The High Stakes of Innovation: Attack Trends in Financial Services

Editorial and additional commentary by Cheryl Chiodi
Executive summary
Web application and API attacks in the financial services industry grew by 65% when comparing Q2 2022 with Q2 2023, accounting for 9 billion attacks in 18 months. This was driven in part by cybercriminal groups' active pursuit of zero-day and one-day vulnerabilities as pathways for initial intrusion.
Financial services continues to see a rise in Layer 3 and Layer 4 DDoS attacks and has surpassed gaming as the top vertical. This increase appears to be caused by the dramatic surge in the power of virtual machine botnets and pro-Russian hacktivism motivated by the Russia–Ukraine conflict.
The Europe, Middle East, and Africa (EMEA) region accounts for 63.52% of Layer 3 and Layer 4 DDoS events, continuing the “regional shift” trend observed last year. The number of attacks against this region was nearly double the number of the next top region. We surmise that this is due to the attacker groups’ financial political motivations against European banks. Additionally, this shows how easily adversaries can quickly switch their attention.
While the financial services industry has fewer third-party scripts than other industries (30%), it’s prone to attacks like web skimming. However, financial services institutions are starting to adopt solutions to comply with the new requirements in Payment Card Industry Data Security Standard (PCI DSS) v4.0.
The ascending number of malicious bot requests (1.1 trillion), which spiked by 69%, exemplifies the continued assaults against financial services customers and their data via attacks like account takeovers and risks posed by financial aggregators.
The 2023 financial services State of the Internet (SOTI) report not only reaffirmed familiar threat trends seen throughout this year's security research but also provided some unique sector insights. The report is based on both the threat traffic we defend against and best practices we’ve learned from our customers.
Noteworthy trends: Web attacks on the rise
A noteworthy shift we observed is the ranking of the financial services industry in distributed denial-of-service (DDoS) attacks. This year, the financial services industry ranked first for DDoS attacks while remaining third for web application and API attacks and first for phishing.
For the first time in this report, we broke out financial services into sub-verticals (Figure 1). This deeper examination of web application and API attacks in financial services revealed that banks are bearing the brunt of web attacks (58%), followed by other financial services companies, such as fintech, capital markets, property and casualty insurance, and payment and lending companies (28%).
Insurance companies account for 14% of web application and API traffic within the financial services sub-verticals. These overall increases originate from a surge in publicly available web application vulnerabilities, which are ripe for exploitation and abuse. Our previous SOTI report, Slipping Through the Security Gaps, highlighted how 2022 was a record year for web application and API attacks due to the emergence of critical security flaws like the ProxyNotShell vulnerability (CVE-2022–41040).
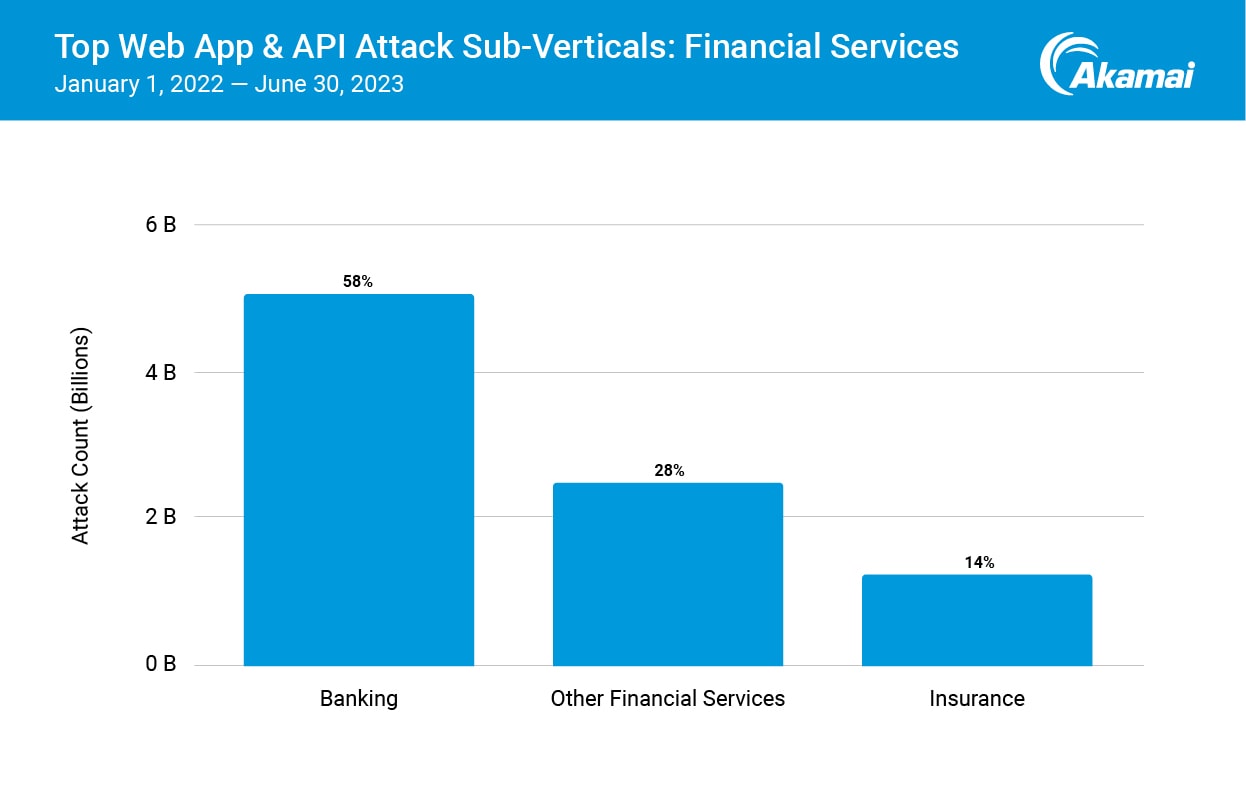 Fig. 1: Banks are heavily impacted by web attacks due to the type of data they possess; however, other financial services organizations like fintech, capital markets, and so forth are also significantly hit
Fig. 1: Banks are heavily impacted by web attacks due to the type of data they possess; however, other financial services organizations like fintech, capital markets, and so forth are also significantly hit
DDoS attacks: A growing security concern
Layer 7 DDoS attacks are a growing problem for financial applications. Cybercriminals are setting new records and making nonstop efforts to elevate their attack operations, networks, and tactics, techniques, and procedures (TTPs) to combat stronger defenses. Some of the most common characteristics that we’ve observed from many large-scale DDoS attacks include:
Highly distributed IP/subnet and countries
Abundant attack sources, including infected/leased cloud service providers, Tor exit nodes, anonymous/open proxy nodes
GET floods
Noncacheable URLs, such as home page, random URLs, login endpoints
IP spoofing by advanced attackers who create botnets behind residential ISPs, mobile carrier networks, or university networks.
Dynamic and adaptive strikes, based on defenders’ responses
For Layer 3 and Layer 4 DDoS attacks, financial services has surpassed the gaming industry to become the most attacked vertical, accounting for 29.25% of attack events. DDoS attacks have long been cybercriminals’ most powerful weapons, capable of causing massive service disruptions, catastrophic financial losses, and disruptions across a network's resources and operations at any moment.
Assaults against financial services customers continue
In this SOTI, we reviewed a trend we reported on in 2022 showing the focus of attackers going after customers. We see that while account takeover took the lead last year, more than 50% of the IPs targeting financial services this year are related to web scrapers (Figure 2). These automated tools are used to harvest information from websites and create exact replicas of sites for phishing purposes, subsequently tricking users into divulging their sensitive information.
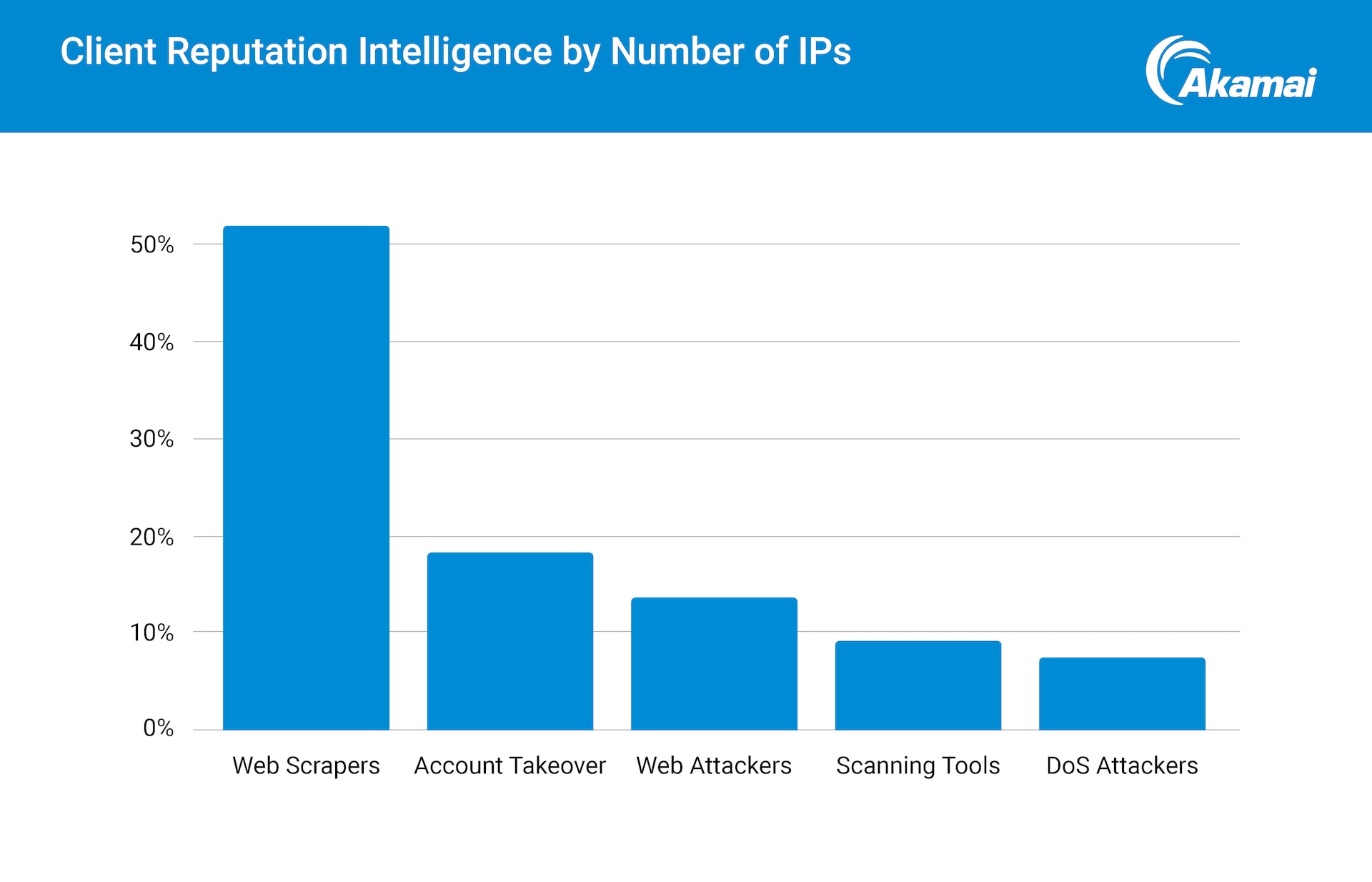 Fig. 2: Distribution from the Akamai Client Reputation intelligence platform showing threat vectors that are targeting the financial services vertical over a 90-day period
Fig. 2: Distribution from the Akamai Client Reputation intelligence platform showing threat vectors that are targeting the financial services vertical over a 90-day period
Regarding compliance, it's essential to highlight the Digital Operational Resilience Act (DORA), a comprehensive EU regulation that will impose obligations on the European financial sector and some of their third-party services providers. Similarly to what has happened with the EU data protection framework (the General Data Protection Regulation), DORA could become a resiliency regulation example that other countries, including the United States, will observe when developing rules for the financial sector.
Safeguarding measures
The threat of shadow APIs and access control bypass attacks is a critical challenge arising from innovation to support customers. The industry must:
Rapidly detect rogue APIs, whether customer-facing or internal
Monitor them for attacks or abuse
Establish processes to investigate incidents
Automate mitigation policies
The same recommendations for visibility and response apply to issues regarding account takeover, financial aggregators, web scraping, and phishing; these edge-facing issues are a great area in which to leverage OWASP Top 10 and MITRE ATT&CK framework to develop training, maturity baseline measurements, and test plans for red team/penetration testing groups.
Financial institutions can also use the ATT&CK Navigator tool as a template to run a purple team exercise based on a specific threat like CL0P. (Purple teams perform simulation attacks to find security weaknesses in an organization’s perimeter with the goal of enhancing its security.)
Up-to-date defenses
As DDoS continues to be a major threat vector, the financial services industry must ensure that it has up-to-date plans for Layer 3 and Layer 4 (infrastructure) and Layer 7 (web) attacks. Valuable exercises include validating playbooks and tracking the attack trends for both size and speed to evaluate your risk based on current capabilities.
In addition, it's advisable to determine a trigger for conducting technical exercises. For instance, if you haven’t experienced an attack in the last three quarters, you should conduct a live exercise.
Detecting and promptly responding to web scrapers that are harvesting customer or website information for the purpose of creating fraudulent phishing sites is crucial. There are a number of tools and services to accomplish this and it is important to collaborate with your fraud prevention team when developing your process/solution.
Financial services prepares for new PCI DSS requirement
Finally, financial institutions must address the increased attention from both cybercriminals and regulators around their JavaScript environments. Although this area has not been as high on risk registrars in the past, you should act early to get the right controls in place to comply with the recently released PCI DSS v4.0 to prevent a crisis.
You should also partner closely with your legal department to update policies that address the emerging regulations on areas like resiliency.
Learn more
We hope these insights allow you to have conversations with partners about ROI and risk, and that the data provides you with effective tactical approaches to defend your financial institution and customers from threats.
Stay plugged into our latest research by checking out our security research hub.



