Mitigating CVE-2021-41773: Apache HTTP Server Path Traversal

On September 29, Ash Daulton, along with the cPanel Security Team, reported a path traversal and file disclosure vulnerability in Apache HTTP Server 2.4.29 to the Apache security team. The issue was fixed within two days, under CVE-2021-41773, and the patch was released on October 4. Apache urges its users to deploy the fix, as the vulnerability is already being actively exploited.
The path traversal vulnerability allows attackers to read arbitrary files from the vulnerable server file system. Attackers can read sensitive system files or expose the source code, which might later lead to full system compromise.
The exploitation is possible only if files outside of the document root are not protected by the “require all denied” directive in the Apache configuration file.
<Directory />
Require all denied
</Directory>
First reproduction was reported on October 5 by PT SWARM and through a more detailed write-up by Rapid7, while several proof-of-concept exploits have been published since.
 Proof-of-concept exploits available on GitHub
Proof-of-concept exploits available on GitHub
Massive malicious activity
Exploitation complexity of this vulnerability is very low. Тhe early exploitation attempts we have detected are from September 20 from different IP addresses. As this is quite a common evasion, it is difficult to attribute those attempts to this specific vulnerability, but the Apache team has confirmed that the vulnerability was already exploited in the wild when they fixed it.
Most of the attack attempts are traversing the path with different depths and different sensitive resources, such as “/etc/passwd”, “/etc/host”, and “/windows/win.ini” to expose information that might lead to full system compromise.
Besides the path traversal variant in the initial PoCs:
/.%2e/.%2e/.%2e/
We have observed several additional variants attackers are trying for evasion:
/.%2e/%2e%2e/
Decodes to: /../../
While most of the variants use “.%2a” in all the path segments in the payload, it is enough to have only a single “.%2e” sequence to bypass vulnerable Apache’s normalization.
/.%2e%2f.%2e%2f
Decodes to: /../../
An attempt to replace “/” with a url-encoded “/” (%2f)
/.%2e%5c/
Decodes to: /..\/
An attempt to evade detection by escaping the “/” with “\/”, which will be normalized by the server just to “/”
And the strangest one, which will be unlikely to work on any system:
/.%2e.%2e/%2f.%2e.%2e/%2f.%2e.%2e/
Decodes to: /....//....//..../
The attack vector includes 4 dots in the segment. It seems the attacker hopes the server will somehow remove either the “.” or the “%2e” before/after decoding, eventually leaving only 2 dots to successfully go up the path, but still confuse the path normalizer. Without this assumption, this traversal attempt just won’t work:
The attacker is also using the double slash “//” evasion technique, which servers normalize to a single “/”.
As mentioned by Rapid7, @hackerfantastic demonstrated how this vulnerability could be “upgraded” to an RCE, while “mod_cgi” is enabled (not by default).
We have observed an IP address from India searching for SharePoint, Exchange, and other Windows-based systems (running on Apache?) to execute “cmd.exe” and list the content of the “c:\” folder (in alphabetical order)
GET /.%2e/.%2e/.%2e/.%2e/.%2e/./winnt/system32/cmd.exe?/c%20dir%20c:\%20/OG
While the query string decodes to: /c dir c:\ /OG
Just over the past 24 hours on our global platform, we have witnessed:
More than 237,000 unique attempts to scan and/or exploit this vulnerability
512 unique IPs involved in these attempts
4,343 unique hosts targeted
80% of attack activity targeted against Commerce, High Tech, Financial Services, and Social Media verticals
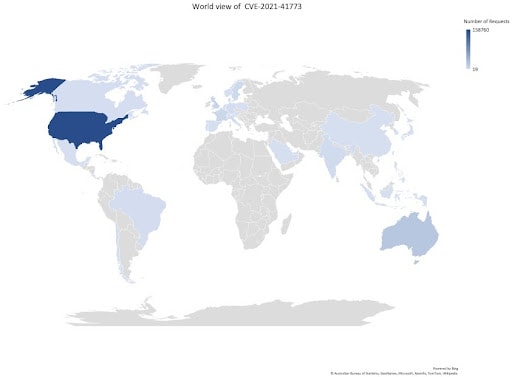
The majority of attacks originated from the United States
 Most-targeted verticals
Most-targeted verticals
Mitigating CVE-2021-41773 with Kona Site Defender (KSD)
Akamai’s threat detection ecosystem enables us to provide robust protections, including for many 0-day exploits, for our customers. Furthermore, Akamai’s vast and worldwide coverage gains its customers unprecedented visibility into threat intelligence, which is translated into protections. Our threat intelligence–based Client Reputation includes deeper protection layers such as scanning activity and client-requested anomaly detection, HTTP request compliance checks, and collection of KSD web attack rules to identify “weaponized” adversarial payloads.
Following is an example of a real attacker attempt to execute CVE-2021-41773 detected by existing Akamai KSD rule sets:
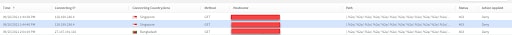
 A real attacker request targeting Akamai’s customer
A real attacker request targeting Akamai’s customer
 Attack detected by Akamai Kona Rule Set
Attack detected by Akamai Kona Rule Set
 Attack detected by Akamai Adaptive Security Engine
Attack detected by Akamai Adaptive Security Engine
Adaptive Security Engine is detecting and blocking the current CVE exploits based on existing rules in Local File Inclusion (LFI) Attack Group, specifically rule:
- 950203 - Local File Inclusion (LFI) Attack (Directory Traversal and Obfuscation Attempts)
While other LFI rules are also important to contribute to the group score, such the ones we see in the example attack above:
- 3000120 - Local File Inclusion (LFI) Attack (Common OS Files 1)
- 3000124 - Local File Inclusion (LFI) Attack (Common OS Files 3)
- 3000126 - Local File Inclusion (LFI) Attack (Common OS Files 5)
Automated Attack Groups is detecting and blocking the current CVE exploits based on existing rules in Local File Inclusion (LFI) Attack Group:
- 1000003 – Local File Inclusion (LFI) Attack Group
Kona Rule Set is detecting and blocking the current CVE exploits based on existing rules in Command Injection Attack Group:
- 950103 - Path Traversal Attack
Final note
Having a web application firewall as another layer of protection might buy you very precious time until a patch is deployed on the vulnerable server and significantly reduce the risk on your web applications, even in the case of a new 0-day.
The Akamai Threat Research team continues to monitor any new exploit variations of CVE-2021-41773 and will rapidly respond by providing rule updates and recommendations to customers.





