Slipping Through the Security Gaps: The Rise of Application and API Attacks
Executive summary
The rising number of web application and API attacks contributed to an approximately 2.5x growth in the amount of attack traffic identified. This volume is likely driven by both the widespread adoption of APIs and increase in threat activity.
The threat vector driving the most growth in web application and API attacks is Local File Inclusion (LFI). These attacks are on a massive upswing with 193% year-over-year growth, which is a 3x surge from 2021.
API attacks directed at the business logic of the API are complicated to detect and mitigate. Consequently, they are challenging to determine at the individual request.
Emerging attack vectors like Server-Side Request Forgery (SSRF) and Server-Side Injection Template (SSTI) will continue to pose serious threats to organizations in the years to come. Attackers used SSTI techniques in conjunction with critical zero-day vulnerabilities, such as like Log4Shell and Spring4Shell, which led to remote code execution.
Critical industries (e.g., manufacturing) that do not typically have to deal with the same volume and scale of API requests as direct-to-consumer verticals (e.g., retail) are seeing a surge in attacks.
In our latest State of the Internet/Security report, Slipping Through the Security Gaps: The Rise of Application and API Attacks, we look at attack trends based on web application and API traffic analysis, critical vulnerabilities, and risk by industry. We also incorporated best practices and mitigation strategies with our research findings to produce this report.
Gaps in API and application introduce vulnerabilities and present opportunities for exploitation from attackers looking for ways to breach your perimeter, propagate inside your network, and obtain confidential information. And as web apps and API attacks remain a critical threat that organizations must defend against, timely patching of security bugs is essential in reducing risks.
Mind the (security) gap: Research on API attacks underscores risks
Our data validates the Open Web Application Security Project (OWASP) release candidate for their API Security Top 10. This new mix moves in a more API-specific direction (Figure 1). The inclusion of API vulnerabilities in this upcoming list seems to indicate a shift away from the heavy focus on web application threats, and brings to the forefront the growing risk of API attacks that organizations need to heed.
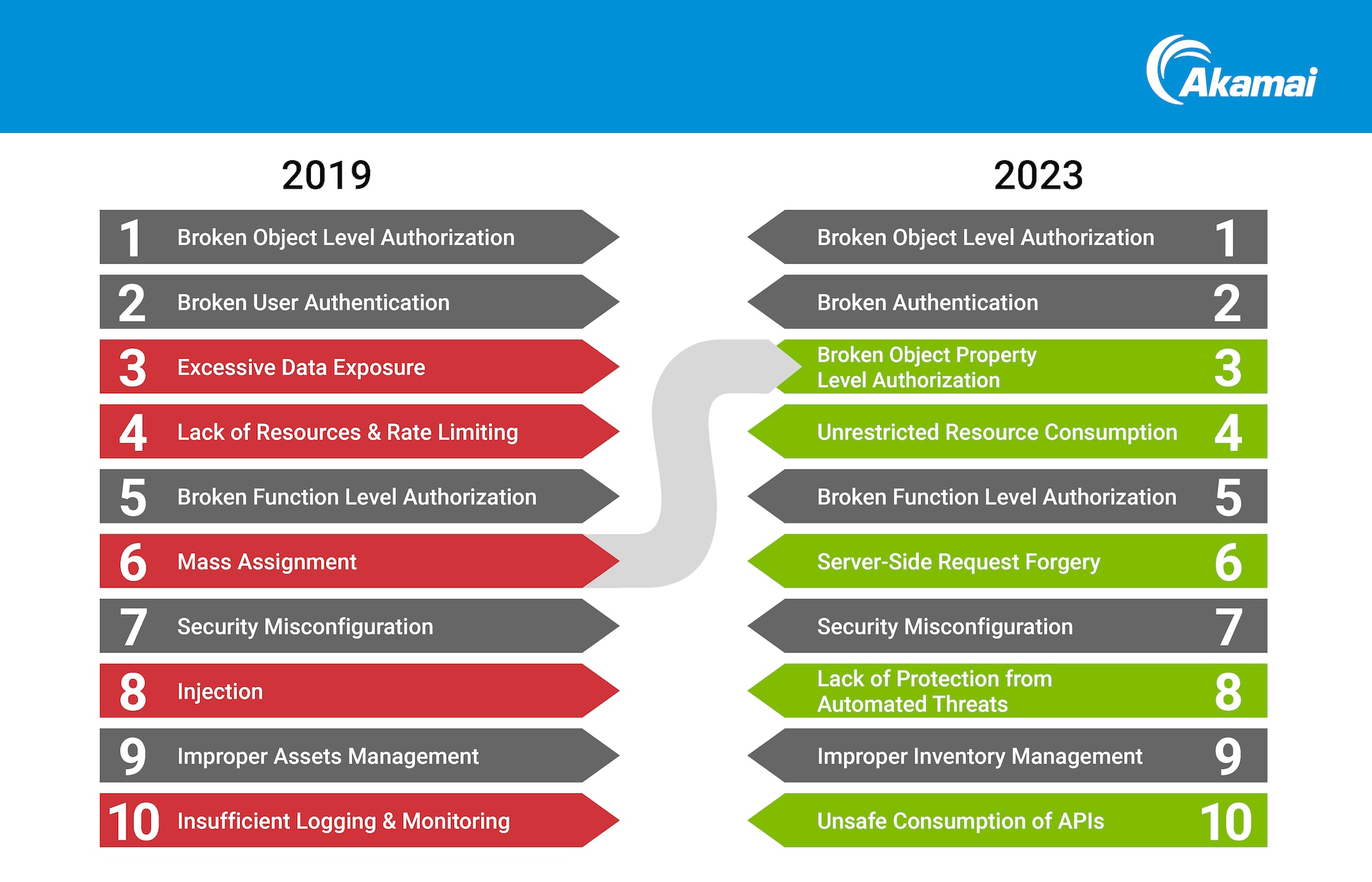 Fig. 1: The proposed new API Security Top 10 includes more API-specific attacks and emphasizes authorization issues (four of the top five attacks)
Fig. 1: The proposed new API Security Top 10 includes more API-specific attacks and emphasizes authorization issues (four of the top five attacks)
Broken Object Level Authorization
Broken Object Level Authorization (BOLA) is the top-ranked API vulnerability in the proposed OWASP API Security Top 10. Although it does not require a more technical approach like breaking encryption (the flaw resides in API logic), it can be very challenging to detect as it resembles legitimate traffic. It is also easy to exploit — attackers can scan for API endpoints vulnerable to BOLA attacks, and the risks could be detrimental as it allows access to the information of other users, such as stored personal identifiable information when successfully exploited (Figure 2).
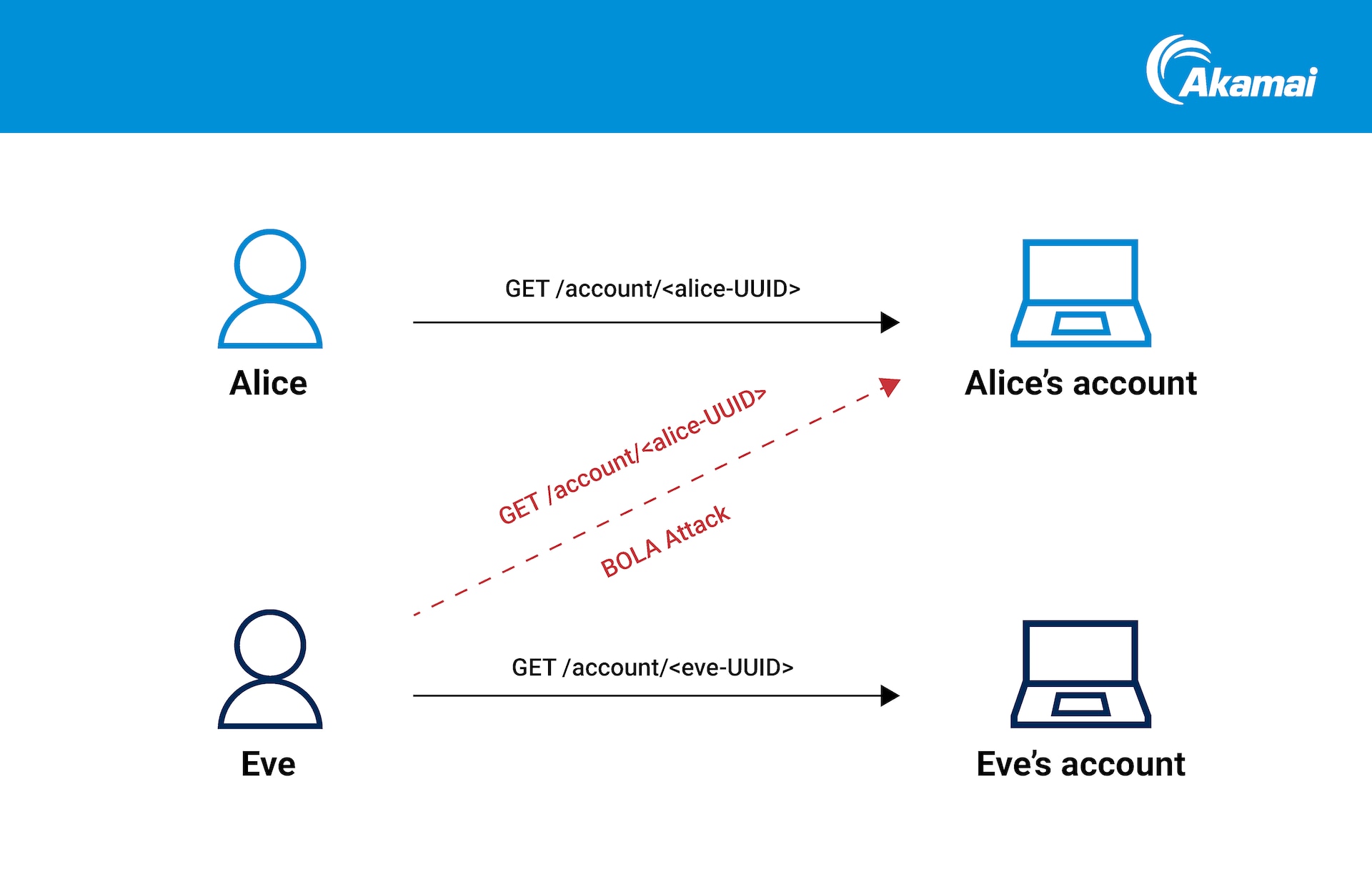 Fig. 2: A normal request versus a BOLA attack
Fig. 2: A normal request versus a BOLA attack
To mitigate the risks posed by BOLA attacks, here are some best practices:
Implement authorization checks for APIs that use client input to check if the current user can access the requested resources
Use Universally Unique Identifiers (UUID) for resource IDs over sequential numerical IDs
Write and run tests to evaluate your API endpoints for BOLA vulnerability
Broken Authentication
We also put a spotlight on Broken Authentication (#2 on the new list), in which there’s a weakness in validating or verifying if it’s an authorized user accessing an account. Although this type of attack is difficult to pull off as it requires a certain degree of technical know-how, the effects, such as account takeover, can be dangerous. This drove a review of the risk to include authentication flow risk, using secure algorithms, avoiding storing sensitive data in payload, and using a generated unique identifier for the kid parameter (if in use).
A year of vulnerabilities and emerging attack vectors
The year 2022 was a record year for application and API attacks and saw a continued battle with zero-day vulnerabilities. At the end of 2021, right on the heels of Log4Shell, organizations found themselves in the crosshairs of additional significant vulnerabilities: the Atlassian Confluence vulnerability, ProxyNotShell, and Spring4Shell.
We also saw emerging malware trends (like SSTIs and Server-Side Code Injection) pose serious business threats as they can lead to remote code execution and data exfiltration. Additionally, there was a surge in SSRF attacks: We observed a daily average of 14 million SSRF attempts against our customers’ web applications and APIs that could allow access to internal resources.
Zero-day vulnerabilities in open source software are becoming prevalent along with SSTI techniques that allow remote code execution. We also see threat actors leverage web shells in advanced persistent threat campaigns and HTTP Request Smuggling.
App and API risks in the time of digitalization: How attacks vary by industry
We also examined key industries and trends and the ways that cybercriminals are likely to use APIs and applications as a pathway to infiltrate organizations. Most industries saw growth in the frequency of attacks — with commerce, high technology, and financial services topping the list (Figure 3). It’s not surprising to see that financial services is in the top three: This reflects our findings from last year’s SOTI, Enemy at the Gates: Analyzing Attacks on Financial Services, in which we described a 3.5x surge in attacks on financial services.
Additionally, we saw this dramatic rise of LFI attacks in the commerce vertical. Perhaps attackers are taking advantage of the COVID-19–induced rush to deploy new applications and technologies by searching for vulnerabilities and other security gaps to exploit.
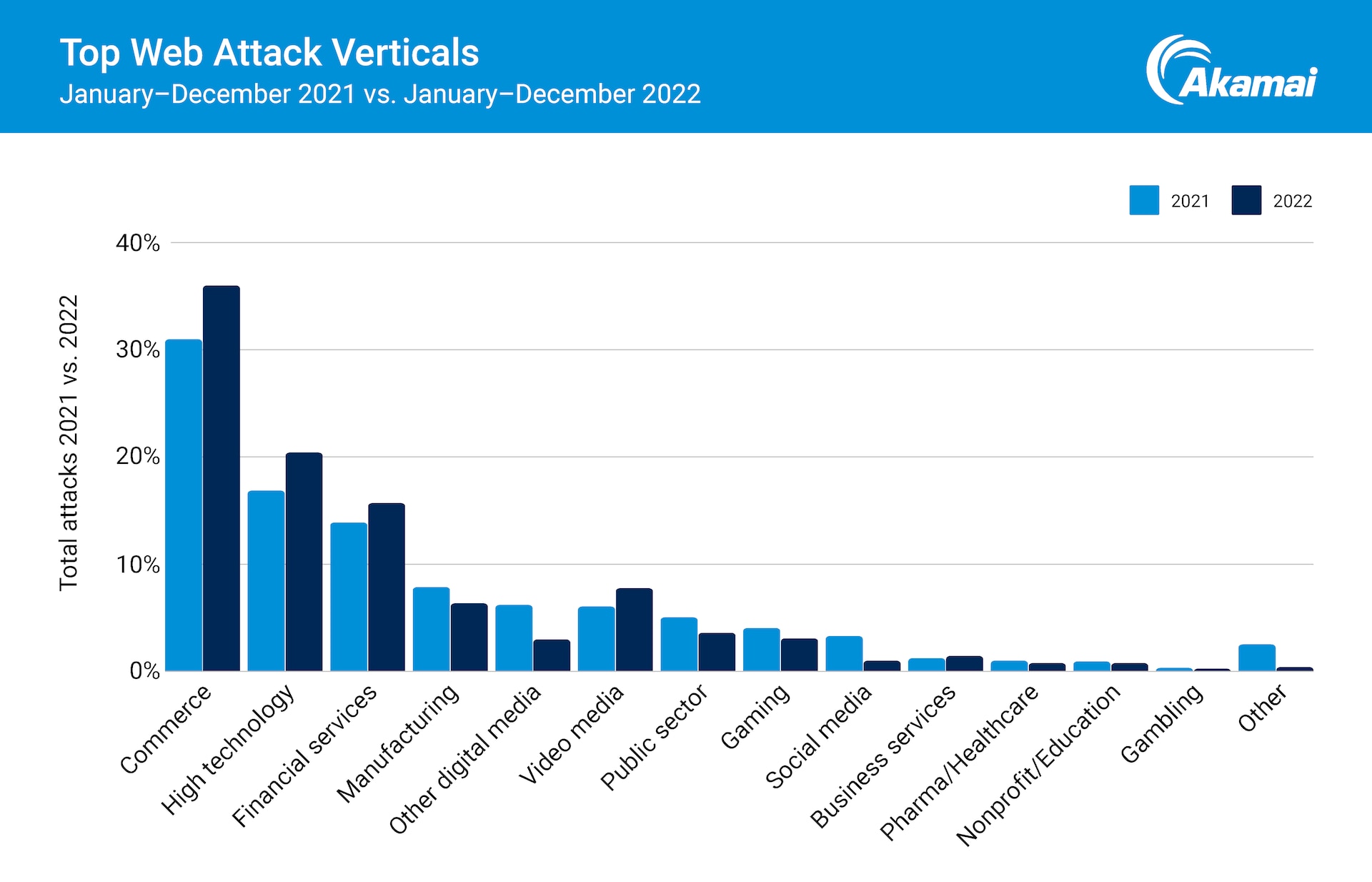 Fig. 3: The top verticals impacted by web application and API attacks are commerce, high technology, and financial services
Fig. 3: The top verticals impacted by web application and API attacks are commerce, high technology, and financial services
A different perspective
A look at the median dataset, however, offers a different perspective of the range of attacks per vertical. With this data, the manufacturing industry surpassed high tech and financial services in the number of attacks in 2022, which is consistent with our previous findings in our latest SOTI report, Attack Superhighway: A Deep Dive on Malicious DNS Traffic and our global ransomware threat report.
Although manufacturing companies do not necessarily deal with the same scale of app and API attacks as do direct-to-consumer verticals, such as retail, the impact of an incident can be serious. And the sharp rise (76%) in the median number of attacks in 2022 is troubling. Successful cyberattacks against operating technologies in this industry enable real-world impacts like supply chain issues.
Finally, median attacks against healthcare and pharmaceutical organizations also saw an uptick (82%), fueled by their adoption of the Internet of Medical Things (IoMT), which has expanded their attack surface. With many healthcare providers having a number of legacy systems, highly federated systems, and IoMT data, it is important to have strong segmentation and visibility of the data flows. Patient safety is too important to risk.
Thoughts on filling in the gaps
This summary has just touched on the rich data and technical details found in our report. We encourage you to read it in its entirety and bring the lessons from the report back to your business.
Some recommendations:
Do not wait for a crisis before you think about mitigating the different types of new or zero-day vulnerabilities, whether they are found in protocol (code), products, or firmware. Although these mitigations may all need slightly different playbooks, establishing a process can be critical to a timely response.
Mitigate these attack vectors with a web application and API protection/web application firewall (WAAP/WAF) at the edge, with segmentation/ringfencing internally, and with patching as soon as possible at the source.
Use the key issues and techniques discussed in the report to drive your pentest/red team planning so you can validate your risk posture. This should be analyzed by industry and, in some cases, by regions. Learn from other’s mistakes!
The next big vulnerability will be here soon — build or validate your playbooks now.
Conclusion
Review the changes to OWASP and, as you think about what to prioritize, start with OWASP’s updated recommendations as the baseline. The spotlight on Broken Authentication in JSON Web Tokens is a great case study of how you still need to practice secure code development and develop best practices and technical controls to ensure your applications meet your risk appetite.
We hope the data from this report provides insights to help you update your program and develop best practices.
For more insights, stay plugged in to our latest research at Security Research Hub.




