Akamai Blog | Australia Experiences Massive Spike in WAF Multi-Vector, DDoS Attacks

With web applications under increased attacks, Akamai has analyzed data points for web application firewall (WAF) multi-vector and DDoS attacks between April 2021 and March 2022 to determine the severity of the situation in Australia.
Insights from the Akamai Intelligent Edge Platform signal an alarming trend
We observed a massive spike in WAF attacks from September 2021 to October 2021, and a steady resurgence of these attacks with a 100% increase in Q1 2022. This shows that attackers are redoubling their efforts to disrupt the Australian market after a sharp drop between October 2021 and December 2021.
The WAF activity chart in Figure 1 shows the monthly number of WAF attacks recorded from April 2021 to March 2022 per attack vector represented by the colored lines.
The top attack vectors were XSS (cross site scripting) and LFI (local file injection), which could indicate that attackers are trying to inject or execute malicious payloads to plant malware and potentially initiate remote code execution attacks.
 Fig. 1: Australian WAF activity chart. Source: Akamai Intelligent Edge Platform analysis, April 2022.
Fig. 1: Australian WAF activity chart. Source: Akamai Intelligent Edge Platform analysis, April 2022.
As part of our analysis, we ranked each country by the total number of attacks in millions and per attack vector (see Figure 2).
Akamai can reveal that the Australian financial services sector has become a top target for web and API application programming interface) attacks globally.
The preferred attack vectors were XSS and LFI with LFI topping the global attack vectors with more than 200 millions attacks. This is significant because the United States has been the largest target for WAF attacks by a large margin as compared with other countries globally.
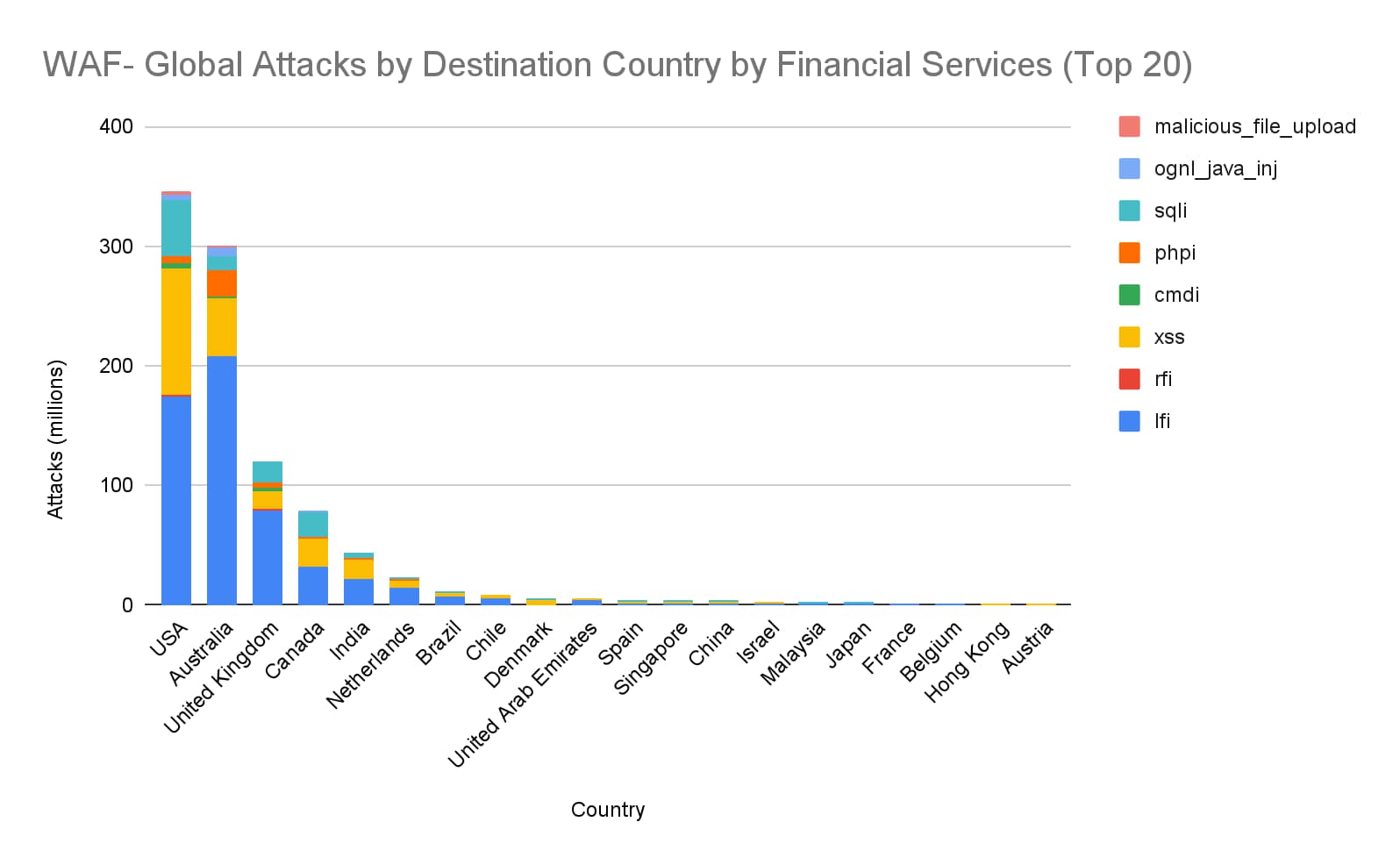 Fig. 2: Total number of attacks per country in millions and per attack vector. Source: Akamai Intelligent Edge Platform analysis, April 2022.
Fig. 2: Total number of attacks per country in millions and per attack vector. Source: Akamai Intelligent Edge Platform analysis, April 2022.
DDoS attacks hit record highs
Figure 3 illustrates the peak volume of DDoS attacks per month by industry from April 2021 to March 2022. It shows that the volume of DDoS attacks that targeted the financial services industry soared to new heights from July 23, 2021, to mid-November 2021.
The attacks were not only large in volume but sustained over that period, which is indicated by the large bubbles.
In the first quarter of 2022, attackers turned their focus to more opportunistic attacks, targeting softer targets such as education and the public sector.
However, as with the WAF attacks, the respite will be short-lived and attackers will likely redouble their efforts toward large financial institutions. We saw a glimpse of that starting in late February 2022.
The DDoS attacks peaked during the same period as the WAF attacks between July 2021 and October 2021, indicating that these were coordinated attacks by organized gangs of attackers rather than random attacks.
We have seen the Conti and Revil ransomware gangs use DDoS volumetric attacks as a means to extort ransom from targeted companies.
 Fig. 3: The peak volume of DDoS attacks per month by industry in Australia and New Zealand. Source: Akamai Intelligent Edge Platform analysis, April 2022.
Fig. 3: The peak volume of DDoS attacks per month by industry in Australia and New Zealand. Source: Akamai Intelligent Edge Platform analysis, April 2022.
API attacks become mainstream
Once limited to specific internal software applications (apps) primarily to reduce operational overhead and facilitate integration, APIs have now entered the mainstream.
The increasing shift to API-centric architectures, including mobile apps, microservices, composable architectures, and third party integrations is contributing to the sharp increase of API-related attacks.
This trend is evident on the Akamai platform with API traffic composing 92% of web volumes. The issue with a shift to APIs is that it challenges conventional approaches to security and governance, making them a ripe target for attackers.
As API-related risk is increasing, API protections were added to the OWASP Top 10, and regulators across the globe are implementing API security requirements to compel businesses to focus on addressing this growing area of vulnerability and risk.
We expect to see attacks continually increase over the course of 2022 that will impact organizations across all sectors, and organizations will need to find ways to mitigate such attacks by deploying API protections that can circumvent DDoS malicious injection, credential abuse, and API specification violations.
With Akamai, you can automatically and continuously discover and profile APIs, including their endpoints, definitions, resources, and traffic characteristics. Akamai's cloud- and origin-agnostic approach allows for easy discovery across your entire application estate without any additional configuration required.
This visibility enables developers, application owners, and security teams to stay ahead of new, unknown, or changing APIs and to easily register them for protection.
In each of the past four years, Akamai was named the Leader in the Gartner Magic Quadrant for Web Application Firewalls. Akamai offers something nobody else has: an edge platform with unmatched visibility into the ever-evolving threat landscape.
The Akamai Intelligent Edge Platform has helped mitigate attacks on customers across all industries by providing broad API protections to deal with DDoS, malicious injection, credential abuse, and API specification violations while providing scalability and performance for API traffic.




