0.2 BTC Strikes Back, Now Attacking MySQL Databases
Last week we first tweeted that the Guardicore Global Sensor Network (GGSN) has detected a wide ransomware attack targeting MySQL databases. The attacks look like an evolution of the MongoDB ransomware attacks first reported earlier this year by Victor Gevers. Similarly to the MongoDB attacks, owners are instructed to pay a 0.2 Bitcoin ransom (approx. $200) to regain access to their content. We saw two very similar variations of the attack using two bitcoin wallets. In this post we will describe in detail the attack flow and provide some recommendations on how to protect your databases from similar attacks along with attack IoCs.
PLEASE_READ.WARNING
The attacks started at midnight at 00:15 on February 12 and lasted about 30 hours in which hundreds of attacks were reported by GGSN. We were able to trace all the attacks to 109.236.88.20, an IP address hosted by worldstream.nl, a Netherlands-based web hosting company. The attacker is (probably) running from a compromised mail server which also serves as HTTP(s) and FTP server. Worldstream was notified a few days after we reported the attack.
The attack starts with ‘root’ password brute-forcing. Once logged-in, it fetches a list of the existing MySQL databases and their tables and creates a new table called ‘WARNING’ that includes a contact email address, a bitcoin address and a payment demand. In one variant of the attack the table is added to an existing database; in other cases the table is added to a newly created database called ‘PLEASE_READ’. The attacker will then delete the databases stored on the server and disconnect, sometimes without even dumping them first.
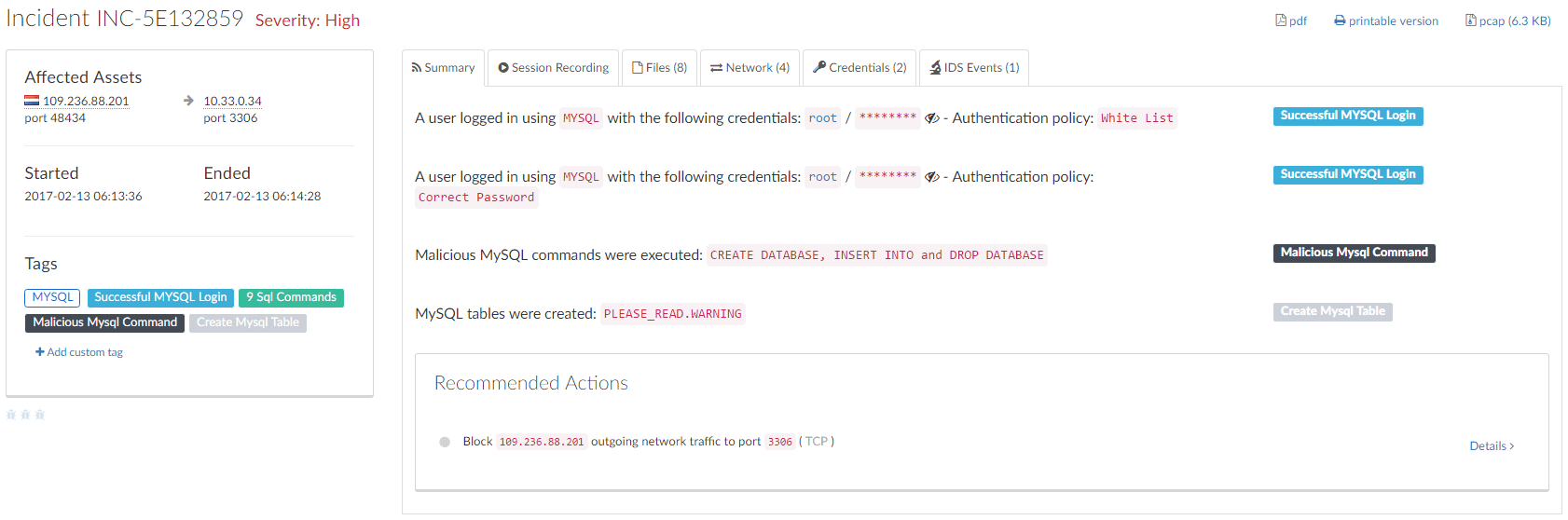 The attack as reported by Guardicore Centra
The attack as reported by Guardicore Centra
Two attack versions
We logged two versions of the ransom message:
INSERT INTO PLEASE_READ.`WARNING`(id, warning, Bitcoin_Address, Email) VALUES(‘1′,’Send 0.2 BTC to this address and contact this email with your ip or db_name of your server to recover your database! Your DB is Backed up to our servers!’, ‘1ET9NHZEXXQ34qSP46vKg8mrWgT89cfZoY’, ‘backupservice@mail2tor.com’)
INSERT INTO `WARNING`(id, warning)
VALUES(1, ‘SEND 0.2 BTC TO THIS ADDRESS 1Kg9nGFdAoZWmrn1qPMZstam3CXLgcxPA9 AND GO TO THIS SITE https://sognd75g4isasu2v.onion/ TO RECOVER YOUR DATABASE! SQL DUMP WILL BE AVAILABLE AFTER PAYMENT! To access this site you have use the tor browser https://www.torproject.org/projects/torbrowser.html.en’)
One version offers the victim to restore their data by contacting the following email address – ‘backupservice@mail2tor.com’. The second version offers the owner to visit the following darknet web site ‘https://sognd75g4isasu2v.onion/’ to recover the lost data.
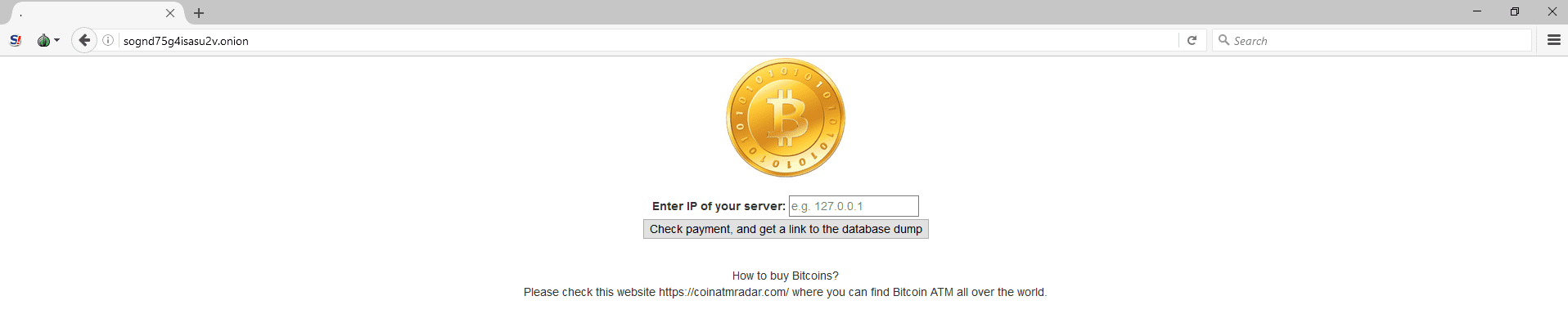 The darknet web site referenced in the ransom note
The darknet web site referenced in the ransom note
Each version uses a different bitcoin wallet, 1Kg9nGFdAoZWmrn1qPMZstam3CXLgcxPA9 vs 1ET9NHZEXXQ34qSP46vKg8mrWgT89cfZoY and based on Blockchain public information people have been paying up. Naturally, we can not tell whether it was the attackers who made the transactions to make their victims feel more confident about paying.
Preventing the attack
Every MySQL server facing the internet is prone to this attack, so ensure your servers are hardened. Also, make sure your servers require authentication and that strong passwords are in use. Minimizing internet facing services, particularly those containing sensitive information is also a good practice. Monitoring your internet accessible machines/services is crucial to being able to rapidly respond to any breach. This can be easily achieved using Guardicore Centra.
This way your security team could easily alert on new services accessed from the internet and enforce a policy which fits those servers (e.g. firewall, data restrictions, etc.). Periodic data backup could allow you restore most of your valuable data without the need to interact with the attacker and provide you with a backup plan should a similar attack occurs.
Check before you pay
Before paying the ransom we strongly encourage you to verify that the attacker actually holds your data and that it can be restored. In the attacks we monitored we couldn’t find evidence of any dump operation or data exfiltration.
IoCs
IP Address:
- 109.236.88.20
Mysql:
- Table: WARNING
- Database: PLEASE_READ (appears only in one variation of the attack)




