Rails Without Derails: Thwarting Code Injection Attacks
At Akamai, we are committed to continuously enhancing our web application firewall (WAF) to ensure the highest level of security for our customers. As part of this commitment, we are excited to announce the release of a new dedicated detection capability for code injection attacks that specifically target Ruby on Rails (Rails) applications.
Why is it crucial to protect Ruby on Rails applications?
Ruby on Rails has become a popular framework for web application development because of its ease of use, flexibility, and robust ecosystem. The ability of Rails to accelerate development time while maintaining a clean and supportable codebase has made it very attractive to developers in organizations of all sizes. Many household name brands, such as GitHub, Shopify, Airbnb, and Basecamp, have built their platforms using Ruby on Rails, which highlights its significance in the tech industry.
However, Rails has also become a more attractive target for cyberattackers for the same reasons it attracts developers. The more-automated processes and ever-increasing need for applications to interoperate creates new places for attackers to hide. Protecting Rails applications is essential to safeguard the sensitive data and business operations of these critical platforms.
Growing threats against Ruby on Rails
Over the years, Rails has faced several notable security vulnerabilities and attack vectors. The Open Worldwide Application Security Project (OWASP) has a cheat sheet on securing Rails that shows how imperative it is for developers and security teams to stay vigilant.
While most high-profile vulnerabilities in Rails have been related to insecure deserialization of JSON and YAML data formats, developers might inadvertently expose the application and users' data to additional classes of attacks, such as code injection. This is particularly true with the ‘eval’ function in the Ruby language. This function dynamically builds Ruby code from a string input. If attacker-controlled input ends up within this function, the attacker can execute any arbitrary Ruby code.
Here is an example of such a case:
def calculate
calc = params[:calc]
result = eval(calc)
render plain: result
End
In this extremely naive example, the calculate action takes a calc parameter from the user input, which includes a mathematical operation such as “1+2”, and uses the Ruby eval method, which in turn returns the result of the mathematical operation. This creates a code injection vulnerability because an attacker can provide arbitrary Ruby code to be executed.
How the attacker can exploit this vulnerability
An attacker could exploit this vulnerability by submitting a crafted request with malicious Ruby code, such as:
POST /calculate?ip=IO.popen('cat%20%2Fetc%2Fpasswd').read%20%23
Or in its decoded form:
IO.popen('cat /etc/passwd').read #
This command would result in reading the contents of the system's /etc/passwd file (which contains sensitive information about system users). The # symbol at the end is a Ruby comment that ignores anything after it, preventing any syntax errors from the rest of the code.
Mitigating with Akamai Adaptive Security Engine
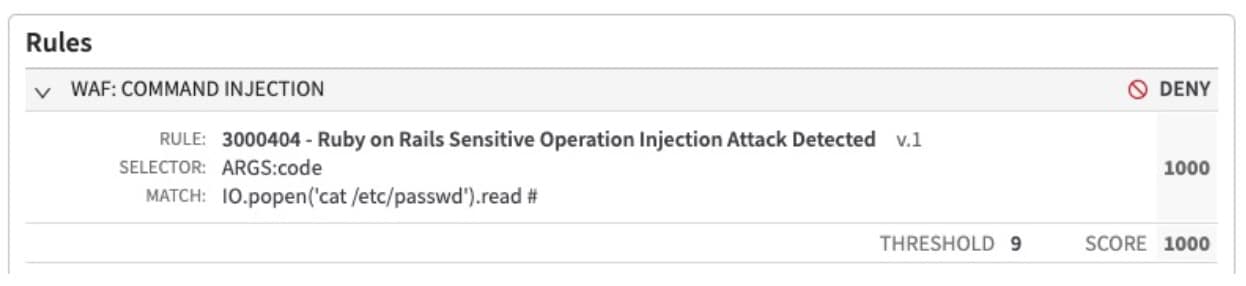
The increasing prevalence of sophisticated cyberthreats makes it imperative to have robust security measures in place. Our latest Adaptive Security Engine rule, 3000404 — Ruby on Rails Sensitive Operation Injection Attack Detected, offers a higher level of accuracy and coverage in detecting and mitigating code injection attacks on Rails applications (Figure 1).
Key benefits
Improved accuracy: Advanced detection techniques accurately identify and block code injection attempts, minimizing false positives and ensuring that legitimate traffic is not impacted
Comprehensive coverage: Extensive coverage for a wide range of code injection vectors offers robust protection for your Rails applications
Ruby on Rails code injection attacks against our customers
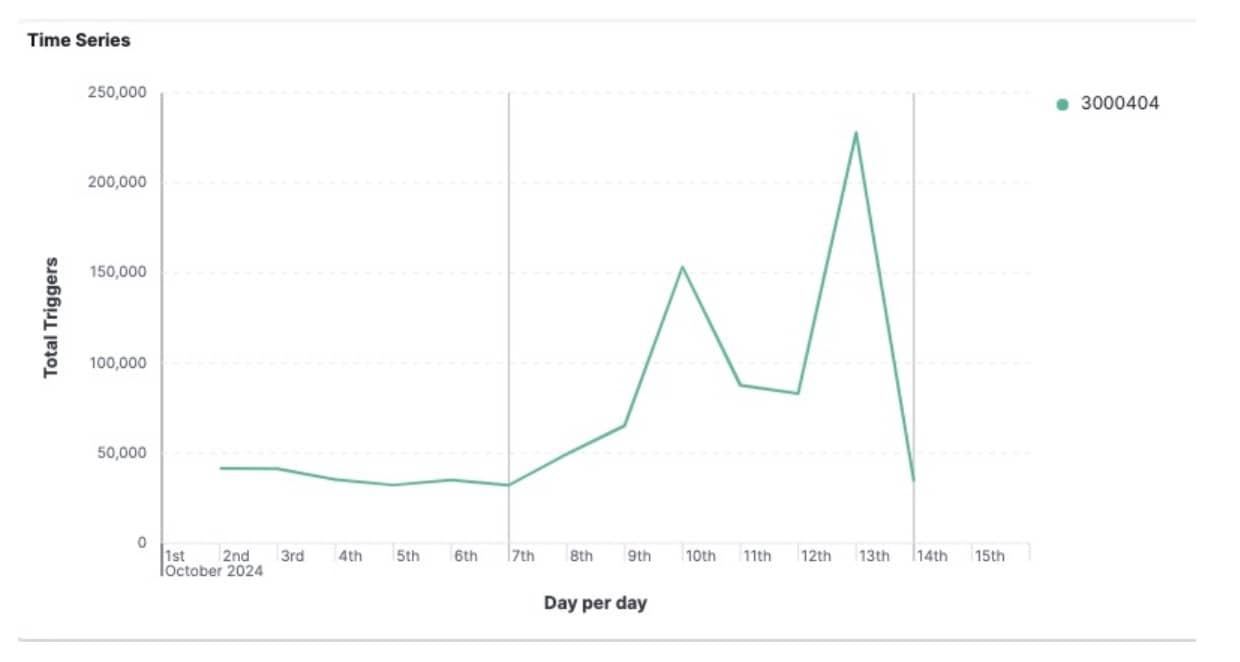
Our new dedicated Rails rule is detecting tens of thousands of Rails code injection attempts on a daily basis worldwide. In recent weeks, this Adaptive Security Engine rule has peaked at nearly 250,000 detections in a single day and averages approximately 70,000 mitigated attacks per day (Figure 2).
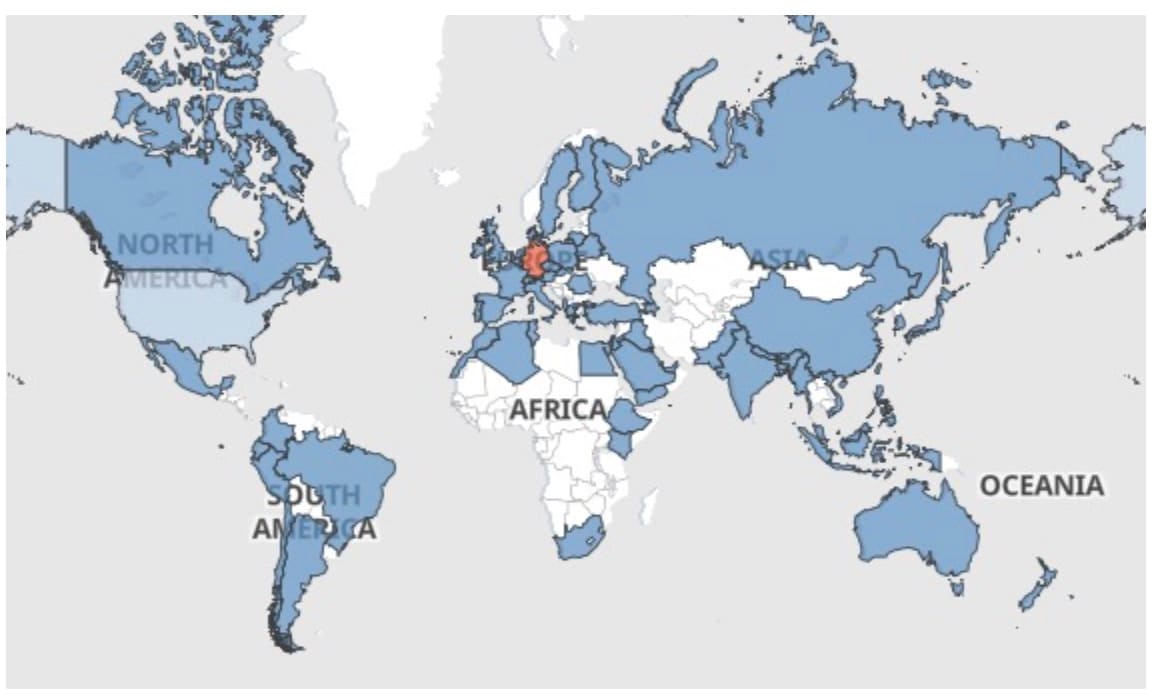
So far, we have observed more than 3,000 unique attacking IPs and over 21,000 hosts targeted by these attack attempts. These attempts have been coming from all over the world; most have originated in Germany (Figure 3).
Looking ahead
Security is a critical aspect of your business, and we are committed to delivering solutions that not only meet but also exceed your expectations. Our WAF is designed to provide comprehensive protection — and the addition of the Rails code injection detection rule further strengthens our defense mechanisms to safeguard your applications and data.
As we continue to innovate and expand our WAF capabilities, we remain focused on providing our customers with the most effective and reliable security solutions. Stay tuned for more updates as we work tirelessly to enhance our product offerings and maintain our position at the forefront of web application security.
To learn more about the Adaptive Security Engine and Akamai's web application and API security solutions, contact your Akamai representative.