Capoae Malware Ramps Up: Uses Multiple Vulnerabilities and Tactics to Spread

Introduction
Recently, there has been a plethora of UPX packed crypto-mining malware written in Golang targeting Linux systems and web applications popping up in the news. The malware’s primary tactic is to spread by taking advantage of vulnerable systems and weak administrative credentials. Once they’ve been infected, these systems are then used to mine cryptocurrency. I’ve named the sample I examined for this post ‘Capoae,’ based on the code’s output to my terminal.
Around the same time the news was spreading about these crypto mining malware attacks, SIRT honeypots were infected with PHP malware that arrived via a backdoored addition to a WordPress plugin named download-monitor.
Download-monitor had been installed after the honeypot’s weak WordPress admin credentials had been guessed. A 3MB UPX packed Golang binary was also downloaded to /tmp. Upon examination, it was clear the malware had some decryption functionality and an encrypted file stored in another directory.
Further reviewing honeypot access logs, a request was made with an obfuscated payload shipped in a GET parameter.

This dw argument is rot13() and base64 encoded. Once the base64 value is rot13’d back to its original content and decoded, it becomes:
 Fig. 2) The above string in figure 1 is decoded
Fig. 2) The above string in figure 1 is decoded
The payload has two parts; the location (url) of the file to be downloaded, and the path (dir) to place it on the compromised machine’s filesystem.
The wp.txt file is downloaded and renamed to wp.php, it is then deleted after execution. The contents of this file were lost, however, due to the limitations of my logging system. The ProductList.php file is also renamed by appending a random string to the end of the filename to avoid passers-by from finding it. The string appears to be generated with the following bash function that uses a md5sum of the output of the date command.
echo $(date|md5sum|awk -v n="$(date +%s)" '{print substr($1,1,n%7+6)}')
The file ./wp-content/plugins/download-monitor/src/Libs/uaparser/regexes.php is an encrypted web shell that takes one parameter as an argument ‘dw’. It is called from the main ProductList.php script, where the dw payload is decrypted and executed. The decryption key for the payload is based on the User-Agent string of the request.
 Fig. 3) User-Agent string being used as a decryption key
Fig. 3) User-Agent string being used as a decryption key
Yet another web shell is added as a back door located at ./wp-admin/includes/class-wp-page-n3RkIo.php
It contains a simple web shell that can be used to upload files:
 Fig. 4) A small file upload web shell script
Fig. 4) A small file upload web shell script
Connecting to the ProductList.php script with a web browser and the correct User-Agent string yields the following web shell interface:
 Fig. 5) Webshell after being decrypted and executed
Fig. 5) Webshell after being decrypted and executed
What’s in the binary
After unpacking the malware with ‘upx -d’, we can look at the actual binary structure. Examining said structure shows that it has functions targeting a handful of well-known vulnerabilities and content management frameworks. A few of the most interesting functions are listed below. Based on the function names and disassembly in R2, we can infer what is going on.
The Golang malware can be found in VirusTotal with an origin date of 8/9/2021:
$ ./redress -compiler Capoae
Compiler version: go1.15.4 (2020-11-05T21:21:32Z)
Using Redress we can see the binary was compiled with Go v1.15.4.
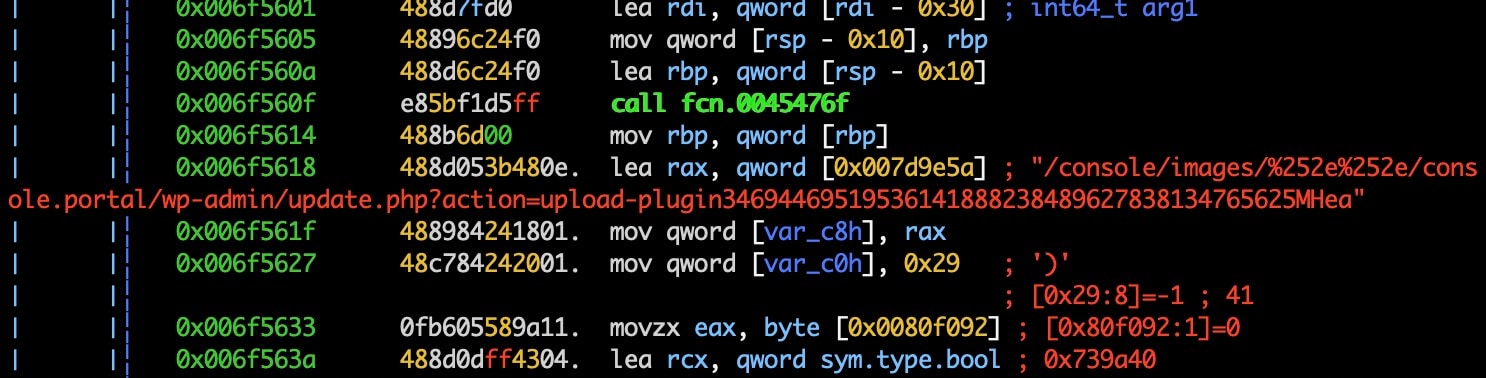
Digging in further, we also find exploitation code for CVE-2020-14882, which targets Oracle WebLogic Server with an Unauthenticated Remote Code Execution (RCE).
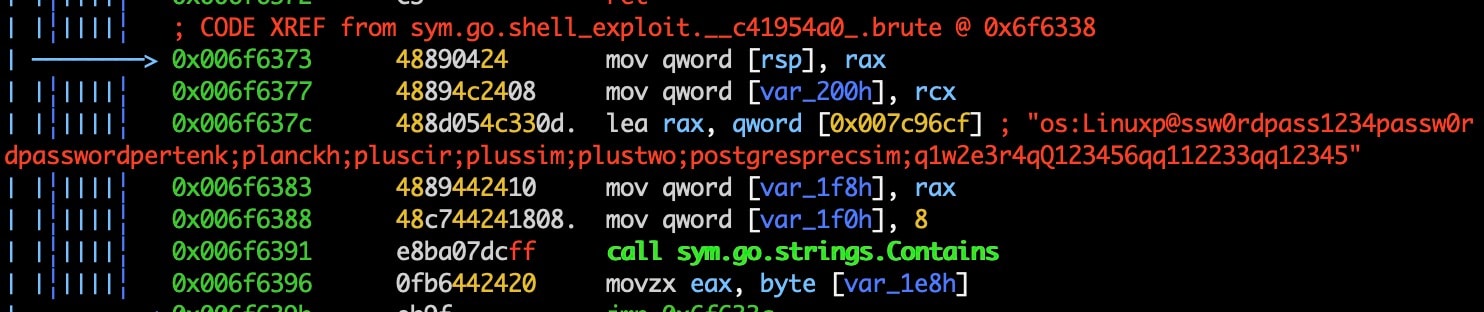
The binary uses a list of weak login credentials to brute force its way into systems running SSH. Once successfully authenticated, the malware installs a public key into .ssh/authorized_keys.
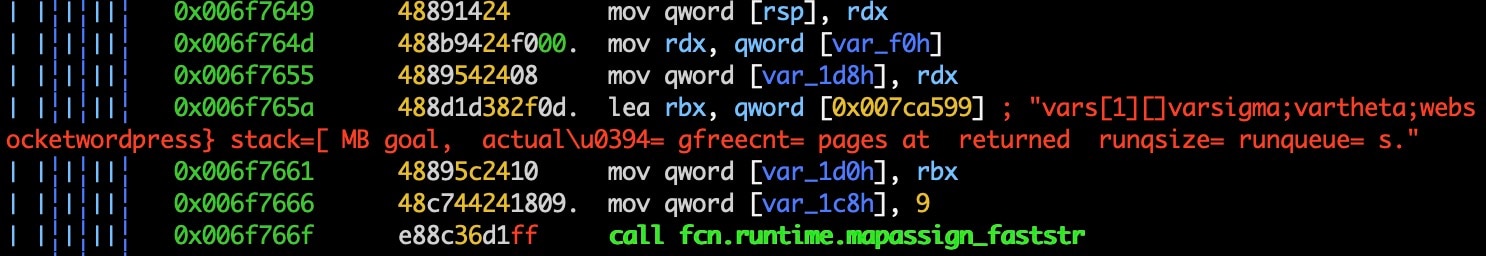
Here we see more exploitation code, this time targeting CVE-2018-20062, a well-known and widely exploited remote code execution vulnerability in ThinkPHP.
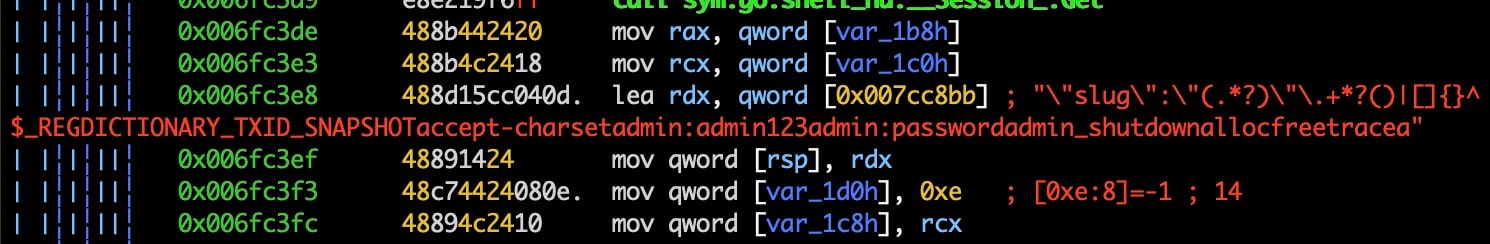
This section contains another spreading mechanism. Here the malware attempts to brute force weak credential pairs against WordPress installations discovered via the WordPress XMLRPC API.
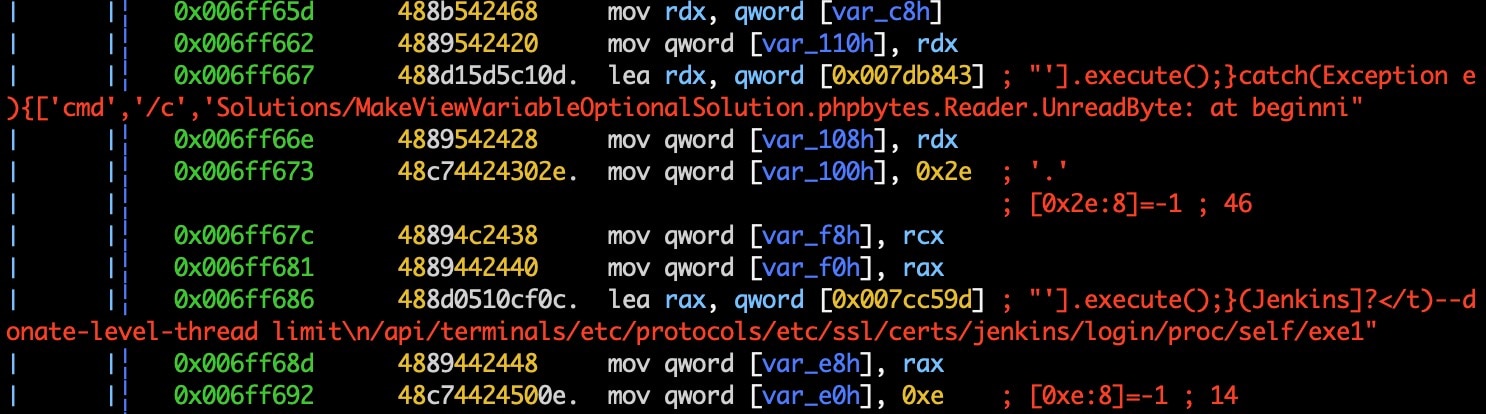
Partial disassembly of functions that target Jenkins installations for CVE-2019-1003029 and CVE-2019-1003030, both are RCE vulnerabilities.
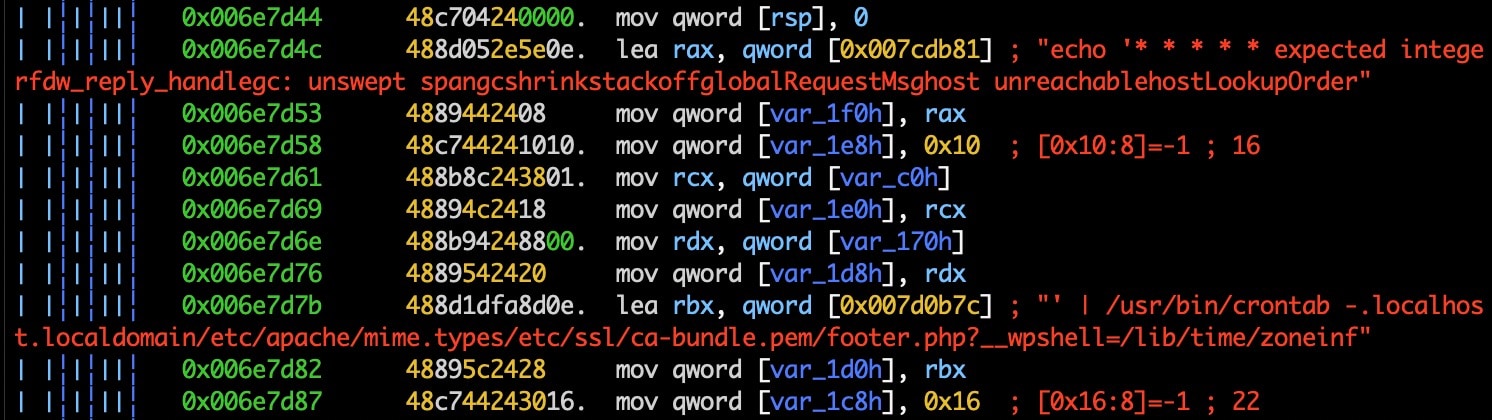
The guard.go code maintains persistence by adding an entry to crontab.
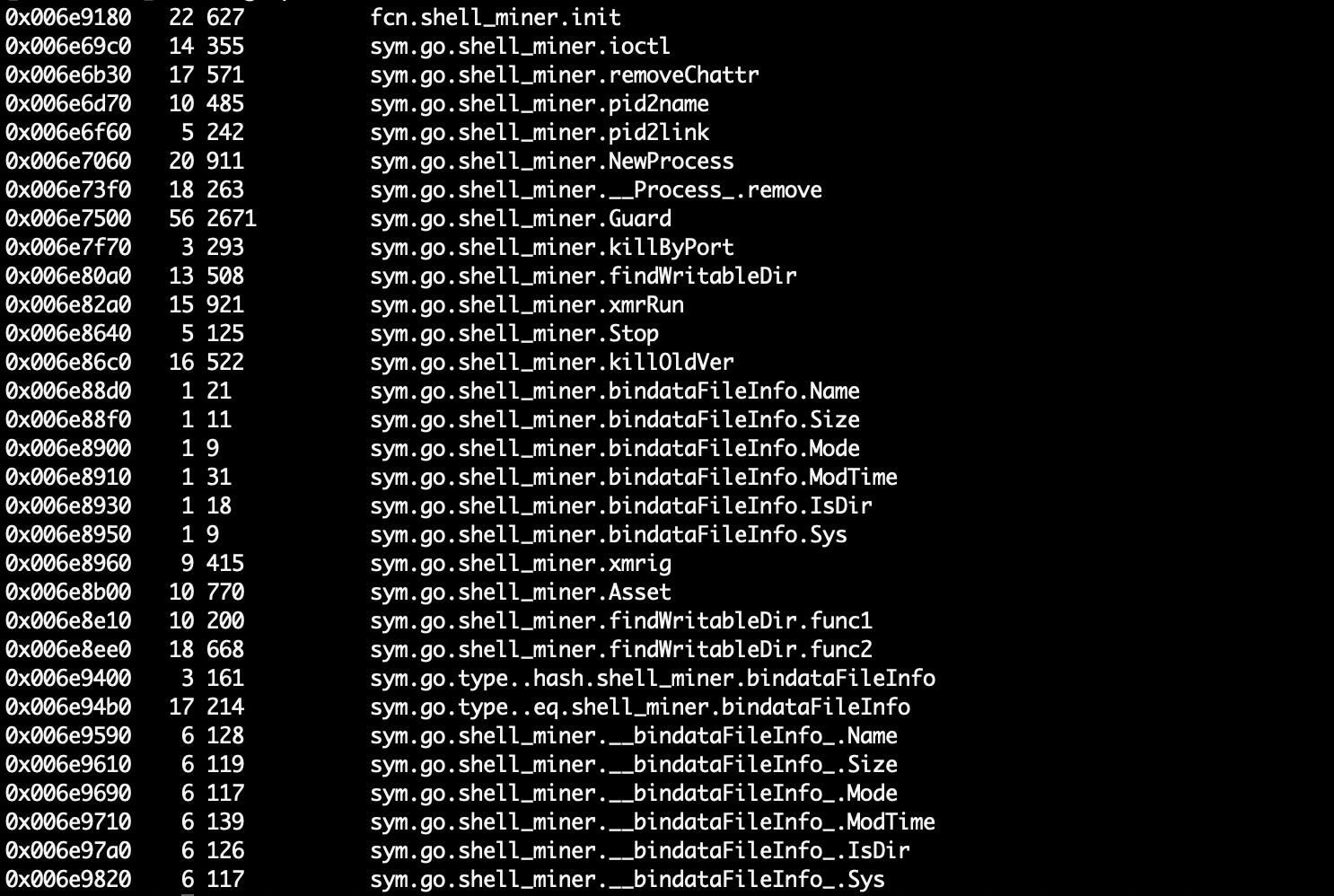
In the above screenshot, a list of functions linked to the xmrig_linux_amd64.go file is displayed. These are shell bindings that expose methods for crypto-mining interfacing. The mining campaign leverages the popular XMRig mining software but is ultimately launched and monitored by the malware.
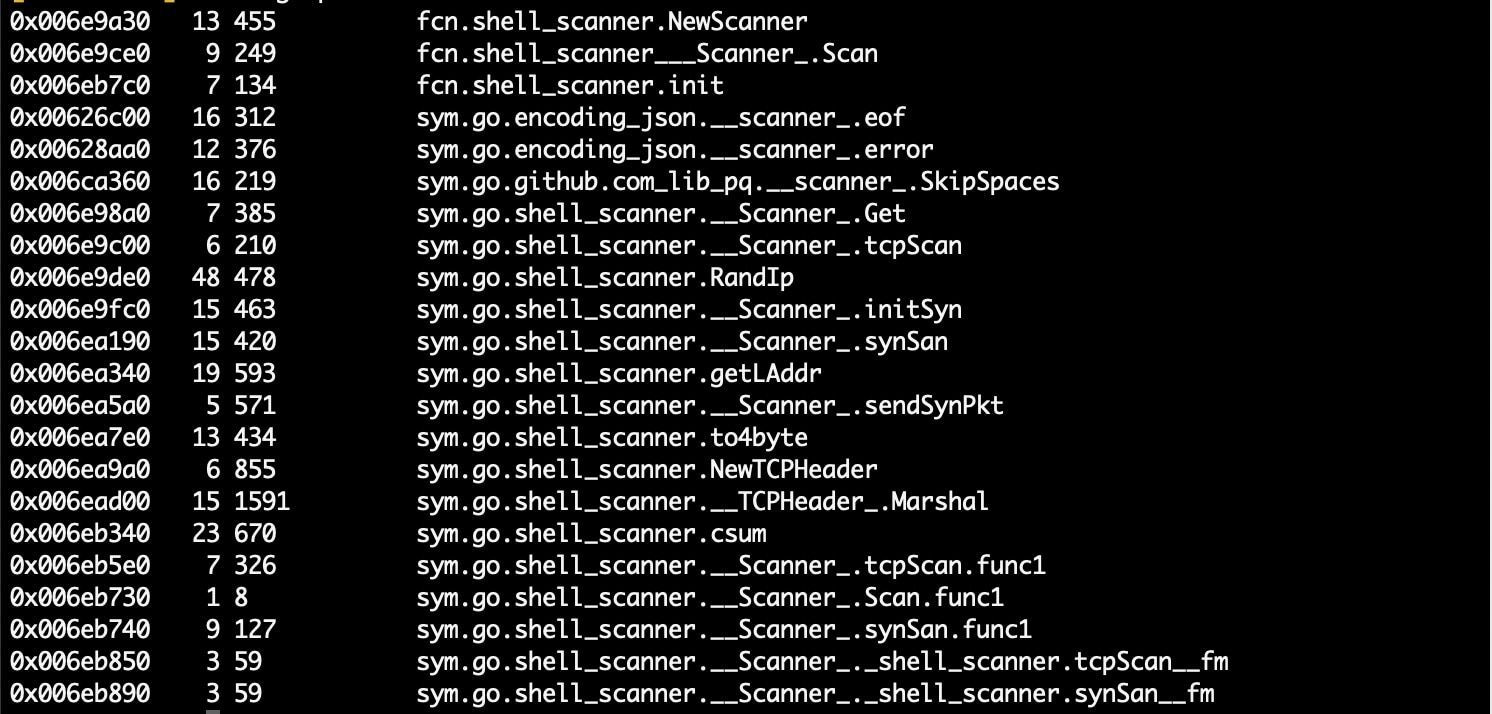
A port scanner is also included in the malware and is used to find open ports and services. It targets randomly generated IP addresses, checking for ports it can launch its various exploit payloads against.
Malware detonation
Upon execution of the Golang binary, a single vague string was printed to the terminal.
 Fig. 6) Output from the execution of Capoae malware
Fig. 6) Output from the execution of Capoae malware
Looking at a strace of the execution, we can see what the non-printable bytes within the text would have been if my terminal supported Cyrillic characters.
 Fig. 7) Output from strace showing the Russian word for ‘Scanning’.
Fig. 7) Output from strace showing the Russian word for ‘Scanning’.
The output is actually “Сканирование”, which is Russian for “Scanning”. Because of this, I’ve decided to use only the ASCII characters that were rendered in my terminal on the initial detonation and have named the malware sample Capoae.
After the Capoae malware is executed, it has a pretty clever means of persistence. The malware first chooses a legitimate-looking system path from a small list of locations on a disk where you’d likely find system binaries. It then generates a random six-character filename, and uses these two pieces to copy itself into the new location on the disk and deletes itself.
Once this is done, it injects/updates a Crontab entry that will trigger the execution of this newly created binary. When that detonation occurs, this entire process occurs again. This ensures killing the infection is a bit like playing a game of whack-a-mole, with a constantly moving infection/payload.
 Fig. 8) Crontab Entry
Fig. 8) Crontab Entry
Among common RCE exploits for Oracle WebLogic like CVE-2020-14882 and CVE-2018-20062 that impacted ThinkPHP, we can see the WordPress content management framework is specifically targeted. The malware preys on weak login credentials to gain access.
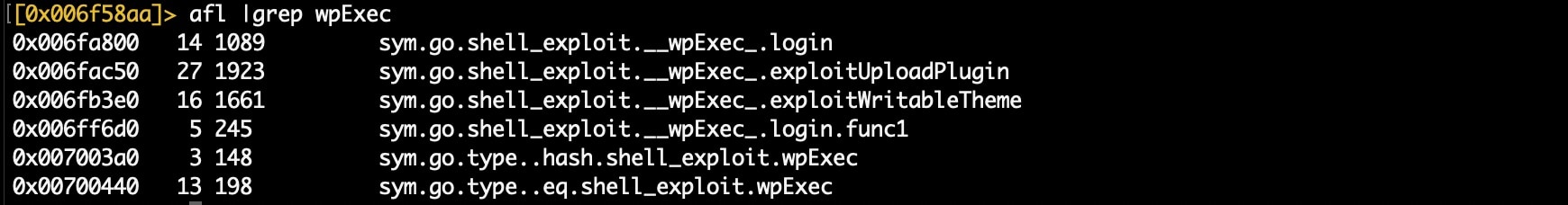 Fig. 9) A list of WordPress-specific functions
Fig. 9) A list of WordPress-specific functions
The exploit writable theme wrote a small PHP script to footer.php in the theme twentynineteen that downloaded the ldr.sh file and executed it. The user-agent string used is the method through which the host was infected. In the below screenshot, we can see the User-Agent string is set to ‘brute_wordpress_admin’.
 Fig. 10) Packet capture of modification to footer.php
Fig. 10) Packet capture of modification to footer.php
Looking at the exploitUploadPlugin function, we see that it can install a plugin using the admin panel interface. Figure 10 highlights some of the plugin installation parameter strings shown in the disassembly.
.jpg)
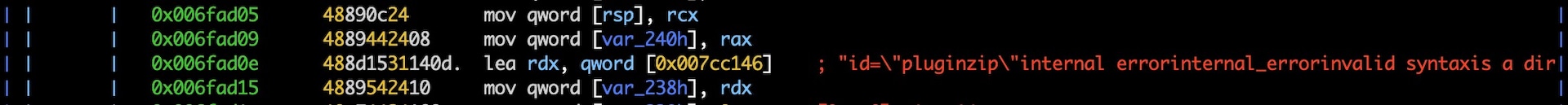 Fig. 11) A partial disassembly of exploitUploadPlugin
Fig. 11) A partial disassembly of exploitUploadPlugin
Of course, the purpose of this malware is to mine cryptocurrency. The crypto mining pool configuration file is shown below, revealing the threat actors are using a mining pool hosted on ntup.net, a Russian VPS company.
 Fig. 12) The miner config file in JSON
Fig. 12) The miner config file in JSON
Closing takeaways
Crypto Mining campaigns are continuing to evolve. The Capoae campaign’s use of multiple vulnerabilities and tactics highlights just how intent these operators are on getting a foothold on as many machines as possible.
The good news is, the same techniques we recommend for most organizations to keep systems and networks secure still apply here. Don’t use weak or default credentials for servers or deployed applications. Ensure you’re keeping those deployed applications up to date with the latest security patches and check in on them from time to time.
Keeping an eye out for higher than normal system resource consumption, odd/unexpected running processes, suspicious artifacts (files, crontab entries, SSH keys, etc.), and suspicious access log entries, etc., will help you potentially identify compromised machines. We’ve also included a list of Indicators of Compromise (IoCs) below that can be used to check filesystems and network traffic for possible infections.
IoCs
SHA256SUM
7d1e2685b0971497d75cbc4d4dac7dc104e83b20c2df8615cf5b008dd37caee0 Capoae UPX Packed
fd8f419f0217be0037ba7ae29baf4c3a08c8f2751b0b1be847b75bd58d6e153f Capoae UPX Unpacked
5a791205bc08396bc413641ea6e5d9fd5ef3f86caf029f51d4da65be700a2b1e ProductList-n3RkIo.php
f37cc420165fb809eb34fbf9c8bf13236a0cc35dee210db5883107a08a70f66d class-wp-page-n3RkIo.php
53521fab245023c56cf5562bd562d6ba98445a052155eb2e40c4a13a9343e6eb regexes.php
9ed14f470c95759cc0dca86fd913714b6733af8c0aaa35e3a7ad6604455e2230 sys.i686 UPX Packed
af7c5617a89c40aac9eb2e573a37a2d496a5bcaa9f702fa919f86485e857cb74 sys.x86_64 UPX Packed
7eb444671ab338eccadf81d43166661ccb4b1e487836ab41e2245db61dceed31 ldr.sh
IPs
198.100.145.141
23.238.128.118
69.12.66.218
207.126.93.190




