In China and Japan, Malicious Botnets Surge Amidst Holiday Ecommerce Traffic

Executive summary
Holidays in China and Japan see a large increase in malicious botnet attacks.
Akamai data finds a 15% increase in malicious botnet traffic in China around Lunar New Year.
Further findings show a 150% increase in such traffic in Japan around Gregorian New Year.
This, combined with other data from the past year — a 3x jump in attack traffic during China’s Singles’ Day — further demonstrates that attackers are leveraging the increased traffic around holidays to conduct their attacks in the retail and ecommerce verticals.
An increase in total traffic for online shoppers around holidays provides attackers with “cover,” allowing them to more easily mask their attacks as websites are hit with heavy traffic.
While a similar surge occurs during the high traffic seen at the end-of-year holidays in EMEA and the U.S. — China and Japan present an enticing opportunity for successful cyberattacks because of their sheer traffic volume.
Additionally, customers are more likely to update their online shopping profiles with up-to-date credit card information and credentials, providing a more lucrative target for attackers.
Attackers focus on credential stealing through account and website hacking. This data can then be sold on the dark web or used to perform additional attacks.
- Also, attackers target ecommerce websites in an attempt to buy up limited edition or limited supply items to resell them for a much higher price. This kind of attack damages a retail organization’s reputation and frustrates its customers.
- Understanding the patterns of botnet activity around holidays can help clarify and quantify the holiday risk, and when analyzed correctly, can provide security teams with actionable data to incorporate into their defense.
Entering the Year of the Tiger marked a return to pre-pandemic celebrations, as the region began to shift back to in-person family gatherings. One element that didn’t change, however, was 2021’s overwhelming shift to online shopping that produced a leap of 28% in sales last year.
This surge in online purchasing repeated in 2022 but came with a mirrored surge in malicious bot activity. Akamai data shows that in the days leading up to and including Lunar New Year, the activity of malicious bots increased 15% in China over the previous month. While a similar surge occurs during the high-traffic seen at the end-of-year holidays in EMEA and the U.S. — China and Japan present a particularly enticing opportunity for successful cyberattacks because of the sheer volume in traffic: Retailers and ecommerce here serve some of the largest populations in the world.
This means that under the cover of billions of shoppers and travelers completing holiday purchases, malicious bots carry out a variety of nefarious activities for which they are purpose-built, such as credential abuse, distributed denial-of-service (DDoS) attacks, price scraping, gift card fraud, and more. Juniper Research estimates that ecommerce fraud — often associated with malicious bots — will spike to 18% in 2021 to top $20 billion in losses for retailers globally (final numbers for the year have yet to be reported).
Lunar New Year bot activity comes after a similar surge around Singles’ Day
Akamai researchers monitored and analyzed malicious botnets (groups of bots that number in the millions) throughout APAC’s late 2021 and early 2022 holidays to examine underlying botnet attack data. Uncovering these attack trends helps IT and cybersecurity teams better understand the attackers that they’re up against.
Our observation uncovered a 15% surge in malicious botnet activity around Lunar New Year in the Chinese retail and ecommerce sectors.
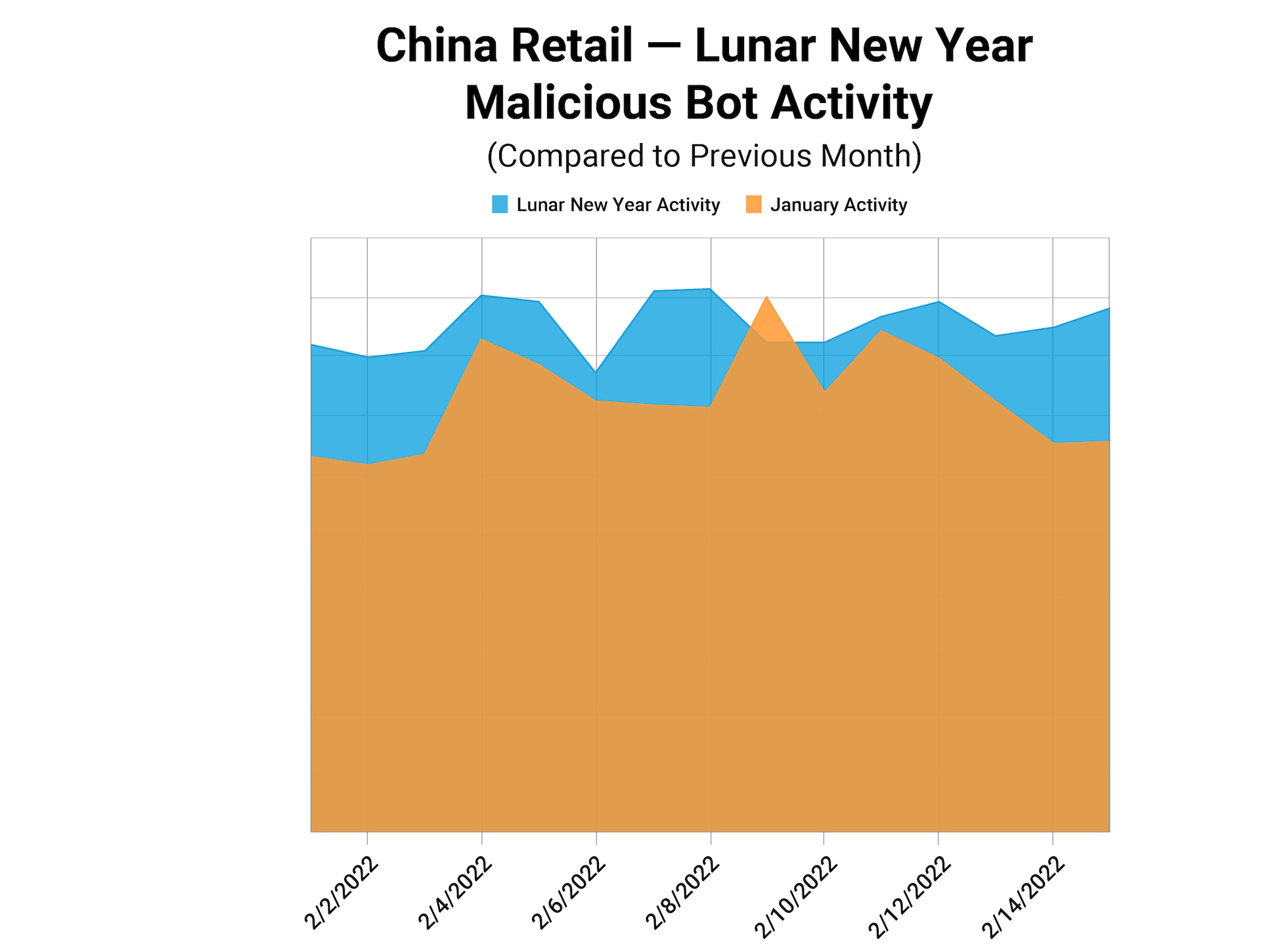
This represents a clear jump in attack traffic, despite the already high number of botnet attacks that started on Singles’ Day in November and that never completely subsided.
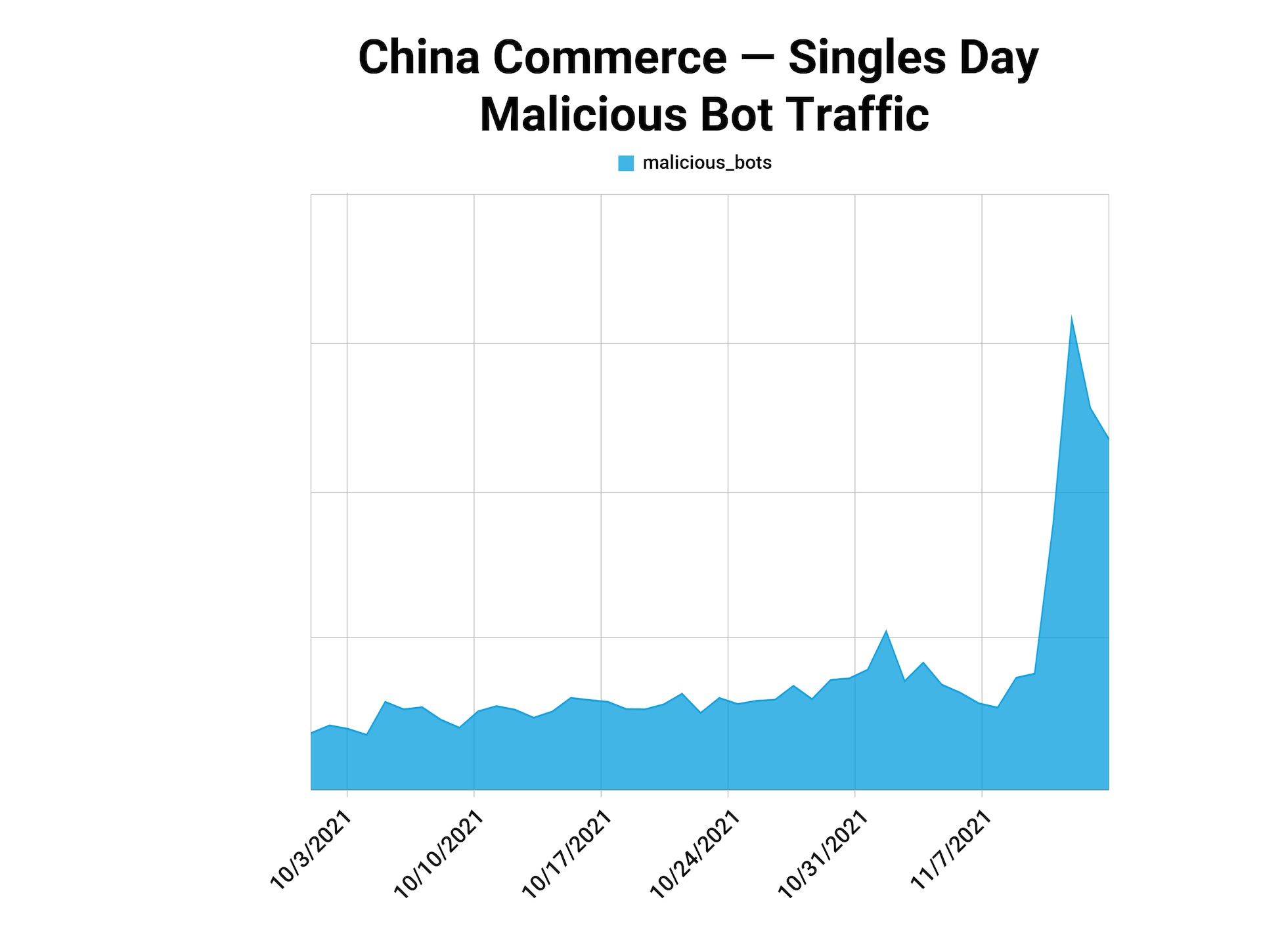
Taken together, this activity paints a picture of attack patterns around holidays in China, starting as a peak in botnet attacks of over 3x on November 11, 2021. Despite gradually declining in the months that followed, attack traffic remained relatively high through the end of the year, before peaking again at the buildup of retail traffic at the Lunar New Year.
The high attack traffic is no surprise, as Lunar New Year represents a huge time of celebration in China. Many shop and travel. The increased activity offers attackers an opportunity, as security teams are working harder to detect malicious traffic in the large numbers of legitimate traffic.
This year, online sales were boosted by the coinciding start of the 2022 Olympic Games in Beijing. Not only did more than a million shoppers flock to the official Olympic store on Tmall, the ecommerce platform, but online sales of winter sports equipment also rose year-over-year by 180% (skiing) and 300% (ice gear), along with a 30% rise in “ice and snow” travel booked on Fliggy between January 31 and February 4, 2022.
Surges in bot attacks appear at holidays throughout the region
Much like the traffic observed during the Lunar New Year, holidays represent a huge opportunity for attackers to conduct attacks across the APAC region. Japan, which has the fourth-largest ecommerce market in the world at US$141.26 billion (behind China, the U.S., and the U.K.), sees similar increases in malicious bot activity around the holidays each year.
Earlier this year, Akamai research measured a 2.5x increase in malicious botnet activity in the Japanese retail sector around the Gregorian New Year in early January. The attack pattern persists for weeks following the holiday, as attackers continue their attempts at credential stuffing, account takeover (ATO), or other data harvesting of personal information that has likely been updated in time for the holidays.
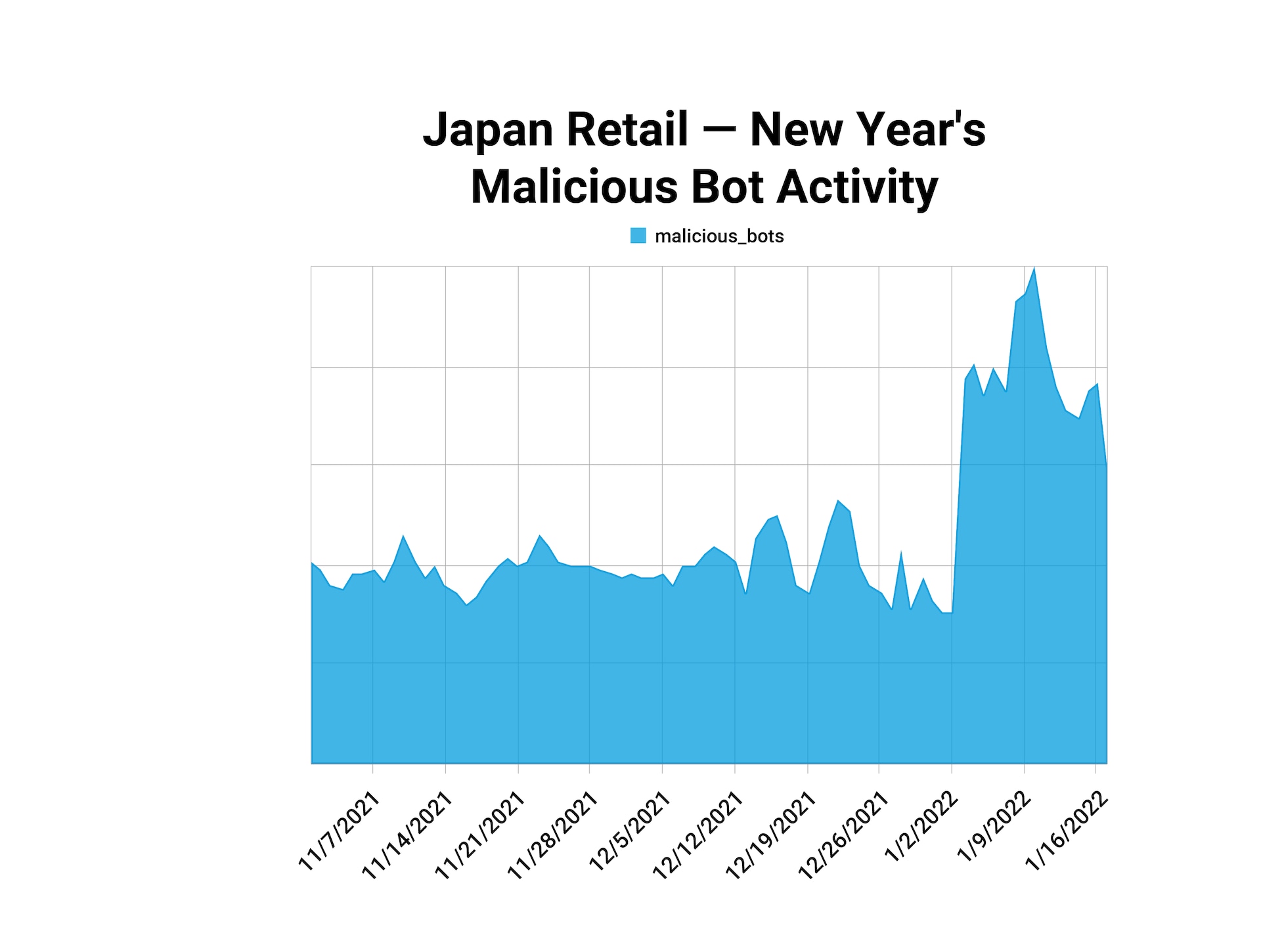
This pattern is very similar to the jump in attack traffic of 3x seen in China around Singles’ Day (see above chart), a similarity that demonstrates a consistency between the two holiday attack patterns. These patterns also point to the elevation in risk that retail and ecommerce organizations experience during holidays in the APAC region.
Malicious bots pose an array of cyberattack risks to an ecommerce organization
Akamai tracks benign and malicious bots as a proportion of internet traffic year-round. Malicious actors never stop attacks altogether, but surges around holidays let us know that they are dialing in their tactics, using the high volume of traffic as a cover for their activity.
Cybercriminals not only exploit the flurry of people shopping and celebrating during holidays, but they also exploit the fact that security departments are stretched thin by staff taking time off to be with their families and to travel. This gives attackers better opportunities to breach the perimeter, and more importantly, operate more freely, without being detected, or without timely mitigation.
Types of cyberattacks carried out by botnets
In credential stuffing attacks, bots are used to match stolen credentials that they have bought on the dark web or stolen themselves to find matches on various accounts. Because people still so often use the same passwords across platforms, criminals know they only need to try the login that worked at one retail site to see if it (or a variation of it) will work at another.
These credential stuffing attacks are automated and swift, especially when undertaken during the surges in traffic around holidays. Matched credentials then can be sold on the dark web or used for ATO.
Account takeover (ATO) by bots is a form of identity theft in which cybercriminals take over legitimate user accounts to commit fraud or steal credit card (CC) information, gift card balances, loyalty points, or other customer benefits that can be monetized. Holidays are the perfect time: Credit extensions have been obtained and accounts are primed for spending.
Once the accounts are in the hands of criminals, all their associated information — loyalty points, CC info, personal information — will be used or scraped, then sold.
Some malicious bots are used for reconnaissance; they are looking for vulnerabilities in websites where they can enter, embed their code, and plan their course for finding and exfiltrating data.
Still other kinds of bots are designed to flood ecommerce sites, rapidly buying up limited supplies of inventory that are in high demand (similar to “sneaker bots” in the West). Spurred by the ongoing global shortage of semiconductor chips — which has persisted since the spike in demand for chips in laptops and other electronics for remote work — cybercriminals have amassed everything from gaming consoles to cars to sell them at extremely inflated prices on secondary markets in Asia.
Whether they are attempting to verify stolen login credentials by logging on thousands of times with login variations or sitting and waiting to infiltrate and encrypt data with ransomware, we can measure their activity and plan for their next strike accordingly.
Holiday attack trends can be used as actionable data for ecommerce defense
Cybersecurity teams around the world know the risks of holiday traffic; for those responsible for the data and IP of retail and ecommerce sites, holidays represent an even bigger challenge. As traffic increases, attackers increase the volume of their attacks, which have the potential to immediately or in future scrape data, drain customer accounts, damage site functionality, and hold encrypted data ransom — all at enormous cost to businesses.
Understanding the patterns of botnet activity around holidays can help clarify and quantify the holiday risk, and when analyzed correctly, can provide security teams with actionable data to incorporate into their defense.
Find out more
To protect brands and customer loyalty, develop a strategy that takes into account attack patterns and the behavior of malicious bots at holidays and beyond. Learn more about Akamai Bot Manager.



