Attack Campaigns Ramp Up for Organizations Down Under

DDoS and AppSec attacks impacting the ANZ region (Australia and New Zealand) have been in the headlines of late, with high-profile organizations seeing prolonged outages and leading to speculation as to whether the region is being specifically targeted. Let’s take a closer look at the types of attack vectors and malicious activity we’ve seen focused on customers Down Under.
Recent ANZ DDoS activity
A few of the regional customers we protect with Prolexic infrastructure defense were targeted with attacks upward of 100 Gbps over the past several weeks, mainly across the Financial Services sector.
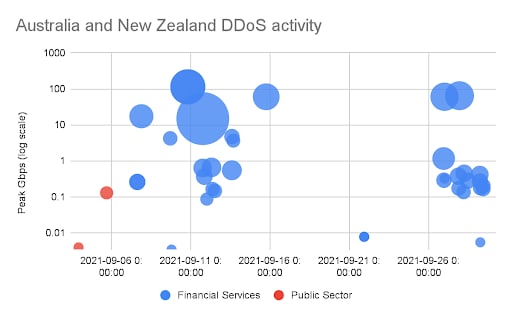
As has become typical, because attackers seem to want to avoid customers already under our protection, we heard about more of these DDoS attacks from new customers needing emergency integration defenses. Prior to onboarding, these new customers saw significant data center outages in addition to attackers targeting DNS infrastructure. In several instances, existing DDoS protections from both on-premises device manufacturers and other cloud-based DDoS providers failed, leaving these organizations to scramble to deploy more robust defenses amidst outages.
Combined with the advent of the Meris botnet and middleware amplification attacks of late, security and network leaders grew increasingly concerned with potential impending attacks around the corner, and they proactively onboarded additional internet-facing assets to reduce risk. As is the case with many of our emergency integration situations, once customers were behind Prolexic defenses, the attackers moved on to pursue their criminal endeavors against softer targets.
ANZ DDoS extortion
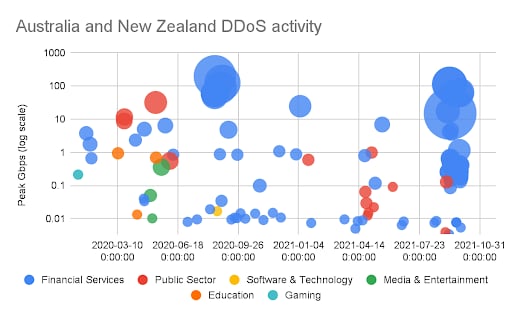
As we look back at our data over the past two calendar years, we see DDoS activity is not novel to both Australia and New Zealand. In fact, last summer we were discussing the resurgence in global DDoS extortion campaigns where the NZ Stock Exchange was one of the first victims publicly hit by threat actors (and taken offline repeatedly until Akamai protections were in place).
Since January 2020 and in aggregate for the region, we’ve seen wide-ranging DDoS attacks in terms of size and duration striking the Financial Services, Gaming, Public Sector, Education, Media & Entertainment, and Software & Technology sectors. Looking at the data, the frequency, size, and distribution of attacks is relatively stable — targeting of ANZ customers is not new.
It leaves us wondering whether the less interconnected internet infrastructures of the two island nations are both more susceptible to DDoS attacks and hence more often targeted. As we’ve observed over the past year with other attack campaigns, threat actors will conduct thorough reconnaissance of internet-facing infrastructure and aim their assaults at uncovered or perceived blind spots.
ANZ AppSec activity
If we pivot to application security (WAF), massive upticks in attacks can be seen starting in May 2021. Several large attack campaigns against Software & Technology (SQLi, XSS), Sports (SQLi), and Financial Services (SQLi, LFI, PHPi, CMDI, JSi, MFU, XSS) were observed.
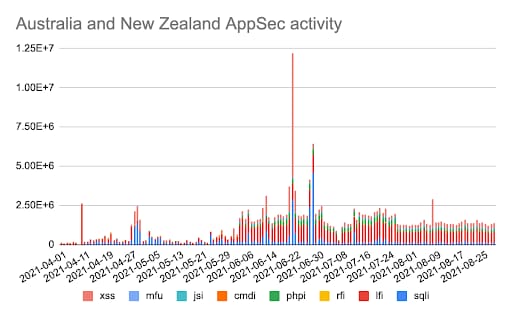
A trending increase in the daily number of AppSec events can be seen going back to mid-2019. This steady surge in activity is continuing to hold strong across multiple attack vectors.
ANZ bot activity
On the bot side, we can see acceleration in login/checkout abuse activity starting in early July and then taking off in late July. This was driven by relentless bot attacks (know_web_automation_libraries) against a Gambling customer. Perhaps the criminals were attempting to brute-force logins or conduct credential stuffing attacks in an attempt to drain customer funds used to place bets.
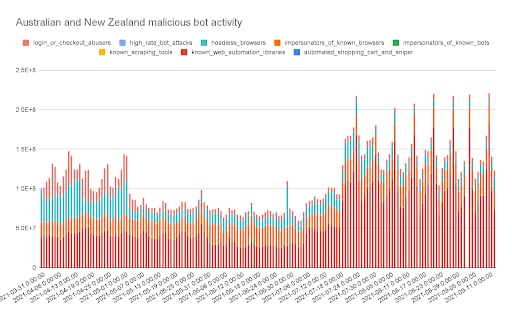
This jump shows bot activity can be a significant threat to anyone in the region. Bot activity can blow up usage-based costs (bandwidth, compute) and can also increase costs (direct and indirect) due to inventory hoarding, gift card and credit card checking, web scraping, and account takeover (ATO) fraud.
In particular, threat actors rely primarily on bots to scale their attacks as they move through the Weaponization stage of the ATO kill chain. A significant uptick in bot activity could be an indicator that an organization is being targeted via credential stuffing efforts to test and validate post-breach combo-lists obtained from the underground economy — the dark web. Once validated, these stolen credentials will be leveraged by criminal gangs to move into the Exploitation and Action phases, leaving organizations to deal with potential financial fallout from compromised user accounts. Blocking malicious login and checkout bots early is one way to fight back.
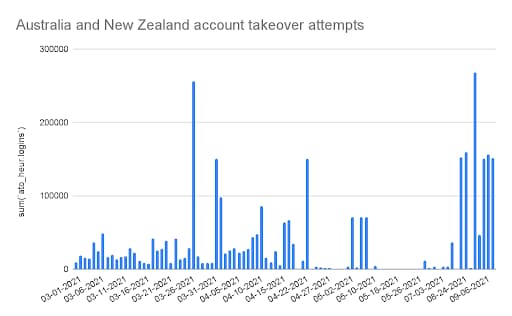
And while credential stuffing and ATO attacks happen at login, there are other significant attacks, such as inventory hoarding and credit card/gift card checking and abuse, among others. Clearly, bot operators continue to scale up as they attempt to disrupt web-facing assets.
Our recommendations
With the low barrier to entry to launch attacks spanning AppSec and DDoS to malicious ATO fraud campaigns, today’s organizations have to remain hypervigilant to evolving threat vectors.
And while the size of the DDoS attacks targeting the ANZ region weren’t chart-topping per se (several peaked at 100+ Gbps, which we regularly mitigate), several high-profile organizations throughout the region did experience widespread outages before routing onto Prolexic for emergency protection. It’s an important reminder that DDoS is back and remains a problem as long as threat actors continue to successfully circumvent less robust controls.
Regardless of which high-value internet and/or web-facing assets you are trying to protect, at the end of the day, the time to strengthen your security posture is now, not after you’re on an attacker’s radar.



