An Attack Surface Workout for Web Application and API Attacks

Written by: Tom Emmons
Executive Summary
Akamai researchers have analyzed web application and API attacks over the past year and have seen a threefold uptick in Q1 2022 vs Q1 2021.
Local file inclusion (LFI) attacks have seen a massive increase, now outperforming structured query language injection (SQLI) as the most prevalent web attack vector.
The majority of the attacks being executed are targeted at our U.S. customers.
Commerce was the highest targeted vertical, with high technology seeing the most growth in 2022 to date.
There are three major patterns we’ve gleaned from this data: long-running attack campaigns, short-burst attack campaigns, and one-time attack campaigns.
Introduction
Web application and API attacks and zero-day vulnerabilities have been on an absolute tear over the last 9 months.
Even before the likes of the Log4j and Spring4Shell exploits, the frequency of these types of attacks was trending upward. Suffice it to say, incident responders have faced back-to-back headline-making zero-day vulnerabilities that have consumed their time and attention. This is in addition to a steady growth in malicious AppSec traffic across the usual web application and API attack suspects.
 We see the attack growth across industries, geographies, and customers.
We see the attack growth across industries, geographies, and customers.
The surge has largely been driven by LFI attacks, which took the lead from SQLi attacks in mid-2021 before taking off in the fall, registering a threefold increase between June 2021 and March 2022. Injection attacks (PHP, Command, JavaScript) are well up (with the exception of SQLI, which is relatively flat), but nowhere near the meteoric rise in LFI, as we discussed in our recent blog post on the subject.
LFI attack flows
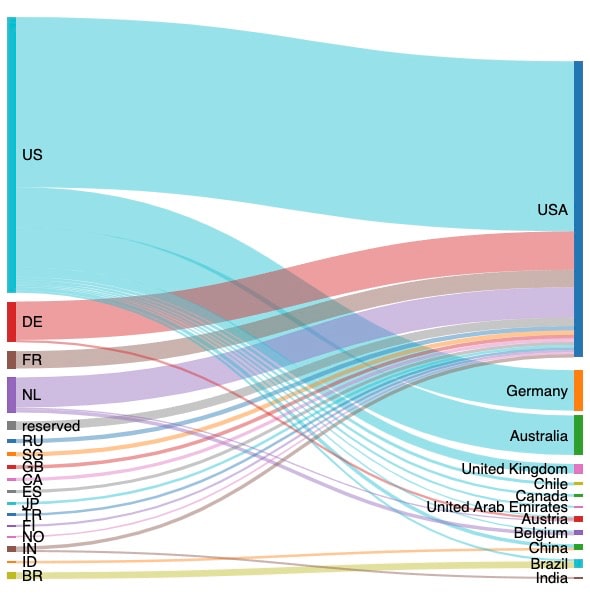
Although the United States is both the origin (see the left side of the figure below) and destination (see the right side of the figure below) of more than half of the LFI attack attempts in early April 2022, there are large flows between other countries and the United States as well. Some countries are largely sources of LFI attack traffic (the Netherlands) and some largely receivers (Australia).
LFI traffic flows: source country to destination country |
LFI attack types
https://xyz.com/main/../../etc/passwd |
file=../../../../../etc/password |
From a content perspective, directory traversal with a specific focus on getting to “/etc/password” seems to compose the lion's share of LFI activity. The attackers either (A) hope to learn login names and GECOS fields that can be useful in future attacks; or, more likely, (B) use their ability to access the file as a flag that security controls can be circumvented and other readable files are accessible.
Some great commentary on the value of “/etc/password” files can be found on Stack Exchange.
Web application and API attack breakdowns
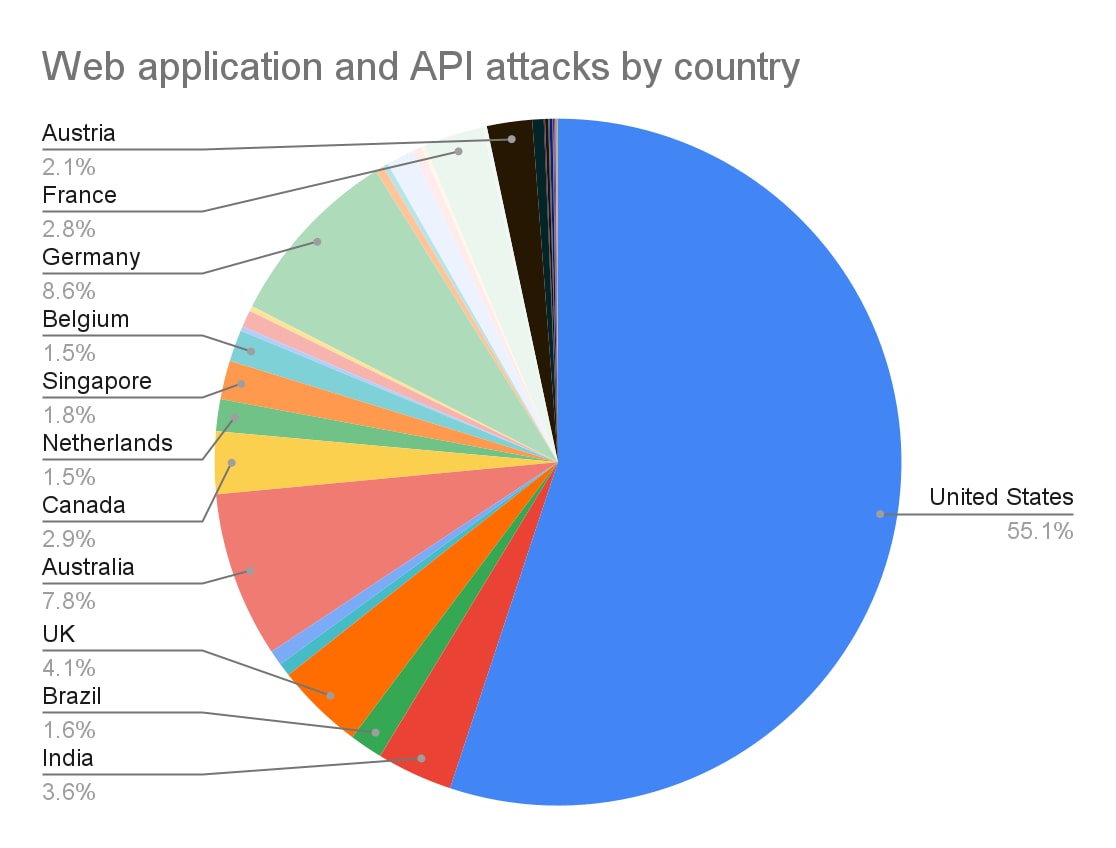
The pie chart below showcases the geographic destination breakdown of the 2022 attacks. As you can see, the majority of the attacks have been launched against our U.S. customers, but both EMEA and APAC were also heavily targeted. A number of countries (e.g., Germany and Australia) have seen attack activity that is out of line with their normal traffic rates.
The industry breakdown chart below highlights the commerce vertical, which saw the most attacks, while high technology has seen the most growth thus far in 2022. There are certainly more than enough attacks to make their way across industries.

Top attacks of 2022
To understand what is dominating the web attack space, we focused on the top 1,000 attacks we’ve seen thus far in 2022 across 93 customers. After collating the data, we’re left with a chart that looks somewhat like a bizarre psychological test.
NOTE: For all figures that follow:
Each customer was assigned a different color.
The y-axis is the number of web application and API attacks in a given day.
The size of the bubble is the deviation from the average number of web application and API attacks per day.

If you squint hard enough at the Top 1,000 web application and API attacks figure above, three patterns emerge from the chaos. You can see lines, clusters, and outliers, all of which can give us some interesting insight.
Pattern #1 — long-running attack campaigns
The customers highlighted in the figure below get attacked so often and consistently you could draw an imaginary line through their data points in the charts. This pattern is shared among these customers despite the fact they are in different industries and geographies. Although each customer has their outliers, all three have seen a steady increase between Q1 2021 to now, peaking at more than 10 million daily attack attempts.

Pattern #2 — short-burst attack campaigns
The second pattern, shown in the figure below, is much less linear. These customers see bursts of activity in which the daily attack volumes run 10 to 30 times over their 2022 average, which tend to naturally cluster over a few days. The bursts are difficult to predict — they seem to come out of nowhere and go away as they came. This is in stark contrast to the first pattern, which seems to have structure to it. These short-burst campaigns can be just as daunting to an organization as the previous type. Although the attacks aren’t as large in number, they do not have the predictability afforded by the long-running campaigns.
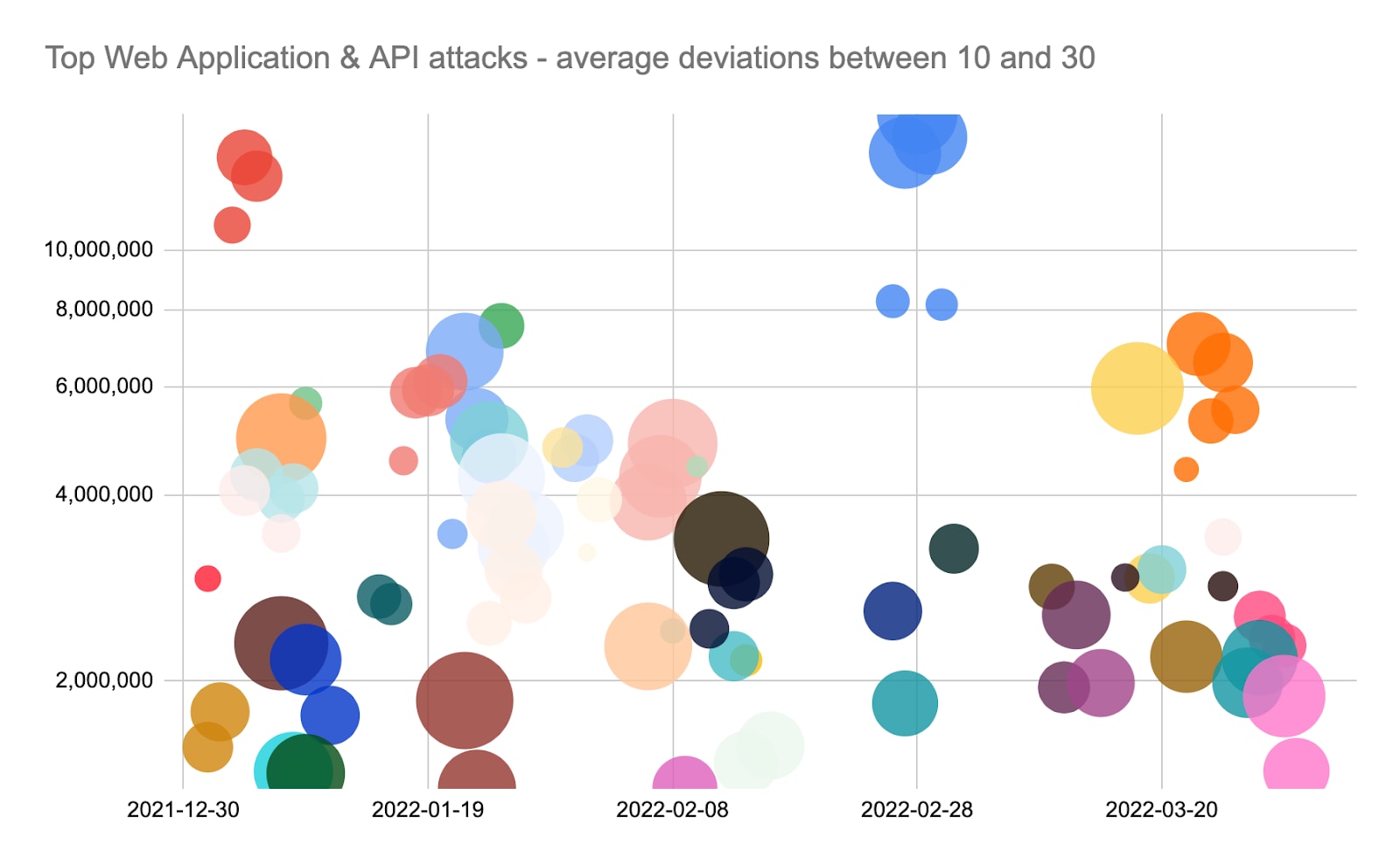
Pattern #3 — one-time attack campaigns
Finally, there are the big booms. The figure below shows customers with volumes of web application and API attack activity way beyond what they normally see, more than 30 times their norm. They’ll see one attack day (or maybe two, as the attack spills past midnight) at that huge multiplier and then the attack disappears. Outside of the increased number of customers being hit around the 02-08 timeframe, it’s quite random, making them very, very hard to predict, even more so than the short-burst pattern.

Call to action
Although we have myriad attackers out there with a variety of modi operandi, one thing is clear: Web application and API attack attempts are on the rise and reaching dizzying heights. There have been more than 6.3 billion attack attempts in YTD 2022 (up 3x from Q1 2021). Attackers are working hard to infiltrate your systems, steal your data (and your users’ data), cripple systems, and generally wreak havoc.
As noted in the pattern discussion above, attackers can leverage long-term persistence, short attack flurries, or surprise one-time attacks. We continue to see attempts to exploit blockbuster unpatched vulnerabilities like Log4Shell and we assume we’ll see the same from Spring4Shell. Although we may not be able to predict how an attacker will exploit web application and APIs next, this is further proof that we need to do all we can to stay current with patches (as is laid out in our blog post on Microsoft’s April 2022 Patch Tuesday) and ensure proper protections are in place (with web application firewall rules updated and in deny mode).
In addition to protecting our current customers, Akamai threat researchers continue to analyze data daily to look for signs of new vulnerabilities and zero-day attacks. If you’d like to talk to us about our research, we would love to hear from you! You can reach us through the Contact Us page, or tweet us at @Akamai_Research.



