Examining the Polyfill Attack from Akamai's Point of View
Editorial and additional commentary by Tricia Howard
The polyfill.io supply chain attack: An overview
Recently, the security community was alerted to a significant supply chain attack involving polyfill.io, a service that provides polyfills (a piece of JavaScript code that allows modern functionality on older browsers that do not natively support it) for web applications. According to detailed reports, this attack has impacted more than 100,000 websites, abusing the trust and widespread use of the polyfill.io service in order to propagate malicious code.
In this attack, a malicious actor that appears to be located in China acquired one of the most popular polyfill open-source projects a few months ago and infected the polyfill JavaScript code by injecting malicious scripts into the distributed polyfills. The attack primarily targeted mobile devices, selectively sampling sessions to remain stealthy and harder to detect. The malicious code was then used for a redirection attack, diverting users to scam sites.
As developers integrated these compromised polyfills into their websites, they unknowingly introduced malicious code into their applications. In this blog post, we will discuss this specific attack — and supply chain attacks, in general — as well as exclusive data that we have observed from the point of view of Akamai Client-Side Protection & Compliance.
What is a supply chain attack?
A supply chain attack targets the vulnerabilities within an organization’s supply chain. In the context of online web applications, modern websites load tens of third-party resources as part of the regular site functionality. These resources are trusted by website owners and typically have full access to the page, including the Document Object Model (DOM), cookies, and sensitive information entered by end users.
Monitoring and tracking these resources is extremely challenging because of their numbers, frequent changes, and lack of client-side visibility. This trust can be exploited by attackers, who use these third-party services to compromise web applications. These attacks usually involve injecting malicious code into legitimate third-party libraries or services, which are then unknowingly distributed to end users.
According to research conducted by the Akamai Security Intelligence Group, 50% of the JavaScripts used in ecommerce websites come from third-party sources. On average, we observe code from tens of different third-party vendors on our customers' payment pages, which now need to comply with the new PCI DSS v4.0 requirements 6.4.3 and 11.6.1.
The polyfill attack from Akamai’s point of view
The polyfill attack is delivered through the targeted website as JavaScript code originating from cdn.polyfill.io. The attack uses both server-side and client-side sampling. On the server side, it examines request headers, such as the user-agent, to target only mobile devices with specific conditions. For other devices, the polyfill server serves the original polyfill code or an empty response for modern browsers.
The sampling process is not limited to the server side. During execution, the code also verifies the device type on the client side using its own JavaScript. Additionally, it selects targets based on the page referrer and the local device time. When the malicious JavaScript executes its attack, it communicates with a server at googie-anaiytics[.]com.
We were able to monitor the execution of malicious JavaScript on the web page, including its communication with its server. When suspicious activity was detected, an alert was triggered for the affected customers. The name of the game with any threat is agility; the ability to respond quickly is paramount to limiting the blast radius of an attack.
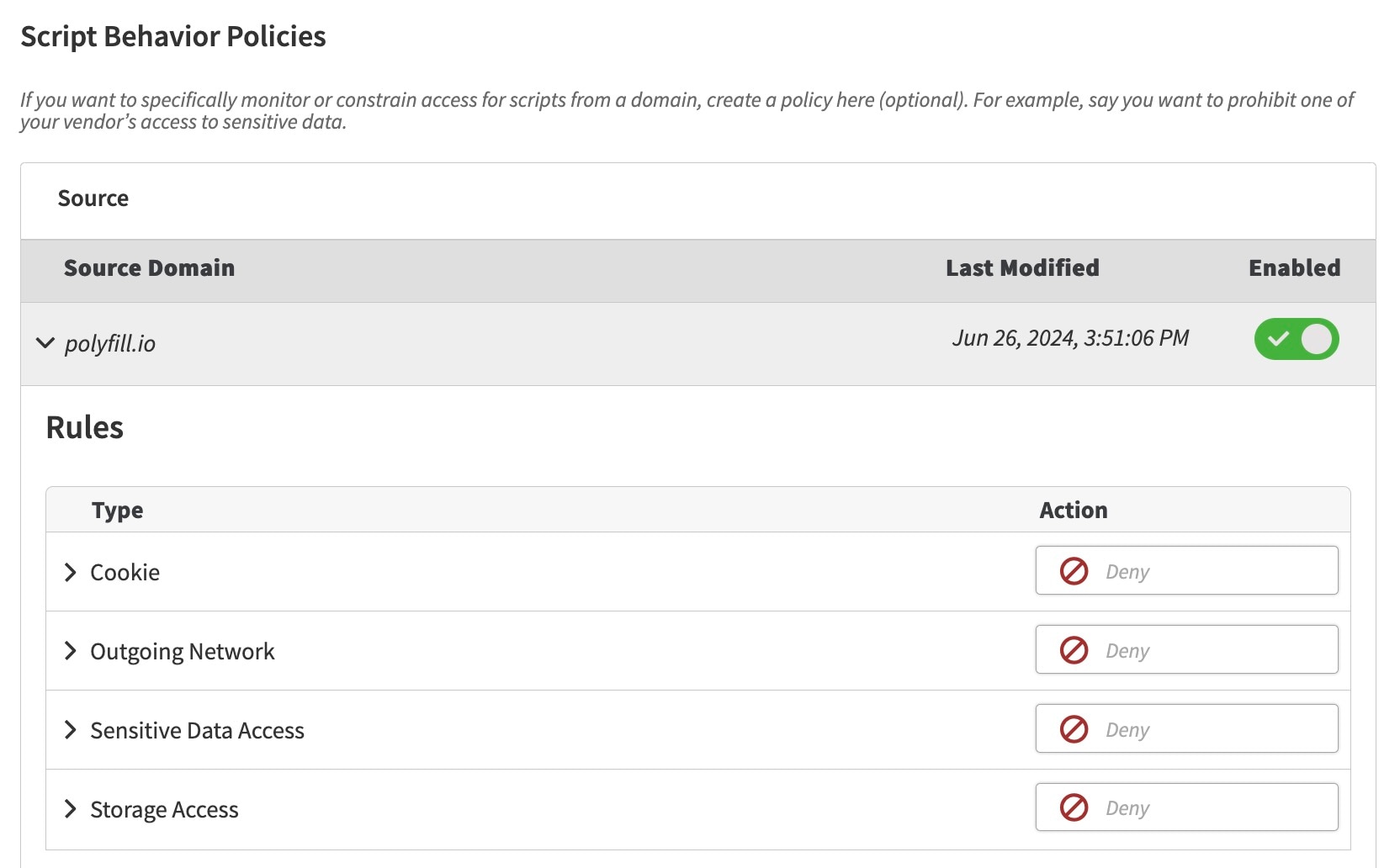
Client-Side Protection & Compliance Script Behavior Policies have been defined to block this communication, denying this path of the attack from proceeding. Figure 1 shows a real-life example of this in the wild: The denial of this attack path occurred in real-time, immediately after the policy was activated.
Polyfill.io use trends before and after the attack
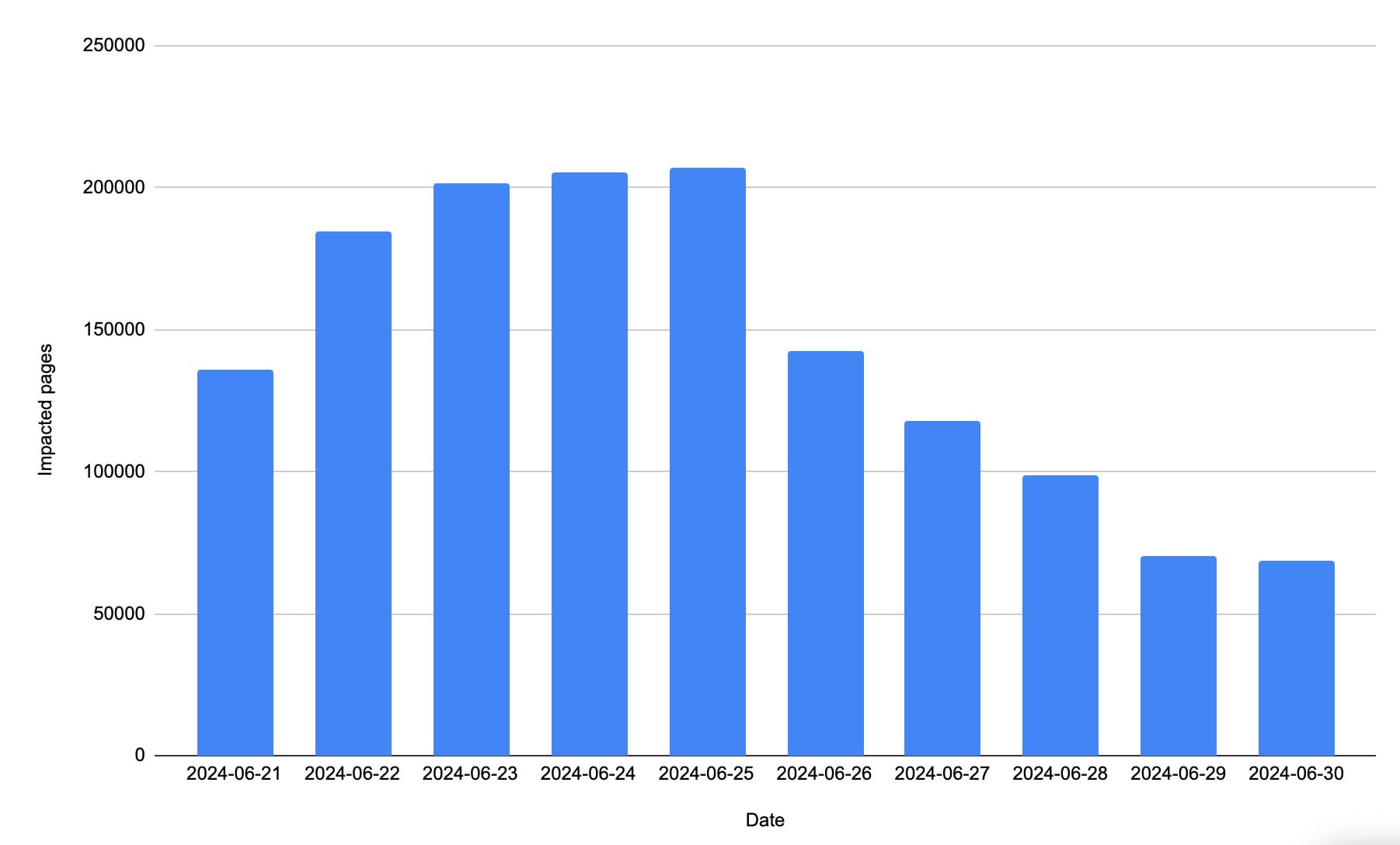
We observed that more than 40 customers had resources loaded from polyfill.io. Some of these customers experienced tens of thousands of impacted pages daily (Figure 2). This number includes customers who directly used JavaScript resources from polyfill.io, third parties who included this code as part of their execution, and resources originating from end users’ browser extensions.
Our data was pulled from Akamai Client-Side Protection & Compliance, which actively monitors and analyzes JavaScript executions in real time, allowing for reduced time to remediation, whether it be first party or third party.
Akamai is collaborating closely with its customers to effectively respond to and mitigate the impact of the attack, including a notification for relevant customers with a security bulletin about the attack. This proactive approach has led to a significant decrease in resources originating from the infected domain name, thereby reducing risk exposure for Akamai's customers.
Need help with supply chain attacks?
Akamai Client-Side Protection & Compliance is designed to safeguard customers against client-side attacks, originating from both first-party and third-party sources, including supply chain attacks.
The solution monitors JavaScript resources in web applications, analyzes their execution in real time, and determines whether they behave suspiciously. It also detects script behavior anomalies, providing a detailed analysis of every JavaScript resource loaded and executed in web applications.
Additionally, Client-Side Protection & Compliance offers real-time mitigation capabilities that prevent malicious script execution within seconds. Without the need to change the web application’s code to block suspicious behavior, security teams can dramatically improve response time to an attack. The solution is able to detect the polyfill.io attack and the impacted user sessions, and then stop the attack execution.
In-browser detection and mitigation advantages
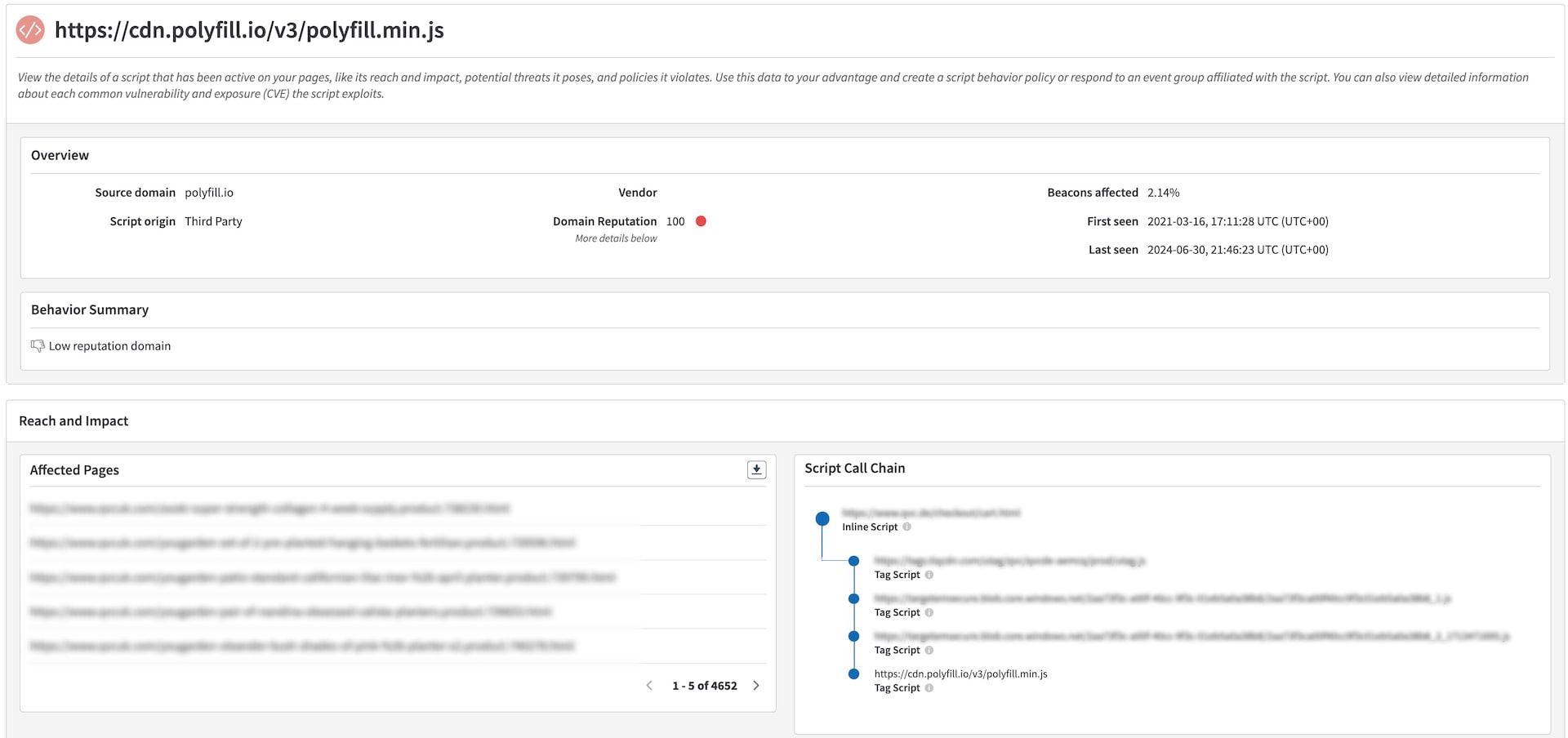
This attack targeted only a small number of sessions, particularly by filtering sessions with uncommon user-agent browsers, so solutions that only perform synthetic scans on the website might have missed this attack flow. One of the key advantages of Akamai Client-Side Protection & Compliance is that it runs inside the browser for every user session; it detected malicious JavaScript executions even when these targeted specific sessions were initiated — and, more important, it prevented attack execution on the page once the protection policy was activated (Figure 3).
Conclusion
The polyfill.io supply chain attack underscores the critical vulnerabilities inherent in modern web application development. Reliance on third-party resources can inadvertently introduce security risks, even when all the proper protections are in place. This incident, involving more than 100,000 websites, highlighted the ease with which trusted services can be compromised to distribute malicious code, diminishing user security and trust.
Monitoring threats such as these are what the Akamai Security Intelligence Group is all about, for both our customers as well as the security community in general. We will continue to observe the threat ecosystem and provide write-ups of our observations. For real-time updates, follow us on X, formerly Twitter, or check out our security research page.