Akamai and the Adoption of Post-Quantum Cryptography

On the internet, we all take advantage of cryptography on a daily basis. The Transport Layer Security (TLS) protocol is used to secure the overwhelming majority of web traffic by encrypting our communications in transit, by validating the integrity of the data transmitted, and by asserting the authenticity of the services with which we interact.
The underlying cryptographic protocols and algorithms rely on computationally expensive mathematical operations to provide these protections, with their respective resistance to attacks generally being proportional to the time and effort it would take to break them.
Traditional computers vs. quantum computers
To perform these calculations, today’s computers, from the smallest Internet of Things (IoT) devices to the largest supercomputers, rely on semiconductors that operate on electrical signals in one of two states: on (or 1) and off (or 0), represented as a binary digit or a bit.
Advancements in technology have made the computer running on your desk or in your hand capable of executing trillions of operations per second. Ultimately these operations are all being performed using the finite bit states of 1 or 0.
In recent years, a new type of computer has entered the playing field: so-called "quantum computers." Unlike classical computers, these systems use a quantum mechanical approach to computing by operating not on traditional bits, but on quantum bits, or qubits. Qubits can represent, in principle, infinite states at the same time; they are said to exist in a superposition of its two basis states (Figure 1).
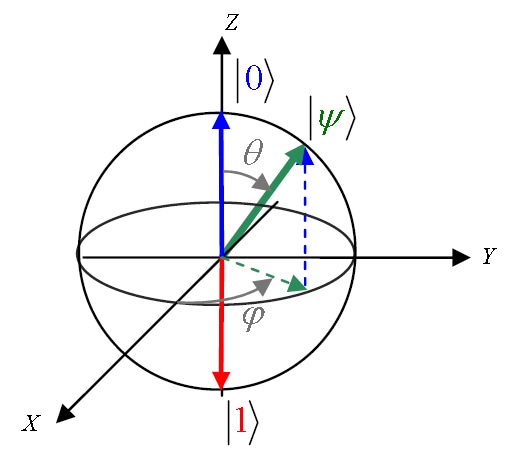
Fig. 1: A Bloch sphere representation of the possible quantum states of a single qubit: a classical bit could only be at |0> or |1>, while a qubit could be found on any point of the surface (Source)
Simplified, this means that quantum computers could be used to probe many different possibilities at the same time, dramatically increasing computational power and reducing the time complexities of traditional algorithms compared with traditional computers. This could effectively lead to quantum computers solving mathematical problems in the blink of an eye — problems that would take a classical computer millions of years to compute.
Preparing for the future
Much of this is hypothetical, as the field of quantum computing is still relatively young — the first applications of quantum theory to the field of computers date back only to the 1980s. However, as the technology rapidly advances, the general availability of reliable quantum computers is indeed only a question of time.
This increase in computational power presents a potential major impact to how we secure our data and communications. It is for that reason that Akamai tracks the ongoing and, at times, ground-breaking developments in quantum computing with great interest as we actively prepare for the wide adoption of this new technology.
Current challenges
Several countries and many companies are working on building quantum computers. But there are some key challenges that they all face, as successfully applying algorithms to quantum computers requires qubit stability — any outside impact from, say, light, vibration, or magnetic fields, can collapse the qubit’s superposition into a classical state.
In practice, quantum-based computations must be completed in microseconds, before the quantum mechanical properties of the qubits deteriorate (a condition described as "quantum decoherence"). This presents challenges in creating quantum computers, as well as in optimizing algorithms to run on them.
There are other engineering and technological distinctions to building quantum computers:
Quantum computers are based on quantum mechanics, not boring old semiconductors. Exploiting quantum mechanical properties allows us to exponentially advance compute power, and drastically affects how we view current algorithms and their security relevant properties. (And we haven't even mentioned quantum entanglement!)
Quantum computers can be built in different ways (see Figure 2 for an example); current approaches include the use of superconducting Helium-3, utilizing the 1/2 spin of this fermion to realize the quantized motional states. This is very exciting if you have even a passing interest in physics.
In order to minimize quantum decoherence and retain the quantum mechanical properties, quantum computers need to be chilled to −273 Celsius, almost absolute zero. That's pretty cool!
Due to these requirements, most of the physical equipment, such as certain superconducting cables, are very expensive, and scaling such systems and their operations remains a challenge with ample opportunity for breakthroughs.
 Fig. 2: Interior of an IBM Quantum System One (CES 2020) (Credit: IBM, unmodified, CC BY-ND 2.0)
Fig. 2: Interior of an IBM Quantum System One (CES 2020) (Credit: IBM, unmodified, CC BY-ND 2.0)
Future challenges
The first quantum computer, created in 1998, could operate on two qubits; today, the largest quantum computer in the world can operate on 433 qubits. But to do really useful work, quantum computers will need 1,000 or even 4,000 qubits. Researchers in both the government and private sectors are allocating significant resources to make this a reality in the next few years.
At the same time, there is an incredible amount of research in the area of quantum algorithms and their use in cryptographic applications. This research is creating new thinking on how to secure data for the long term.
Algorithms that are considered secure today, based on existing computational limits, may suddenly become trivially broken with the advent of practical quantum computers. Certain capable (and forward-looking) adversaries may already be collecting encrypted data and communications with a goal of using quantum computers to decrypt them in a few years' time.
For this reason, it is critical for both commercial and governmental organizations to begin preparing now for a post-quantum world.
How do quantum computers affect today’s cryptography?
Cryptographic algorithms apply complex mathematical problems for the protection and integrity of sensitive data. For example, the widely used RSA public-key encryption scheme (named after its inventors, Rivest, Shamir, and Adleman) relies on the difficulty of finding the factors of the product of large prime numbers.
Elliptic-curve cryptography (ECC) (which in recent years has found widespread adoption due to its notably smaller key sizes at similar or better security properties than RSA) depends on point multiplication and finding the discrete logarithm of a random elliptic curve.
Both of these problems currently take exponential time to compute: increasing the key size by just one bit doubles the time it takes to perform the computation for a classical computer. RSA, the Elliptic Curve Digital Signature Algorithm (ECDSA), as well as the Diffie–Hellman (DH), and the Elliptic Curve Diffie–Hellman (ECDH) key exchange algorithms all exhibit these cryptographically desirable properties.
A quantum computer, on the other hand, can solve these problems in polynomial time, meaning to double the time needed to break a key, you now have to double its size. In 1994, American mathematician Peter Shor developed a quantum algorithm that completes integer factorization in polylogarithmic time: Using Shor’s algorithm, a 2,048-bit RSA key that would take a traditional computer trillions of years to brute force could conceivably be factored in just a few seconds with a 4,000-qubit quantum computer.
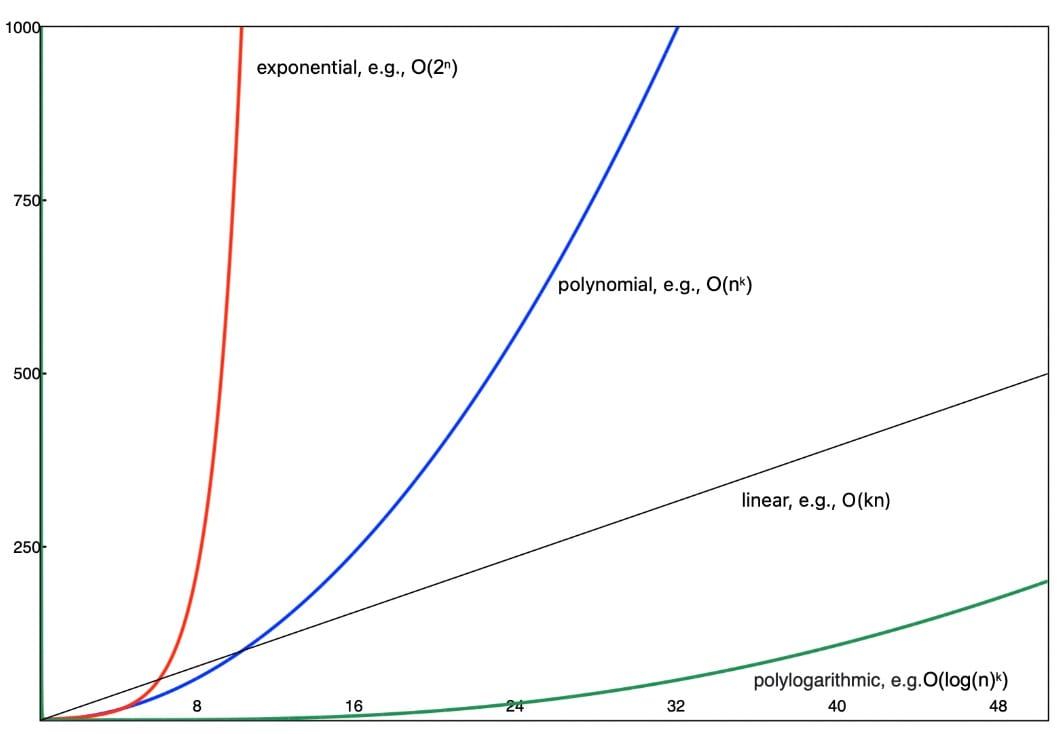 Fig. 3: Comparison of computational complexity of algorithms using Big-O notation
Fig. 3: Comparison of computational complexity of algorithms using Big-O notation
Other cryptographic algorithms, such as the SHA-2 hash function or the symmetric Advanced Encryption Standard (AES) do not rely on the same mathematical properties described above. Although quantum search algorithms, such as Grover's algorithm, may speed up unstructured search to some degree (and thus facilitate attacks on symmetric encryption and hashing), the work required remains proportional to the key size. That is, if a sufficiently large key is selected, these algorithms are generally considered "quantum safe."
Q-Day: What is the industry doing to prepare?
The information security industry and governments around the world are working to prepare for “Q-Day” — the day that a quantum computer will be capable of breaking today’s cryptography, potentially exposing confidential information and encrypted communications.
In 2016, the U.S. National Institute of Standards and Technology (NIST) kicked off an open “competition” to find the algorithms that are resistant to quantum algorithms. After six years of multiple rounds of research, analysis, and selection of candidates, NIST approved the following algorithms in 2022:
The lattice-based Cryptographic Suite for Algebraic Lattices (CRYSTALS) public-key encryption (PKE) / key-encapsulation method (KEM) named Kyber
The lattice-based CRYSTALS Dilithium signature algorithm
The Fast-Fourier lattice-based signature algorithm FALCON
The hash-based SPHINCS+ signature scheme
However, as cryptographic and computing researchers continue to investigate these algorithms, it’s possible that any weaknesses in them will be exposed. During the selection process, some earlier candidates were quickly broken, while others were shown to be vulnerable to different types of attacks and had to be modified or eliminated.
Preventing attacks from future quantum computers
As these standardization processes are ongoing, implementations of the prospective and selected candidates have begun to appear. Keep in mind that these algorithms are intended to be used on today’s computers to prevent attacks from tomorrow’s quantum computers. These are implementations of quantum-safe algorithms and do not themselves perform any quantum mechanical calculations, nor do they require a practically usable quantum computer.
Several noteworthy open source tools already provide sample implementations of the NIST-approved algorithms:
The Open Quantum Safe project provides an open source C library and prototype integrations with popular libraries and applications, such as OpenSSL and OpenSSH, as well as demo integrations with Apache httpd, nginx, curl, and others.
Bouncy Castle, the leading open source cryptography provider for Java and C#, has implementations of all the current NIST-approved algorithms.
In addition to these implementations, there are efforts underway to examine the use of hybrid cryptography; i.e., the use of both pre- and post-quantum algorithms simultaneously. The Internet Engineering Task Force (IETF) has many drafts on how to do this and is experimenting to see which algorithms work for which uses.
Regardless of which approach is ultimately accepted and approved, it will take the industry some time to adapt. The algorithms that are selected must be able to be run with reasonable performance on today’s computers, and be able to handle millions of internet transactions every second. They will also need to withstand the efforts of researchers and attackers to find weaknesses in their implementations.
Keeping up with advancements in post-quantum cryptography
Although the general consensus in the industry is that we’re still several years away from “Q-Day,” Akamai is not content to sit idly by and wait for it to come.
Akamai’s goals of powering and protecting life online depends heavily on the ability to keep end users and customers safe. Cryptography plays an important role in this — from encrypting customer data to following the industry standards that protect billions of internet transactions every day. Akamai is therefore very interested in keeping up with the advancements in quantum computing and their impact on today's cryptography.
It is critical for organizations to understand exactly where post-quantum cryptography (PQC) will impact them. As noted above, not all cryptographic algorithms are equally impacted, and organizations will need to have a complete understanding of what libraries and implementations are used across all of their systems.
Transition steps
In November 2022, the White House published a memorandum outlining required steps for U.S. agencies to prepare for a transition from traditional to post-quantum cryptography, which prioritizes the inventory of all cryptographic systems.
Akamai is committed to the safety of our customers, their end users, and their traffic. Therefore, we comply with various information security programs, such as FedRAMP, ISO, and SOC2. As a result, we are already following the recommendations in this memorandum as we are assessing the impact of quantum computing within our technology stack.
Akamai's internal Cryptography Group of subject matter experts is closely following the progress of the post-quantum algorithm selection process being led by NIST, and has begun experimenting with the open source implementations available today. We’re also actively involved in the IETF and are monitoring updates on plans to support hybrid cryptography.
Learn more about an upcoming beta program
When the industry and the IETF are close to standardization of post-quantum cryptography ciphers for TLS, and those ciphers have been implemented in TLS libraries, Akamai plans to offer an opt-in beta program to enable post-quantum cryptography ciphers on edge certificates. Please reach out to your account team if you are interested in participating in this upcoming beta program.
Looking ahead
It is an exciting time to be in this field. We appreciate the challenge of aligning the practical requirements and implications of serving billions of users with the performance and security guarantees that our customers expect in a rapidly changing ecosystem.
Akamai continues to participate in the community and keep our finger on the pulse of the latest research, but not get ahead of the standards before they are defined. With our rich experience in securing our customers' traffic and data, we are well-prepared to adopt quantum-safe algorithms when the industry is ready to move.
Thanks to Rich Salz of Akamai who wrote the first draft of this blog post.




