Akamai Blocked 419 TB of Malicious Traffic in a 24-Hour DDoS Attack
Executive summary
On July 15, 2024, Akamai prevented one of the largest distributed denial-of-service (DDoS) cyberattacks it has ever observed against a major financial services company in Israel.
The highly sophisticated, high-volume attack lasted almost 24 hours.
The attacker deployed larger-than-usual resources, indicating a serious risk for future attacks.
Other Israeli financial institutions reportedly suffered outages and downtimes on the same day, potentially due to the same type of attack and the same aggressor.
Anatomy of the attack
A sustained volumetric DDoS campaign started 8:05 UTC (10:05 AM local time in Israel) on Monday, July 15, 2024, and included a wide variety of attack vectors including UDP flood, UDP fragmentation, DNS reflection, and PSH+ACK, among others. In congruence with a rapidly growing trend, the DDoS attack originated from a globally distributed botnet.
Although we have seen bigger attacks in terms of peak levels of attack traffic, this attack on Akamai’s customer was also highly significant in size — from 300 to 798 gigabits per second (Gbps). The largest DDoS attack ever recorded by Akamai Prolexic, our DDoS network security platform, was 1.44 Tbps, and though this recent attack stayed below that peak level, it was clearly of remarkable strength; in fact, it is the sixth-largest DDoS peak traffic ever mitigated by Akamai Prolexic.
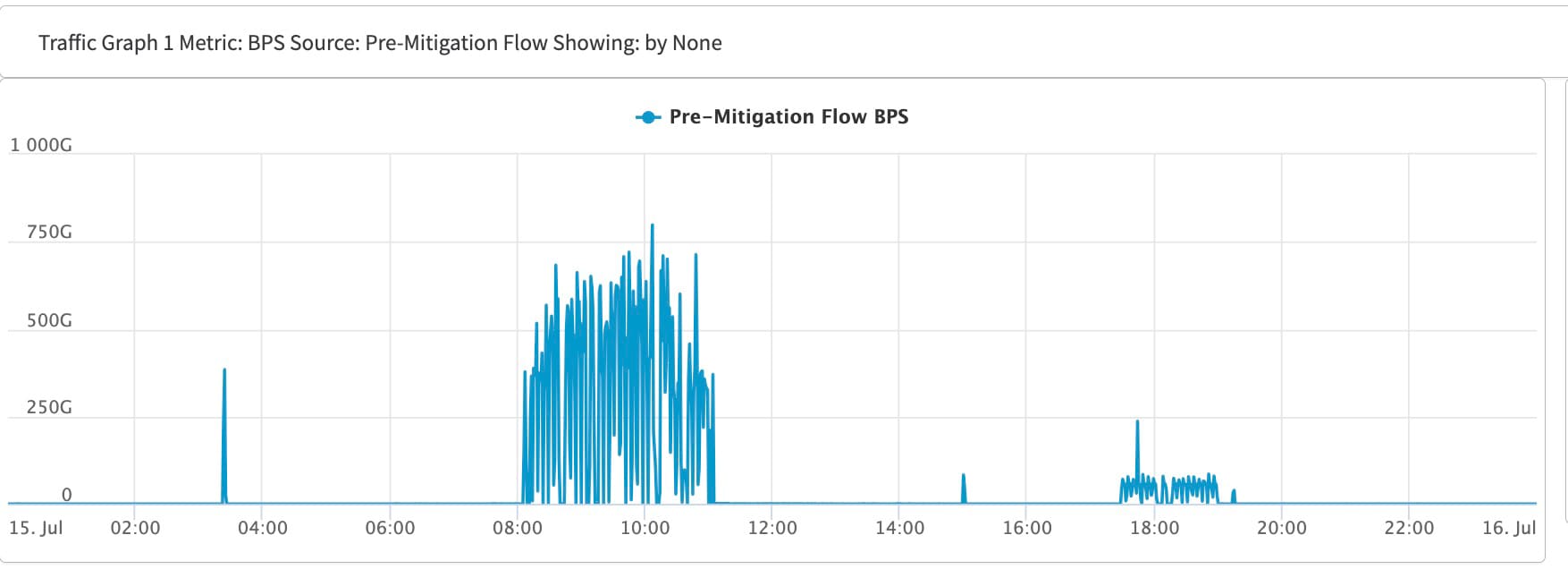
More important, this attack was a dedicated, sustained campaign that lasted almost the entire day. An initial small probing attack was followed by a three-hour attack window during which the total amount of attack traffic mitigated by Prolexic added up to a whopping 389 terabytes. For the entire attack duration of almost 24 hours, Akamai Prolexic blocked approximately 419 terabytes of traffic (Figure 1).
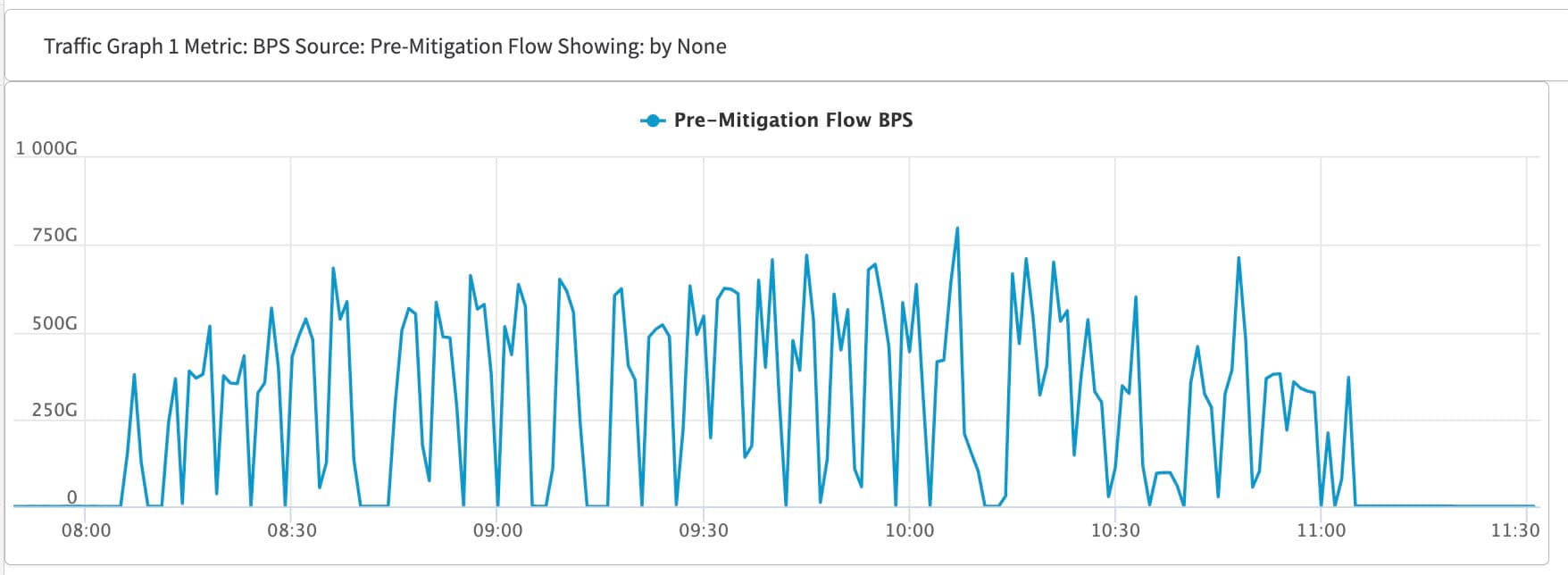
Most types of DDoS attacks are short-lived and often only last for minutes — for at least three reasons. First, if successful, even a short attack can bring down systems for a long time and cause significant damage by interrupting a company's ability to do business. Second, short attacks are more difficult for the victim’s defense systems and security engineers to analyze and react to. Last, but not least, short attacks make it much easier and cheaper for an attacker to rally the massive compute resources needed for a meaningful attack. The main attack window of this DDoS attack, however, was three hours long (Figure 2).
The attack resources typically come from large botnets of malware-infected computers that the attacker can control remotely and abuse for coordinated activities against an intentionally selected victim. Unlike many other forms of cyberattack campaigns in which a system or a company gets hit by coincidence, DDoS attackers make a conscious decision about who to go after.
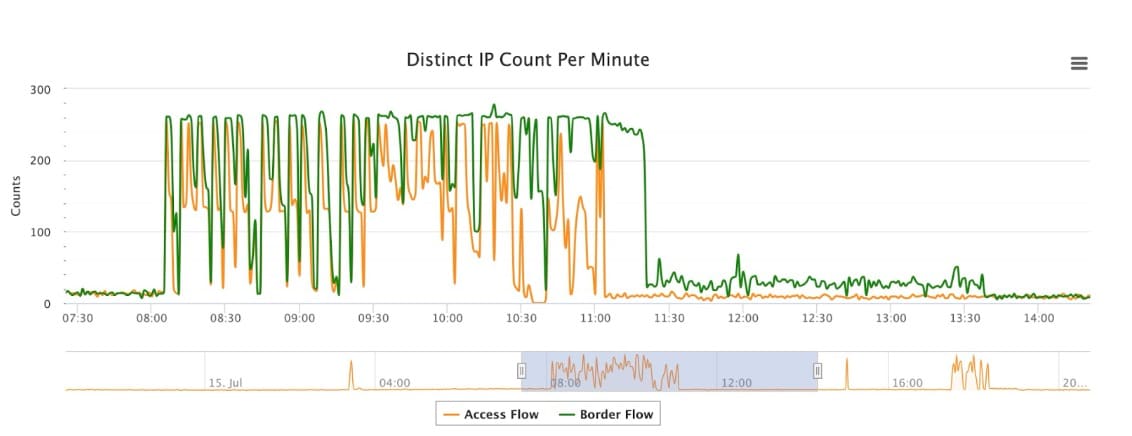
In this regard, the attack on July 15 was no exception: It originated from a globally distributed botnet that targeted more than 278 destination IP addresses simultaneously, making it a significant horizontal Layer 3 and Layer 4 DDoS attack (Figure 3). It seemingly was part of a purposeful, orchestrated wave of attacks on multiple financial institutions in one specific country.
However, this attack was very exceptional in terms of total duration. Sustaining such an intense high-volume multi-vector DDoS attack for an entire day is rare. This requires significant resources and is an indication of a very sophisticated aggressor.
A serious new DDoS threat
The attacker in this case obviously had significant resources at their disposal, both in terms of DDoS “firing power” and the time they spent controlling the attacking army of machines. This is even more remarkable as the same aggressor was potentially responsible for several other attacks during the same period.
This aggressor and their massive DDoS capability must be considered a very significant threat — after all, we have to assume that they are capable and willing to launch similarly potent (or even more potent) attacks on other targets, or to attack their recent victims again. The attacks observed in Israel tested and exceeded the defense capabilities of some cybersecurity vendors and DDoS protection solutions. The attacker may now have a much better understanding of who is vulnerable.
Israel under DDoS attack
According to Akamai’s internal DDoS threat intelligence, businesses and institutions in Israel have never witnessed more DDoS attacks than in 2024 — and the year is not yet over. The financial services customer referenced in this blog post has been repeatedly targeted with DDoS attacks since the fourth quarter of 2023, coinciding with the war between Israel and Hamas.
Over the past 90 days, the same customer has been targeted with 27 significant DDoS attacks, each time successfully mitigated by Akamai Prolexic. Before the record-setting DDoS attack on July 15, the largest attack on this customer had been clocked at 330 Gbps.
Who is most at risk of attack?
Although the DDoS attacks observed against financial institutions in Israel suggest a connection to the ongoing regional political conflicts, there is no way to make any predictions about who is more likely to be selected as a new victim should this actor decide to activate their botnets again and launch new attacks.
We should assume that the attackers still have the same resources that they deployed on July 15, and have perhaps even extended their botnets and evolved their attack efficiency since then.
DDoS attacks use the global internet, so we also have to assume that this aggressor is capable of directing unusually potent attacks against businesses and organizations anywhere in the world. Whatever the exact motives behind this attack were, the threat actor could well pick targets outside the Middle East and in verticals other than the financial industry.
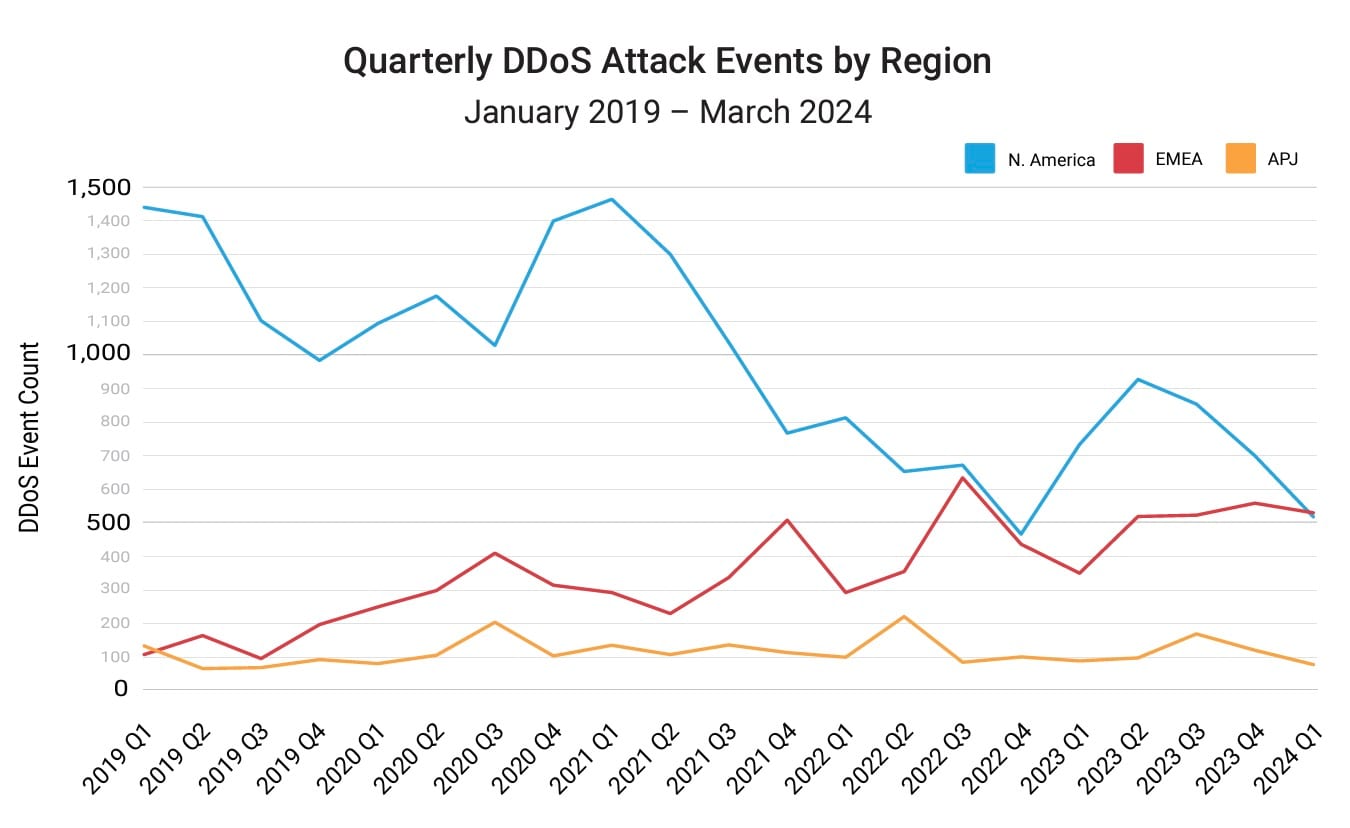
In the report Fighting the Heat: EMEA’S Rising DDoS Threats, Akamai researchers observed that the number of DDoS attack events in EMEA has been rising, with higher peaks, since the beginning of 2019. The researchers have analyzed regional DDoS data and are seeing EMEA’s DDoS attack event numbers moving at a steadier incline than any other region’s numbers, including North America’s, which leads overall (Figure 4).
Who is most at risk of severe impact from an attack?
From a technical standpoint, we consider organizations that only use certain appliance-based, on-premises DDoS defense systems without cloud backup capacity to be at higher risk of not being able to withstand the type of attack we saw on July 15. These solutions can have limitations in terms of how much attack volume they can handle while still allowing legitimate network traffic to get through.
Similarly, organizations that solely rely on the DDoS protection mechanisms of their hosting/service providers are more likely to be severely impacted by an attack of this nature. The concept of shared DDoS defense resources in multi-tenant environments often means that not enough defense capacity can be dedicated to an individual customer.
How to minimize risk
We advise businesses and organizations around the world to revisit their DDoS security posture and strengthen their defense systems to withstand attacks similar to the July 15 attack.
In fact, the Akamai customer that withstood the July 15 attack had re-evaluated their DDoS defenses and made the decision to switch to Akamai’s Prolexic platform out of concern about their earlier solution’s ability to handle large-scale attacks. Their forethought paid off as they were one of the only major financial institutions that didn’t experience sustained downtime during this attack wave.
The 6 steps we recommend to address the risk
Assess risk, including the existing DDoS mitigation services: Conduct a thorough and proactive risk assessment that involves your DDoS defense provider — specifically in terms of extremely forceful sustained attacks like the one described in this post, and whether your existing defenses are sufficient.
Review critical subnets and IP spaces, and ensure that they have mitigation controls in place.
Deploy DDoS security controls in an always-on mitigation posture as a first layer of defense to avoid an emergency integration scenario and to reduce the burden on incident responders.
Extend your security posture through an edge-based network cloud firewall beyond basic DDoS protection. A firewall at the edge of your network, in front of (and in addition to) your existing firewalls is a powerful, easy-to-deploy, and easy-to-use tool to quickly, centrally, and globally block traffic that you don’t want to hit your networks or certain targets within your networks. Akamai Prolexic provides a network cloud firewall as part of its DDoS defense capabilities that we consider a key defense capability.
Protect your DNS infrastructure from DNS-focused DDoS attacks. Ensure you have a robust authoritative DNS solution deployed, like Akamai Edge DNS, either in primary or secondary mode. If you have on-prem or hybrid DNS infrastructure, use a DNS proxy solution like Akamai Shield NS53, which can implement dynamic security controls to protect your network from DNS resource exhaustion (NXDOMAIN) flood attacks.
Develop an incident response plan and crisis response team: Proactively develop a comprehensive incident response plan that outlines the steps to be taken in the event of a DDoS attack. The plan should include roles and responsibilities, communication channels, and predefined mitigation strategies. Ensure runbooks and emergency contacts are up-to-date.
Contact us if you’re under attack right now or if you need Akamai’s help to future-proof your security.