Akamai EdgeWorkers for SaaS: Balancing Customization and Security

Managing a large number of tenant configurations is a core challenge that software as a service (SaaS) and platform as a service (PaaS) providers must tackle. In this digital age, in which customization and security are paramount, the tenants of these providers demand tailored environments that are both secure and easy to change. They require the ability to modify settings from web application security to CDN options like caching time to lives (TTLs), custom response headers, content, and redirects — ensuring their services run optimally and securely.
Manage customized settings
To address these concerns, Akamai has developed an EdgeWorkers code bundle we call edge as a service (EaaS), which helps SaaS and PaaS providers manage a vast range of customized settings for their clients. By integrating EaaS with other Akamai products and features — such as Hostname Buckets, secure by default, Akamai EdgeKV, and Akamai EdgeWorkers — providers can easily cater to various tenant needs at a massive scale. This solution makes it far simpler for clients to deliver a tailored and secure service for unique applications, ensuring high-speed performance and reliability for their users.
EaaS also markedly reduces the time required to deploy changes. Configuration adjustments get reflected almost instantaneously, taking less than a minute through a single API POST to EdgeKV, which then rapidly disseminates across our global network. Finally, the EdgeWorkers EaaS code downloads and caches each tenant configuration within the EdgeWorker runtime on the fly, significantly reducing the time for updates to get reflected on our network.
One-time initial setup: 5 steps
There are five critical steps for setting up this new framework to help SaaS/PaaS providers scale their tenants' certificates and settings into the thousands with a single Akamai CDN and security configuration.
Create a new security configuration so any hostname applies to your security rules
Create a property manager configuration with Hostname Buckets using secure by default to scale hostnames and certificates into the thousands
Enable security configuration and populate security trigger information on your Property Manager configuration
Upload EaaS SDK bundle to EdgeWorkers and associate it to your Property Manager configuration
Create your first tenant configuration on Akamai EdgeKV service by uploading a JSON document with tenant settings with Akamai CLI or API
Two API calls to onboard a hostname in 10 minutes
The onboarding workflow highlighted below is efficient if your customer has already set up their Let's Encrypt validation settings. This workflow will provision a hostname, certificate, and all settings in approximately 10 minutes from start to finish (Figure 1). After adding the hostname, only one other API call is required to configure a tenant’s security and content delivery settings:
- Add new tenants to the host bucket by running HTTP PATCH with the new hostname
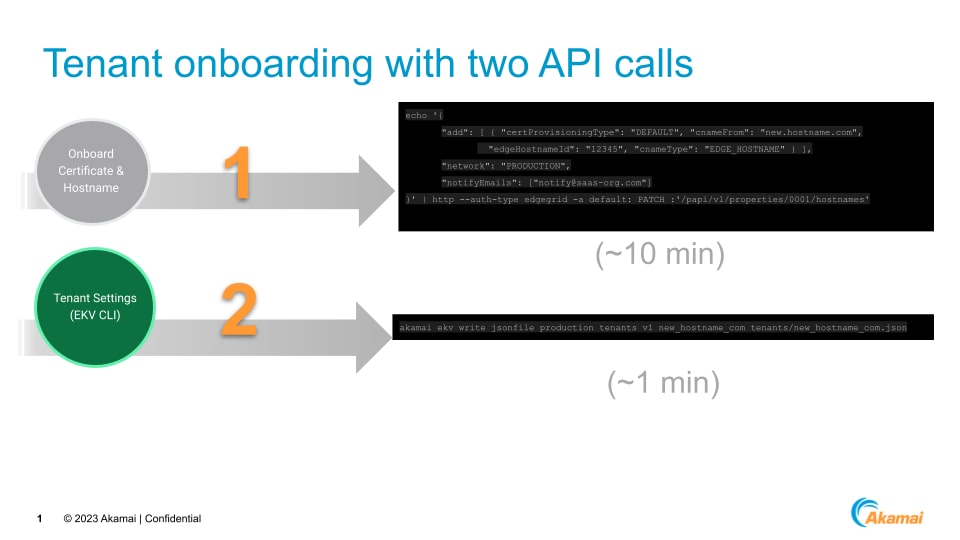 Fig. 1: The onboarding workflow: two API calls will onboard a hostname in 10 minutes
Fig. 1: The onboarding workflow: two API calls will onboard a hostname in 10 minutes
A sample tenant file
Figure 2 is a snippet of a JSON file containing security configurations and Figure 3 is a snippet containing delivery configurations. As Step 2 in Figure 1 demonstrates, the JSON file can be pushed to our EdgeKV.
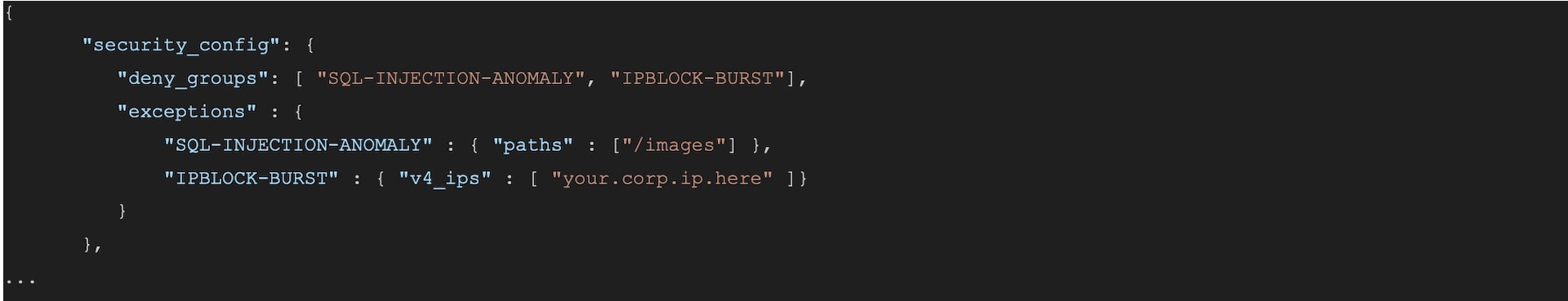 Fig. 2: JSON file containing security configurations
Fig. 2: JSON file containing security configurations
Security configuration
For this tenant’s security settings in the security_config section, we have only enabled Structured Query Language SQL injection (SQLi) and rate control protections while turning off SQLi protections for their “/images” path. This tenant also disabled IP rate controls for some IP addresses.
Delivery configuration
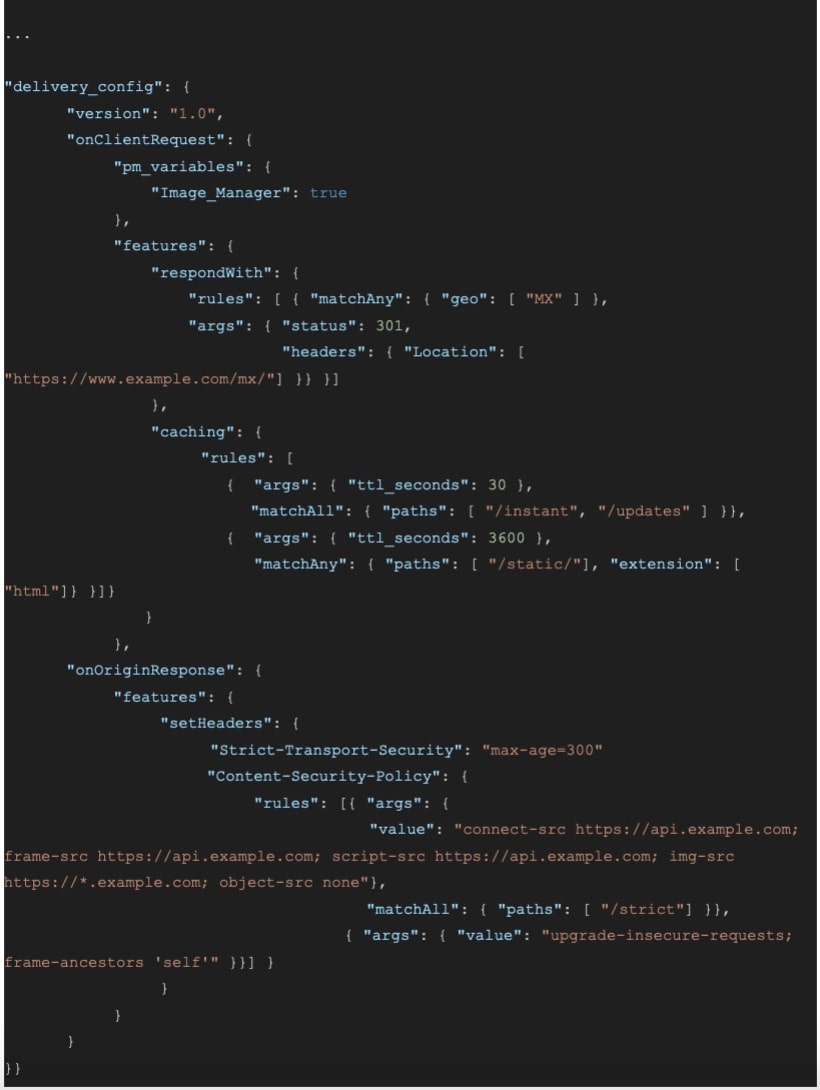
The delivery_config section has two subsections for tenant CDN control: pm_variables and features. The pm_variables subsection is the simplest feature flag use case where each tenant can have a unique set of Boolean or key/value flags to control the execution of Property Manager. This example tenant enables Image Manager by setting the corresponding feature flag value to true, so the Property Manager config will see this value and enable Image Manager accordingly.
Next, the features section provides the tenant conditional controls beyond basic feature flags. The design of the features schema was inspired by the power of the Property Manager’s rule tree without the recursive characteristics and keeping it consistent with the latest EdgeWorkers event model, response, and request nomenclatures.
Consequently, the schema directly interacts with the same underlying EdgeWorkers request and response objects, so arguments passed via the schema in Figure 3 are already documented. For this features section example, the tenant has configured custom redirects, caching rules, Strict-Transport-Security, and Content-Secure-Policy headers. Each instance has conditional criteria to execute this logic, but each can work without any conditions if you want the same behavior for each request.
Give it a try!
Akamai SaaS customers need best-in-class security and CDN delivery performance for their tenants. With this design pattern, they’ll benefit from capabilities at scale for the biggest SaaS and PaaS providers. If you want to give it a try, please contact your Akamai account representative, and they can help you get started.