Protect and Elevate Your DNS with Akamai Shield NS53
Introduction
Akamai offers a comprehensive suite of Domain Name System (DNS) solutions to help domain owners achieve performant resolutions, highly secure zones, and scalable workflows. However, DNS hosting and operational requirements are often nuanced since the protocol allows for a variety of implementation strategies. Luckily, the Akamai DNS portfolio is specifically designed to meet diverse and complex use cases.
- Akamai Edge DNS is a distributed denial-of-service (DDoS)–resilient, authoritative DNS platform that supports both primary or secondary zone management models, so customers can administer and manage their zones either in Edge DNS or via an existing provider.
- Akamai Global Traffic Management is a fault-tolerant, DNS-based load balancing service that makes intelligent routing decisions based on real-time data center performance, health and global internet conditions.
- Akamai DNSi is Akamai’s carrier-grade, private recursive DNS resolver that doubles as a highly flexible and extensible services platform.
Processing more than 13 trillion DNS queries every single day, Akamai DNS boasts an industry-leading 100% uptime SLA and one of the largest, distributed DNS platforms in the world. With Akamai, domain owners have a comprehensive solution set that can be seamlessly incorporated into their architecture with the confidence that their applications will continue to scale and remain resilient.
To complement this robust collection of products, Akamai continues to develop new, innovative solutions so admins can further optimize DNS server workflows and meet the challenges of an ever-evolving cybersecurity landscape.
The challenging DNS attack landscape
One of the more pernicious attack vectors in today’s threat landscape is DNS flood attacks, which attempt to exhaust the resources of nameservers, global server load balancers (GSLBs), or firewalls by sending an overwhelming number of illegitimate DNS queries. A common flood technique is an NXDOMAIN attack, in which malicious actors trigger excessive requests for nonexistent hostnames (e.g., www.doesnotexist.example.com). These queries consume an authoritative nameserver’s resources while exhausting a recursive resolver’s cache pool. A successful DNS flood attack can thus increase resolution times for legitimate queries or even achieve an outright denial of service (DoS).
Difficult to block
DNS flood attacks are becoming increasingly popular for threat actors since this traffic can prove difficult to block without disrupting legitimate queries. Authoritative nameservers often only have visibility into the resolver’s IP address so denying or rate limiting traffic on the basis of IP may introduce false positives since resolvers facilitate traffic for true end users as well.*
*Extension mechanism for DNS (EDNS0) offers no reprieve since the extension only advertises the true end user’s subnet.
Difficult to isolate
Additionally, volumetric DNS attacks can be difficult for Layer 3 or Layer 4 DDoS scrubbing centers to successfully isolate since DNS DDoS queries often advertise relatively low bits per second (bps) or packets per second (pps) rates compared with overall traffic.
Cost-effective
Along with being particularly challenging to mitigate, DNS flood attacks are also often a cost-effective DDoS strategy for attackers. A DNS request is a relatively small artifact, and therefore issuing volumetric DNS queries at scale is often less computationally expensive than other malicious traffic types.
More ubiquitous
Finally, application owners often allocate more bandwidth and security resources toward fortifying other digital infrastructure assets, like web servers, application servers, and databases — often leaving DNS components inadequately protected or uniquely exposed.
As a result, these attacks are becoming more ubiquitous. Figure 1 shows how DNS-based DDoS attacks more than doubled between the first quarter of 2022 and the fourth quarter of 2023. According to Akamai’s threat intelligence, more than 64% of the total DDoS attacks in the fourth quarter of 2023 had a DNS component. Of these DNS attacks, more than 50% were DNS resource exhaustion attacks.
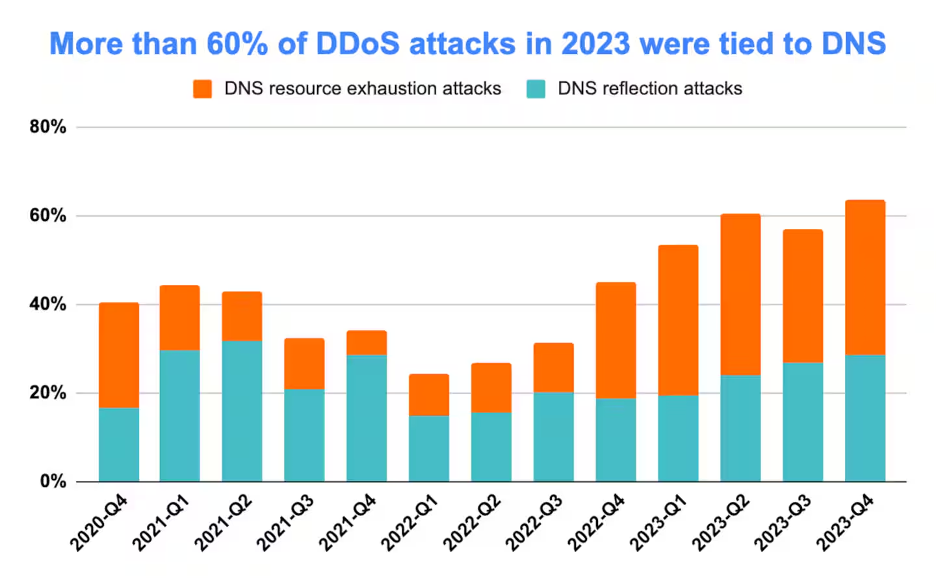 Fig. 1: More than 64% of DDoS attacks in the fourth quarter of 2023 had a DNS component (Source: Akamai DDoS threat intelligence)
Fig. 1: More than 64% of DDoS attacks in the fourth quarter of 2023 had a DNS component (Source: Akamai DDoS threat intelligence)
Akamai Shield NS53
In response to these trends, Akamai has launched Akamai Shield NS53, a geographically distributed DNS caching proxy service that allows an authoritative DNS server (e.g., on-premises nameservers or GSLBs) to remain in the resolution flow for an extra layer of protection. With Shield NS53 in place, the Akamai DNS network will respond to queries from recursive DNS resolvers to offload answers from an authoritative source. If the response is not in cache, the query will be forwarded to an “origin” nameserver to retrieve the record (Figure 2).
A subsequent request for the same record will be returned from that Shield NS53 node’s memory, assuming the query arrives before the duration of the assigned time to live (TTL).
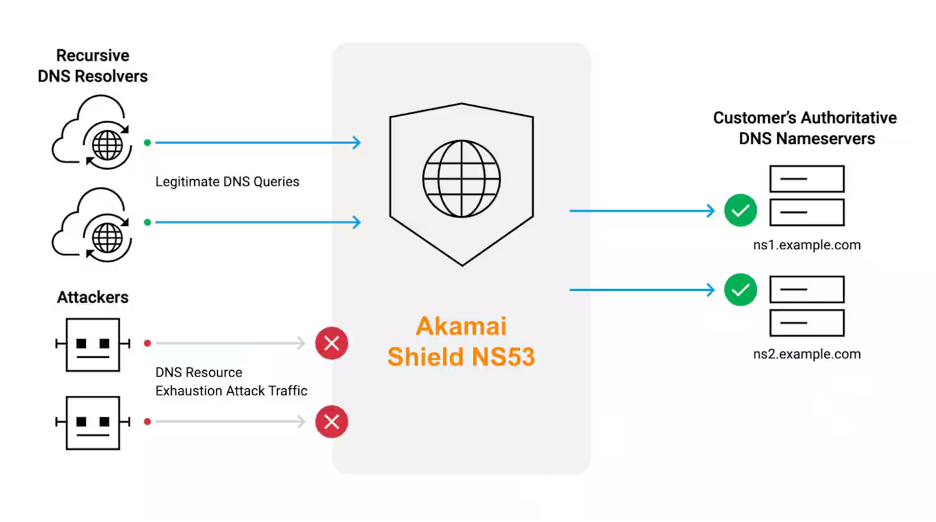 Fig. 2: Akamai Shield NS53 is a bidirectional DNS proxy solution that protects key components of your origin DNS infrastructure from NXDOMAIN attacks
Fig. 2: Akamai Shield NS53 is a bidirectional DNS proxy solution that protects key components of your origin DNS infrastructure from NXDOMAIN attacks
In simplified terms, Shield NS53 is like a content delivery network (CDN) for your DNS infrastructure, which is an enticing option for customers who want to enjoy the benefits of the scale and resilience of Akamai’s DNS solutions, while fortifying and protecting existing, on-premises DNS assets. DNS providers or on-prem nameservers often don’t support zone transfers, which eliminates the possibility of a secondary model with Edge DNS. Even if asynchronous full transfer zone (AXFR) requests are supported, many domain owners prefer to rely on existing nameservers to field end-user queries but may require a caching proxy to offload bandwidth from their infrastructure.
Both of these use cases, and countless others, are perfect candidates for Shield NS53, a product that further expands the architectural possibilities for network administrators looking to improve their DNS security posture.
Protection from DNS DDoS attacks
Shield NS53 offers robust DDoS protection from a variety of DNS attacks including DNS flood, DNS water torture, and others. As with Edge DNS, Shield NS53’s impressive scale perfectly complements anycast's innate DDoS resilience, thereby ensuring that the platform seamlessly absorbs large-scale volumetric DNS attacks.
In addition, Shield NS53 supports customer-specific dynamic security policy configurations, including rate limits on incoming and outgoing traffic to temporarily drop excessive resource load and block any resolver or client that’s requesting records at an anomalous rate. And while there is minimal risk that end-user queries may be temporarily blocked when an offending client is placed in the penalty box (since resolvers are public machines), network administrators can dynamically configure rate limits based on their own baseline traffic to minimize false positives.
Along with rate limiting malicious traffic, Shield NS53 is designed to significantly reduce authoritative origin load via the caching mechanisms outlined in the prior section. This service can also be configured to directly serve negative responses by establishing a strict “names allow list.” This way, only requests for valid records are potentially forwarded, preventing NXDOMAIN attacks from ever reaching authoritative origins, and domain owners have the flexibility to define this allow list via AXFR requests, the Shield NS53 portal, or the open API.
Performance
Shield NS53’s impressive DDoS protection is complemented by a variety of performance benefits. While a centralized model often requires queries to travel penalizing distances across the globe, Shield NS53 uses one of the most geographically distributed anycast networks to route traffic to the closest geographical server based on Border Gateway Protocol (BGP) routing tables. This networking technique thus reduces round-trip times by minimizing average distance vectors between resolvers and nameservers when a query is served directly from cache.
To improve the chances of a cache hit, Shield NS53 supports a variety of offload-maximizing features, including:
- Shield NS53 uses a tiered distribution architecture, which forces any cache misses to be forwarded to a second, more concentrated cluster of nearby Akamai nodes
- Asynchronous prefreshing allows Shield NS53 servers to update cache for an expired record via an offline, asynchronous call to the authoritative server so fewer end users experience the latency of a request forwarded to a customer origin
- Cache sharing enables Shield NS53 servers to proactively push a cached record to other Shield NS53 servers for more efficient cache reuse across the platform
Finally, domain owners can further reduce authoritative queries by tuning/increasing zone TTLs where possible, so records remain in cache for longer prescribed durations.
Health checks
Along with shortening distance vectors via caching, Shield NS53 can also optimize reliability and eliminate costly resolver retries when an authoritative server becomes unresponsive. Domain owners often delegate multiple nameserver records for a single name to avoid a single point of failure (SPOF). Although this is a recommended best practice, DNS performance will suffer if a resolver contacts a downed nameserver during the resolution process since an additional query will be required to successfully retrieve the desired record — not to mention the application will fail altogether if all the listed nameservers are down.
When a domain is delegated to Shield NS53, however, Akamai will perform health checks against each authoritative IP and automatically remove any problematic origins from rotation until they are back up. Shield NS53 can also “serve stale” to ensure DNS requests will continue to be fulfilled without interruption even if all authoritative endpoints are judged to be down. In terms of the resolver-to-Akamai queries, Shield NS53’s anycast posture and built-in network failover mechanisms ensure that no node is a SPOF in the extremely rare event that a Shield NS53 node is experiencing downtime.
Onboarding
Once you define your origin nameservers in the Shield NS53 portal, onboarding involves pointing both the domain’s glue records and the zone’s NS hostnames to Shield NS53 IPs.**
Zone file
Ns1.example.com 10800 IN A {Shield NS53 IPs} Ns2.example.com 10800 IN A {Shield NS53 IPs} |
Registrar’s delegation records
Authoritative nameservers
Example.com 10800 IN NS ns1.example.com Example.com 10800 IN NS ns2.example.com |
Additional records (glue)
Ns1.example.com 10800 IN NS {Shield NS53 IPs} Ns2.example.com 10800 IN NS {Shield NS53 IPs} |
**If the “origin” authoritative nameservers belong to a third-party provider, the domain owner will need to create new hostnames that point to Shield NS53 IP addresses (and reference these in the registrar’s records and the zone file) since the third party owns their own nameserver records.
After the deployment, domain owners can lock down their authoritative nameservers to only accept queries from Shield NS53–connecting IPs to eliminate the possibility that a malicious actor will hit these origins directly. In addition, many of the features referenced previously in this blog post are self-configurable and self-serviceable, including the rate control thresholds and mitigations, the health check settings, and the strict names allow list.
Advanced and actionable analytics are available in the portal that highlight the amount of queries absorbed by Shield NS53 and the ratio of positive to negative responses. And as with most Akamai solutions, Shield NS53 supports both a user-friendly interface and an easy-to-use API for programmatic updates.
The bottom line
If your DNS goes down, your online presence goes down — it’s that simple. It is therefore not surprising that cybercriminals have accelerated their attacks on the DNS infrastructure of businesses, institutions, government agencies, and critical public infrastructure. The challenge of protecting and ensuring the performance of your DNS assets gets elevated further when it is a mixed architecture with some components on-prem and others in the cloud. Rudimentary DNS firewalls do not provide adequate protection from motivated malicious attacks.
Akamai Shield NS53 offers a robust solution to protect your capital investment into on-prem DNS infrastructure and significantly improve performance by using one of the most distributed networks of anycast servers. The capabilities of Shield NS53 combined with Akamai Prolexic Network Cloud Firewall and Akamai Edge DNS can protect your entire digital infrastructure estate from DDoS attacks across all layers, ports, and protocols.
Explore more DNS-oriented solutions from Akamai
Everything Akamai deploys depends on our intelligent Akamai Connected Cloud platform, which expands to enable a range of services for domain owners. If you found this blog post useful, I invite you to continue your exploration.
- Learn how Akamai deploys Edge DNS with multiple vectors of global resilience in the Designing DNS for Availability and Resilience Against DDoS Attacks white paper
- Achieve domain stability and resilience with Akamai Edge DNS service
- Load balance your data centers, cloud deployments, and CDNs with Akamai's cloud-based GSLB solution, Akamai Global Traffic Management
- Scale your application with Layer 7 load balancing with Akamai App Load Balancer Cloudlet
- Turn your DNS resolver into a security tool with Akamai Secure Internet Access Enterprise along with DNSi and Secure Internet Access ThreatAvert solutions for internet and mobile carrier services providers.
Akamai's DNS solutions are API- and DevOps-aligned to enable cloud-to-cloud innovation, and DevOps professionals are always welcome to join our developer community.




