Virtually Patch Vulnerabilities with Microsegmentation and Akamai Hunt

In 2022, more than 25,000 new Common Vulnerabilities and Exposures (CVEs) were reported, and that number will only continue to rise in the coming months and years.
In a previous blog post on CVEs, I mentioned that there are many established security solutions on the market for hardening your environment and improving your security posture. But there’s one solution that I’ve yet to mention: virtual patching.
Virtual patching: an overview
When a vulnerability is discovered and reported, it usually takes some time for the source code creators to develop and distribute a patch. During this time, any systems containing the vulnerability are at risk of being exploited, even if you have many of the security solutions outlined. Virtual patching helps you protect yourself while waiting for a “real” patch to be issued.
Sometimes, the source code is unalterable, and the vulnerability simply can’t be patched. In these cases, virtual patching is one of the only ways to ensure that a vulnerability isn’t exploited. The risk still exists, however, as new attack vectors continue to open up and misconfigurations continue to be abused.
For years, the term “virtual patch” was associated with a very specific solution. The term itself was coined by intrusion prevention system (IPS) vendors who, at the time, were selling network-based solutions that operated like web application firewalls (WAFs).
These network-based solutions provided an additional layer of security policy enforcement by analyzing incoming traffic for malicious activity, anomalous traffic, or a predefined policy. Although host-based IPS solutions soon emerged, it meant installing the new software on every host. In an emergency situation, that’s resource-intensive and not particularly scalable.
Network-based solutions: advantages and disadvantages
Network-based solutions offer several benefits, including:
Speed — providing a quick solution for addressing vulnerabilities without altering the source code, which can also work to secure any legacy tech you might still have in your IT stack
Savings — reducing time and money spend by not requiring any kind of emergency patching outside of the typical release timeline
Protection — safeguarding your mission-critical systems without having to take them offline
There can also be downsides to network-based IPS solutions. One disadvantage is the increased strain on your network due to the traffic analysis. Also, the virtual patch might not account for all malicious traffic, leaving parts of your system vulnerable even after deployment.
As attackers become more emboldened and the impact of wide-reaching supply chain vulnerabilities becomes more apparent, we should begin to challenge long-held beliefs about which security solutions we need, and what they should look like. Thinking about multiple alternative methods to achieve the same security goal can foster innovation and help us stay one step ahead of the latest threats.
Virtually patch system vulnerabilities with microsegmentation
One of the ways that we’re addressing these challenges is by enabling quick and effective virtual patching through our host-based microsegmentation solution.
Yes, you read that right. If you’re using Akamai Guardicore Segmentation to segment your network assets, then you can also use it to virtually patch system vulnerabilities. This is one of the primary use cases for Akamai Hunt.
Collect and correlate data with Akamai Hunt
If you’re an Akamai Guardicore Segmentation customer, you already have agents deployed in your network who are enforcing security policy and providing alerts and remediation actions for suspicious or unauthorized traffic. Akamai Hunt is a managed service that leverages the data collected from your segmentation deployment for analysis by security experts from Akamai’s threat intelligence and analytics teams.
With the help of artificial intelligence (AI), Akamai Hunt collects and correlates data from both your environment and Akamai’s global platform to unveil suspicious activity. If something is amiss, Akamai’s specialists send you an alert and share all the insights and information required for mitigation. They also assist with the incident response, guiding the remediation process.
Akamai Hunt in action: researching and remediating Log4j
So, how does this relate to virtual patching? Let’s look at one of the most notorious vulnerabilities in recent memory, Log4Shell — better known as Log4j because of the software it affects — and what occurred for some of our Akamai Hunt customers during that time.
When the Log4j vulnerability was disclosed in early December 2021, experts already knew that the scale of the potential security impact was staggering. Millions of devices run this logging software worldwide, and threat actors were actively leveraging the vulnerability: the security monitoring company Arctic Wolf saw exploitation attempts affect approximately 25% of their customer base.
The Akamai Hunt teams focused their efforts on research and remediation. They knew that our host-based segmentation solution could be used to monitor and block communications with affected assets. But, then, a question arose: how were they going to detect which customer assets were actually vulnerable?
Securing vulnerable assets in four easy steps
Here is their answer: The Hunt team used Akamai solutions to detect and secure vulnerable assets in the following four easy steps.
1. By leveraging Akamai Guardicore Segmentation’s Insight feature, based on osquery, the Hunt team built unique queries to locate all the vulnerable installed packages in customers' environments and scan their process memory to detect risks from unnecessary communications (Figure 1).
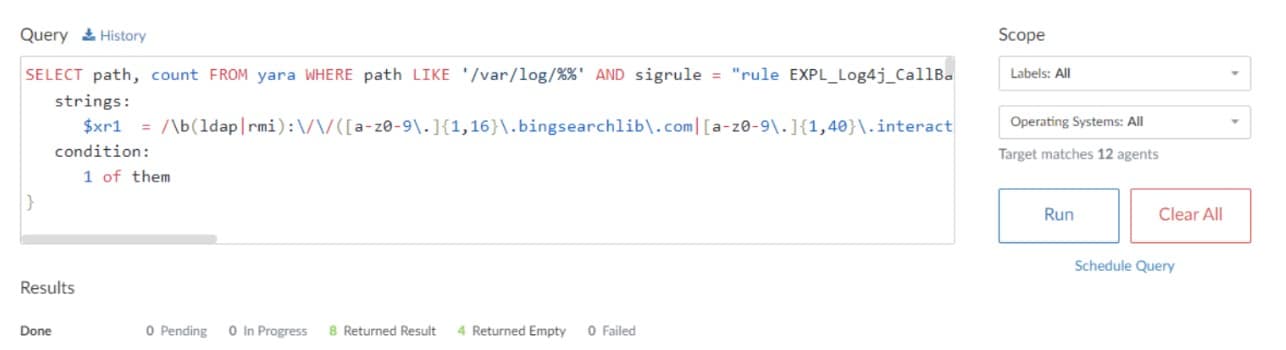 Fig. 1: A portion of the Insight query used to detect vulnerable systems in our customers’ environments
Fig. 1: A portion of the Insight query used to detect vulnerable systems in our customers’ environments
2. The information provided by Insight was fed into Akamai Guardicore Segmentation’s detection engine, determining which machines were vulnerable to attack. Two labels were then created to discern vulnerable machines from invulnerable machines. This allowed the Reveal map to illustrate traffic between our customers’ vulnerable machines, their invulnerable machines, and the internet (Figure 2).
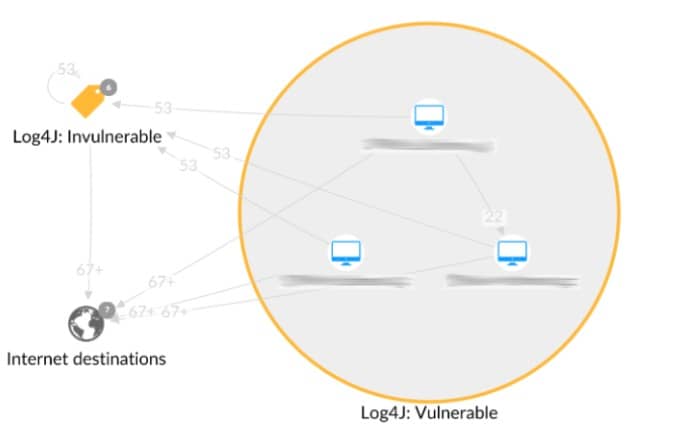 Fig. 2: Visualizing traffic from vulnerable machines in the Reveal map
Fig. 2: Visualizing traffic from vulnerable machines in the Reveal map
3. Through their analysis, the Hunt experts determined which vulnerable machines had been exploited and which were at serious risk of being exploited (Figure 3).
 Fig. 3: Reveal map showing traffic from an active exploit of the Log4Shell vulnerability
Fig. 3: Reveal map showing traffic from an active exploit of the Log4Shell vulnerability
4. Because this was a global crisis, the Hunt team sent a detailed Log4j status report to all Akamai Guardicore Segmentation customers explaining whether they were vulnerable, under active attack, or relatively safe. They followed up with customers who were vulnerable or under active attack, and helped them quickly build and enforce virtual patching policies (Figure 4).
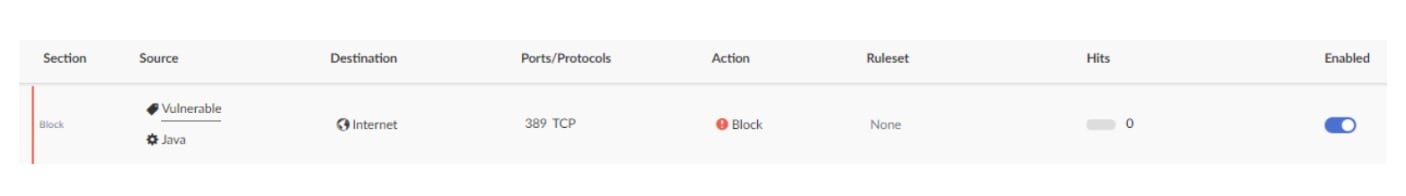 Fig. 4: A virtual patching policy for the affected machines shown in Figure 3
Fig. 4: A virtual patching policy for the affected machines shown in Figure 3
Bolster your defenses
As you can see from the Log4j example, Akamai Guardicore Segmentation along with Akamai Hunt can identify vulnerable assets and act as a sufficient virtual patch in the case of a wide-reaching critical vulnerability. There’s no need to install additional agents or purchase another solution.
This is just one example of how your existing Akamai Guardicore Segmentation deployment can solve additional problems beyond the perceived scope of the solution. With the Hunt experts on your side, this segmentation product becomes an expansion of your security team, bolstering your defenses and making new vulnerabilities that much more manageable.
Find out more
Find out more about what Akamai Hunt can do for you.


