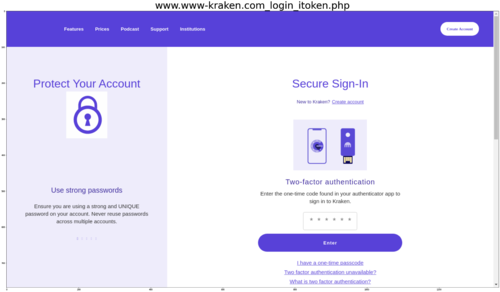
Figure 3: An example of a phishing website stealing hardware-based OTP tokens
Akamai has been tracking high-scale phishing scams that bypass multi-factor authentication (MFA). These scams also target crypto exchange agencies and try to steal credentials that are protected by one-time password (OTP) tokens.
We can also see a significant increase in the number of fake crypto exchange phishing URLs being accessed in the wild, with an increase of over 500% between March 2020 to May 2021.

Figure 4: Phishing attacks on crypto exchanges
Similar to malicious cryptomining activities, rapidly growing cryptocurrency rates have most likely increased the demand for compromised crypto exchange accounts in the dark market, leading to a surge in phishing attacks.
Ransomware and cryptocurrency affairs
Ransomware has made headlines this past year by causing significant financial damage to organizations around the globe. One noticeable example, the recent attack on the Colonial Pipeline, caused the company to temporarily shut down operations, and the incident once again garnered mainstream media attention.
As opposed to crypto exchange phishing or cryptomining attacks, cryptocurrency is not directly motivating cybercriminals to execute ransomware attacks. With ransomware attacks, cryptocurrency enables attacks that use cryptocurrency as a payment method because it gives cybercriminals a layer of anonymity.
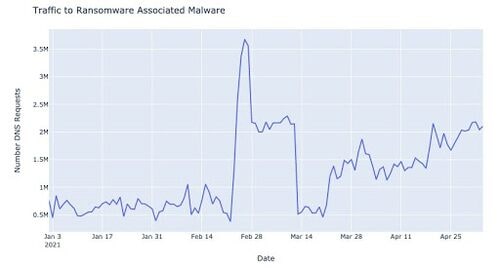
Figure 5: Traffic to ransomware-associated malware websites
Ransomware attacks have gained momentum in the past year, and we believe cryptocurrency has enabled and supported that trend. According to sampled DNS traffic, we saw an increasing trend in the volume of traffic to ransomware-associated malware websites between January and April 2021, with more than a 250% increase in traffic.
Elon Musk scam
Another scam that has recently gained strong momentum includes a social engineering technique that convinces victims to send crypto coins to cybercriminals' wallets with the promise of repayment that is double the original amount.
We saw a good example of that in the wild with the Elon Musk scam, which abused Musk's reputation as an entrepreneur and Tesla as an organization that advocates for the use of cryptocurrencies. This scam presented a reliable and trustworthy airdrop event on a phishing website that appeared to be supported by Musk and Tesla. An airdrop event occurs when a cryptocurrency or organization decides to distribute tokens or coins to users for any reason.
According to the scam phishing website, Tesla HQ declares that, as a supportive action to the crypto community, it will give back each participant twice the amount that was initially sent by the user. Needless to say, when it's too good to be true, it probably is; victims did not get their coins back.
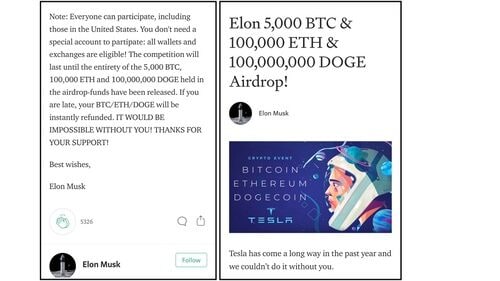
Figure 6: Fake Elon Musk phishing website
This scam used a variety of techniques to create a trustworthy and sustainable website, such as a newly registered domain that seems legit, giving the phishing website the look and feel of a well-known blogging platform, complete with fake comments from fake users indicating they just received repayment as promised. All these social engineering techniques helped gain victims' trust so they were more willing to take the risk and give away some of their coins.
Summary
The same cryptocurrency technology that prevents users' identities from being exposed also motivates cybercriminals and explains why cryptocurrencies play a significant role in the modern cyber ecosystem. As a result, we can see more and more attack vectors, such as DDoS extortions and ransomware, that request payment in the form of cryptocurrency.
As cryptocurrency becomes even more significant, the trends reported in this blog don't come as a surprise. Yet the strong correlation between crypto rates and level of attacks being reported is surprising and indicates that cybercriminals are motivated by commercial forces.
Because some crypto-associated threats, such as cryptomining and DDoS attacks, involve abusing servers or infected computational devices, the potential impact is relevant to both consumers and businesses.
To apply proactive security monitoring and controls, we need to better understand the relationship between global events and what motivates cybercriminals to execute scams. Events that influence our lives, our economy, and our health will most likely trigger cybercriminals to target us by leveraging those events. Those attacks will happen when we're most vulnerable to lurking scams.
As an InfoSec community, we need to increase awareness, evaluate our vulnerabilities, better understand cybercriminals' mindset, and as a result, try to predict what might come next— and be ready for it.



