The Bondnet Army: Questions & Answers

Last week we annouced the discovery of Bondnet, a new botnet that was uncovered by Guardicore Labs. The originator of Bondnet had installed a cryptocurrency miner and backdoor in thousands of servers of varying power and conscripted them into a botnet – a group of computing devices that can be centrally controlled for malicious purposes.From there the Bondnet army can be used to launch DDoS attacks as we’ve seen with the IoT botnet Mirai. The fact that the Bondnet victims are servers with strong compute capabilities makes it possible for the attacker to use any victim server to scan more victims, exfiltrate data, deploy ransomware or laterally move inside a network. Bondnet victims include high profile global companies, universities, city councils and other public institutions.
Since we published we received many questions from reporters and bloggers about the nature of the attack, attacker motivation, identity and goal, dangers posed to organizations, the botnet discovery process and more. The following is a select list of questions and answers that we hope will shed more light on the botnet.
1. What is the attacker’s goal?
The primary goal of Bondnet is mining cryptocurrencies for profit. At a thousand dollar equivalent of Monero coins a day, our attacker is earning good money for what is considered a low risk, high reward activity. Using the existing infrastructure, the attacker can also easily pivot to deploying ransomware on thousands of servers or creating a high bandwidth DDoS botnet.
2. How is the Bondnet campaign different from the WannaCry ransomware worm in terms of goals, profits and delivery?
Both campaigns seem to be financially motivated. The WannaCry worm made a big splash over the last few days with over $76k though the campaign’s profits will now be carefully tracked by law enforcement. The Bondnet makes lower sums ranging between a few thousand to tens of thousands of dollars a month, by staying under the radar and not causing damage to the victims.
In terms of technical delivery the two campaigns vary – the WannaCry is a self propagating worm, with a single payload of ransomware while the Bondnet consists of a Remote Access Trojan (RAT) and cryptocurrency miners.
3. Were there any surprises with the discovery of the botnet?
We found ourselves surprised at multiple points while working on this botnet:
- Compared to prior mining botnets, Bondnet is relatively sophisticated. Many mining botnet operators are content with simply leaving a persistent miner, while Bondnet leaves a backdoor capable of taking full control of the system.
- When we started to analyse the Bondnet C&C logs, we came across the victims’ IPs. In this list we also saw IPs of the attacking machines. Those machines were communicating with the C&C. At this point we understood that all the machines we’ve seen so far, including the C&C servers themselves, were Bondnet victims.
- We were also surprised by the breadth and types of victims. Ranging from small businesses to large universities, it seemed that every organization has servers vulnerable to some kind of exploit.
- The Bondnet attack toolset is quite versatile. A partial list of tools includes obfuscated Visual Basic code, WMI MOF files, custom mining software alongside a Golang based web server forked from public repositories, browser extensions to hijack traffic and more.
4. What makes Bondnet stand out from its rival botnets such as the Mirai botnet? Does it have any unique features that users should be concerned with?
Bondnet stands out from its rival botnets in several key features:
- In terms of size, compared to the well known Mirai botnet, Bondnet is much smaller. Mirai has recruited tens of thousands of active victims. So far, Bondnet is an order of magnitude smaller, totaling a few thousand of active victims at any given time (with over 20,000 unique victims).
- Unlike many recent botnets in 2016 and 2017, the botnets victims are servers. Unlike IoT devices (Mirai) and PC endpoints (PhotoMiner), servers in general boast high bandwidth connections and strong compute capabilities. So far, large scale IoT botnets have been limited to creating highly damaging DDoS attacks but not much more than this. Bondnet victims have the bandwidth and compute power to actively scan and exploit more victims.
- Using the WMI trojan deployed as part of the attack, the Bondnet allows its operator to take full control of its victims. The cool thing about the trojan is that it receives Visual Basic code as commands and executes it with high privileges. Visual Basic code commands allow the attacker to easily extend the trojan’s capabilities and do almost anything on the victim.
- As part of the infection, Bondnet creates multiple access points that will allow it to return. To this end, it primarily uses the WMI trojan and when this fails, the Guest account is enabled and exposed over RDP and SMB.
5. You first discovered the botnet in January. Have you noticed any changes or modifications made to it ever since?
Absolutely, the attacker has since constantly monitored and updated the Bondnet underlying infrastructure and software. The attacker has been uploading new versions of the miner software on a weekly basis, tracking the source code of many popular repositories. To make it less trackable the attacker frequently rotates the list of victims acting as file servers. These changes require updates and changes in the attack and installation scripts.
6. Could you briefly explain the attack flow?
Let’s use this diagram to explain the flow:
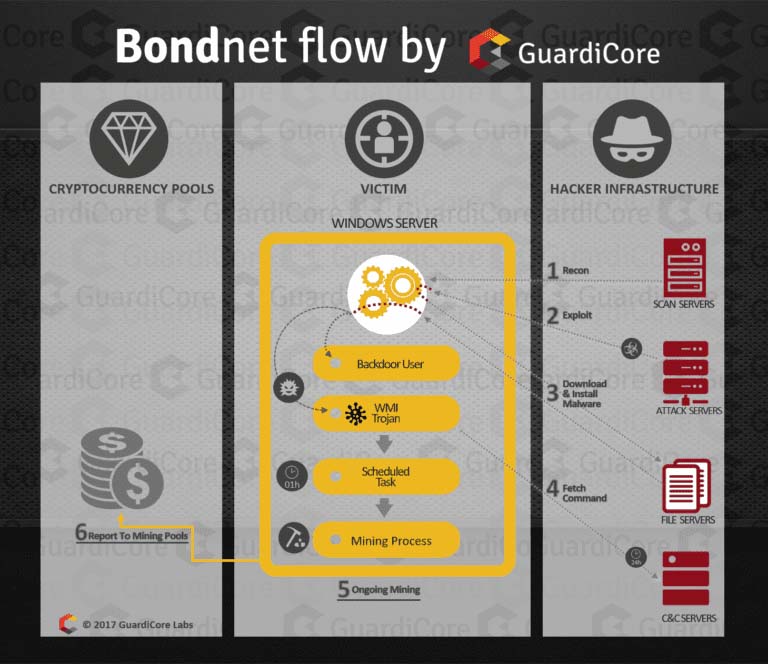
- First, the attacker uses reconnaissance to find potential targets.
- After finding a target, the attacker tries to get into the server. In this stage the attacker uses a mix of vulnerabilities and weak user/password combinations to primarily attack Windows Servers.
- After securing access to the victim server, the attacker downloads & installs a cryptocurrency miner and a trojan that allows the attacker to take complete control of the victim server.
- The trojan downloads a command file from a C&C server and executes it.
- The miner is activated hourly by a scheduled task to keep it mining for the attacker, primarily Monero.
- The miner reports to a to a cryptocurrency pool. More money is added to the attacker’s wallet…
7. How does the botnet attack/infect machines? Is there a specific type of target?
The attacker uses a mix of old vulnerabilities and weak user/password combinations to primarily attack Windows Server machines (covering Server 2003, 2008, 2008 R2, 2012, 2012 R2). The attack vectors we uncovered include known phpMyAdmin configuration bugs, exploits in JBoss, Oracle Web Application Testing Suite, ElasticSearch, MSSQL servers, Apache Tomcat, Oracle Weblogic and other common services.
8. What dangers does this pose to businesses? What type of effects can this have?
Businesses with infected servers are at a double risk. The attacker has created two backdoors – a WMI trojan and a backdoor user, allowing the attacker to do practically anything on the compromised machine. Organizations should be alarmed as the backdoor user is easy to test remotely, allowing other attackers to search the internet for victimized servers and easily connect to them.
9. How did Guardicore Labs discover the botnet? Have you seen anything like this before?
We were able to do it using our GGSN, which is basically the Guardicore deception technology installed in multiple locations across the globe. It constantly streams early threat information which we later investigate to identify new and unknown attack vectors/malwares like Bondnet.
It is not the first time we’ve detected attackers mining on their victims. Last year we detected the Photominer, a worm propagating through FTP servers. Unlike Bondnet, the Photominer botnet targeted desktop machines and used the servers they accessed as a launching pad for attacks . It used to scan for open FTP servers and upload itself to every folder available on the compromised machine, aiming to infect web server code and from there attack anyone browsing to that server.
10. How can businesses protect themselves from this type of threat?
A well known best practice is that all services and particularly internet facing ones should be monitored for resource usage spikes and unexpected network connections. Any irregularities should be escalated to both IT and security teams. In addition, network based monitoring solution such as Guardicore Centra can easily alert on known malware and new suspicious connections (revealing unknown services exposed to the internet or machines accessing cryptocurrency pools).
It’s also important to lock down all internet facing services. For example, MySQL servers which are our attacker’s most common victims. Simply locking down MySQL instances to prevent running arbitrary SQL commands would have mitigated the infection vector of this attack as would have preventing the MySQL service from writing arbitrary data to the file system and loading external code.
In addition, regular monitoring of all WMI activity and all user accounts is important. Monitoring modifications such as changing user passwords would have quickly alerted the relevant security team which could investigate the incident.
Specifically in case of this botnet, detection is easy if IT knows what to look for, as we detailed in our report.
11. Is the size of the botnet shrinking now that you’ve shed light on it?
Over the past two months we haven’t seen it shrink but rather slowly grow. This is because the vast majority of targets are not security aware and are applying minimal to no security measures to protect servers. Administrators that do respond seem to be doing this because of the spike in the CPU load rather than being aware of a “vulnerability”. We see many cases of reinfection, that is machines that are reinfected after being cleaned.
We have contacted via email some of the companies that were hit by the Bondnet and helped them clean their infected machines. But this is only a drop in the ocean as the internet is flooded with vulnerable machines that we can’t identify their owners. The fact that the attack infrastructure is based on victim machines makes it way harder to shut down the botnet.
12. Has the hacker used the botnet for anything other than cryptocurrency mining?
We’ve seen the attacker use the botnet for cryptocurrency mining and also as part of the attack infrastructure. Being part of the infrastructure means some of the victims are re-purposed as attack and C&C servers. We haven’t been able to track all operations by the attacker on victim machines, as they can be accessed via the backdoor user . So far, none of the infected companies we’ve been in touch with has reported any additional malicious activities.
13. When you say “The attacker’s code handles Chinese desktop victims differently compared to all other victims,” what exactly do you mean?
The post-exploitation payload executed on the victim machine installs a miner and a trojan on most machines. The payload code has a special case for Chinese desktop machines, on which it installs a browser ad hijacker instead of a miner. The code’s definition for a desktop machine is low uptime (less than 24 hours) and a small number of CPUs (less than 8).
Based on our knowledge and observations, the vast majority of the attacker’s efforts are focused on servers, making desktop victims a small portion of the overall victims.




