How to Dramatically Simplify PCI DSS Compliance
Executive summary
PCI DSS is a global security standard set to protect card payments against ongoing cybersecurity threats.
In March 2022, PCI DSS v4.0 was released, containing several new security requirements to address changes in the threat landscape.
Microsegmentation divides a network into smaller parts so security teams can implement custom security policies to limit east-west traffic.
Meeting every PCI DSS v4.0 certification requirement can pose a significant challenge to organizations.
Effective microsegmentation can streamline the process of organizations becoming PCI DSS-compliant.
The Payment Card Industry Data Security Standard (PCI DSS) is a global information security standard set defined by the PCI Security Standards Council — and validated by the Qualified Security Assessor — to protect cardholder data against ongoing cybersecurity threats. It governs how businesses accept, handle, transmit, and store customer credit card data and other financial information. Payment processors and organizations that handle payment processing online (such as ecommerce retailers) must adhere to these requirements to stay PCI DSS–compliant and avoid penalties and remediation.
Inside the infamous March deadlines
In March 2022, PCI DSS version 4.0 was released. It included several new security requirements that address changes to the threat landscape that have emerged since version 3.2.1 was released in 2018.
PCI DSS v3.2.1 was retired on March 31, 2024, and version 4.0 will become active in March 2025. This means that organizations have one year to fully comply with the new standard — a massive undertaking for compliance and security teams.
Of the many tools that businesses can use to become PCI-compliant, microsegmentation stands apart as it offers broader, more robust capabilities for quickly handling several new PCI requirements.
What is microsegmentation?
Microsegmentation divides a network into smaller, more granular parts — including individual workloads, virtual machines, applications, and operating systems. This security solution is more robust and secure than typical firewalls; security teams can implement custom security policies — including data and application access control — for each network area to limit myriad east-west traffic types across servers and applications.
With microsegmentation, organizations get greater visibility into potentially malicious traffic inside their network. It blocks attacks based on lateral movement, helping security teams more quickly identify potentially suspicious behavior that could signify a network or data breach.
Customer compliance challenges
Meeting every PCI DSS v4.0 certification requirement can pose a significant challenge to organizations. In particular, they may struggle with:
Identifying and scoping the cardholder data environment
Isolating and segmenting the PCI environment
Addressing the need for multiple security controls
Identifying and scoping the cardholder data environment
The PCI DSS process is exhaustive, time-consuming, and costly. Applications and network environments included in the PCI DSS scope can be complex and span multiple systems — often across hybrid and multicloud infrastructures. Correctly scoping a PCI DSS–compliant environment requires IT security and compliance teams to accurately identify the system components of the cardholder data environment (CDE).
The IT security and compliance teams must then prove that they have completely disconnected their PCI DSS environment and their out-of-scope systems. Without visibility into the CDE, your security team is prone to segmentation errors and can potentially expose your network environment to a security breach.
Isolating and segmenting the PCI environment
Flat networks are a common concern among businesses looking to become PCI DSS–compliant. In a flat network, the CDE is connected to non–card-processing environments. With a flat network, your audit costs can increase because the auditor will consider everything to be part of the PCI audit’s scope.
Addressing the need for multiple security controls
Meeting every PCI DSS standard condition requires implementing several unique security controls. For example, one requirement mandates placing a network security control to separate the CDE from other applications, while another demands monitoring the CDE. These different technologies often require numerous vendors, as well as unique support and maintenance procedures.
Akamai Guardicore Segmentation: Become PCI DSS–compliant with microsegmentation
With a robust network segmentation solution, organizations can dramatically cut costs and time spent on PCI DSS compliance efforts.
Akamai Guardicore Segmentation can empower your IT and compliance managers to show auditors that they can:
Scope PCI environments with a real-time visibility map
Isolate PCI environments from the larger network with comprehensive microsegmentation
Reduce the compliance and audit burden by addressing all requirements with a single tool
Scope your PCI DSS environment better with a real-time network map
Akamai Guardicore Segmentation’s interdependency map helps your IT and compliance managers identify your CDE and out-of-scope systems, providing greater visibility so you can more accurately scope the entire environment. Figure 1 shows the Akamai Guardicore Segmentation map displaying an organization’s network after microsegmentation.
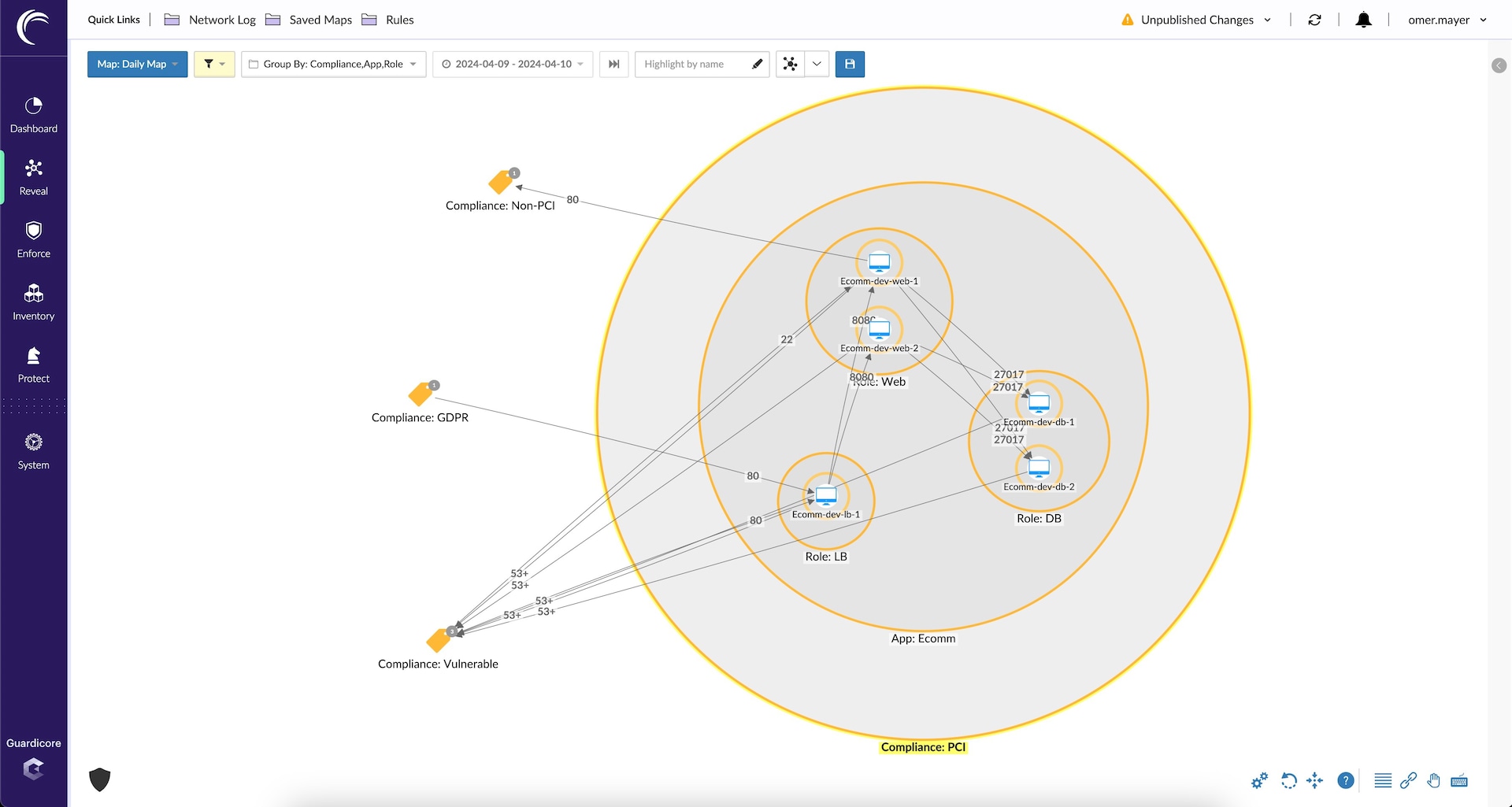 Fig 1: Akamai Guardicore Segmentation network segmentation map
Fig 1: Akamai Guardicore Segmentation network segmentation map
Isolate your PCI DSS environment from your network with effective segmentation
Akamai Guardicore Segmentation can segment your entire enterprise’s network — including the data center and hybrid cloud that store sensitive data. With this unified microsegmentation solution, your security policies are abstracted from your network infrastructure and can move with the workload across environments — all without the need to change or reconfigure the network. Figure 2 shows how to get automated policy suggestions and a matching map from the Akamai Guardicore Segmentation portal.
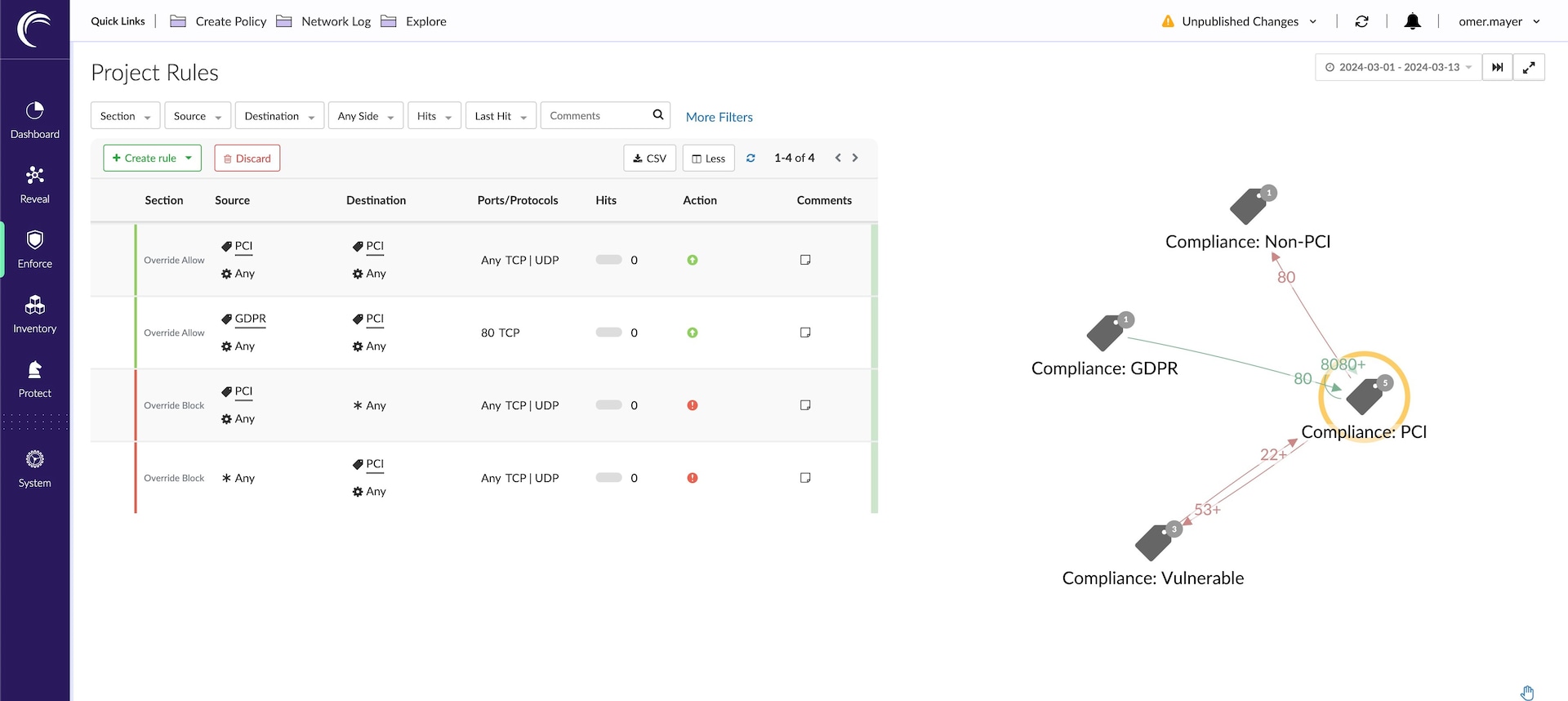 Fig 2: Akamai Guardicore Segmentation automated suggested rules
Fig 2: Akamai Guardicore Segmentation automated suggested rules
Reduce compliance and audit burden with one tool
Akamai Guardicore Segmentation allows IT and compliance managers to reduce the compliance and audit burden by addressing many PCI DSS requirements with one tool, rather than having to navigate multiple point solutions. That way, you can make your enterprise organization PCI DSS–compliant for drastically less time and money.
Read GRSee’s third-party report to discover more about how Akamai Guardicore Segmentation can simplify your PCI DSS audit and help you better comply with PCI DSS v4.0 requirements.




